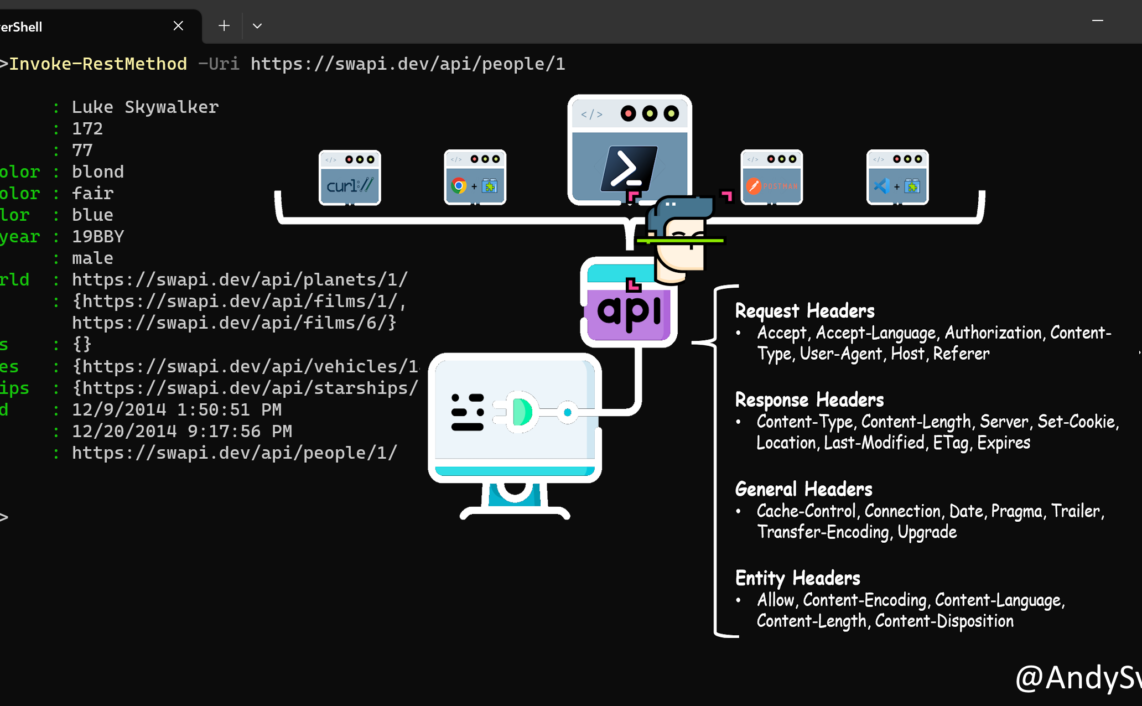
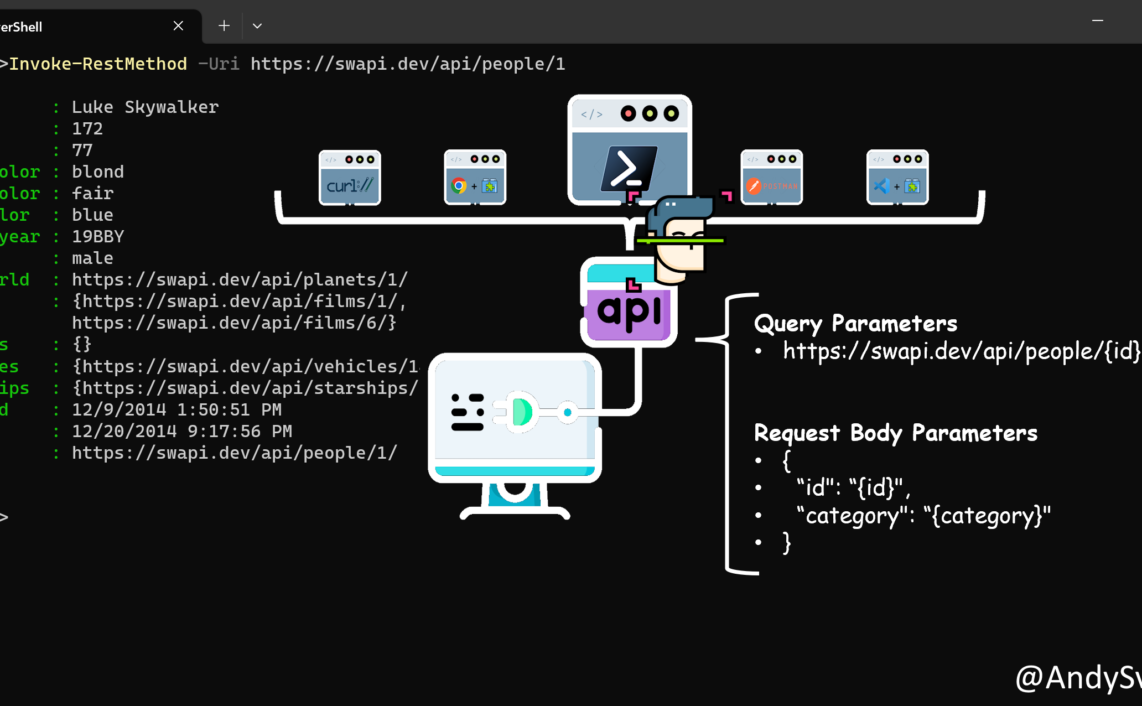
During my preparation to MS-500 exam I generated/gathered bunch of notes, summarizing some specific topics and emphasizing important things. They are in completely random order.
These notes also have been posted on Twitter Thread.
P.S. I did pass MS-500 on November 2020. Here is the link to my Credly account.
Used Resources
- Exam Ref MS-500 Microsoft 365 Security Administration
- Microsoft Learn MS-500 Learning Paths:
My Preparation Notes
Without PHS enabled, you cannot utilize premium features in Azure AD, such as Identity Protection’s leaked credentials detection report.
Azure AD Connect events are logged and found by navigating to Event Viewer > Windows Logs > Application.
SSPR Password Reset settings only applies to your organization’s users, admins always have SSPR.
Identity Governance require Azure AD Premium P2 licensing.
Sign-in security strategy questions:
- Should we have restrictions based on location?
- Do we require MFA for all or some users, and should it also be conditionally required?
- Should certain device characteristics be considered non-compliant?
You won’t be able to benefit from Security Defaults, If you plan on utilizing conditional access policies.
Conditional access policies are the recommended way of enforcing MFA.
In order to implement Windows Hello for SSO, devices must first be joined to Azure AD and Intune-enrolled.
Compliance and conditional access policies design questions:
- What characteristics determine compliant devices? (These could include OS version and build and mobile passcode requirements.)
- What policies exist in your organization that need to be incorporated into the compliance and conditional access policies somehow?
- What sign-in activity would be risky for users in your organization (such as foreign location sign-ins when users typically don’t travel outside the country)?
RBAC roles assignments and are additive in nature, meaning that multiple allow assignments result in the sum of their allowances for the user they’re applied to.
Deny RBAC role assignment overrides any Allow assignment.
In order to use PIM, you must have an Azure AD Premium P2, Microsoft 365 M5, or Enterprise Mobility + Security (EMS) E5 license.
PIM planning questions:
- Should granting privileged roles be subject to approval?
- How could JIT access requests improve current practices?
- Which roles should be re-evaluated and possibly put under an access review?
Planning an Azure Advanced Threat Protection (ATP):
- For the best performance, your domain controllers should have enough RAM to cache the entire NTDS.DIT in memory on top of the operating system requirements and any other software running on the domain controllers
- if there is not enough RAM on the domain controller
Deploying the Azure ATP Standalone sensor has pros and cons. The pros include not needing to deploy additional software to domain controllers to upgrade their hardware and that the out-of-band deployment can make it harder for an adversary to detect. The cons include the additional cost, the need for a mirror port, and that you lose the ability to directly capture ETW events on the domain controller, which are necessary for certain detections, including LDAP-based reconnaissance. You can get around this by configuring event forwarding from domain controllers to the standalone sensor, but that does increase the complexity of your deployment.
Once Azure ATP is installed, all authentication is through certificates.
Any user who is a Global Administrator or a Security Administrator is automatically an Azure ATP Administrator.
Azure ATP Workspace Health reports issues such as connectivity, disconnected sensors, or service account authentication.
While you can protect servers using Microsoft Defender ATP, the licenses included in Microsoft 365 E5 and Windows E5 only cover the Windows workstation products. To protect servers, you must onboard them to the Azure Security Center, which charges based on a consumption model.
Anything that Microsoft Defender ATP detects is tracked as an incident.
Off boarding scripts must be refreshed every 30 days and that their file name includes the “use by” date.
Secure Boot sequence:
- When the PC first boots (or is rebooted), signature databases are each checked against the platform key to ensure that the firmware is valid.
- If the firmware is not valid, UEFI firmware initiates an OEM-specific recovery process (boot menu) to restore a trusted firmware, usually from a USB key. However, if all is well, the machine proceeds to the next step.
- The Windows Boot Manager is checked against the database. If it fails, the firmware should boot from a backup copy of Windows Boot Manager. If this fails as well, the firmware initiates an OEM-specific recovery process.
- Once Windows Boot Manager is running, drivers are checked as they are loaded. If any fail to have a valid signature, the Windows Recovery Environment (Windows RE) is loaded, so you can begin a repair or recovery process. However, if all goes well, the machine proceeds to the next step.
- Windows loads the installed antimalware software (Windows Defender AV or third-party antivirus applications) that registered with Windows Security.
- Windows finishes loading the other kernel drivers and then initializes the user mode processes.
If you want to change Secure Boot from on to off or vice versa, you will need to reinstall the operating system after you make the change.
Azure AD joined machines will automatically encrypt drives and store the recovery keys in Azure AD.
Mobile Device Management is used for company-owned devices, and Mobile Application Management (MAM) is used to secure the application and enable secure access even when supporting a Bring Your Own Device (BYOD) environment.
Windows Information Protection (WIP) is the MAM mechanism for Windows 10 devices.
SharePoint Online, OneDrive for Business, Microsoft Teams, and Office 365 ProPlus all benefit from the protections provided by Office 365 ATP.
It is recommended that you have only one production anti-phishing policy for your organization that applies equally to all users, unless you have very specific reasons to treat different users or groups differently.
O365 ATP service can automatically remove messages that were previously delivered to Exchange Online mailboxes using the Zero-Hour Auto Purge (ZAP) feature.
Azure Sentinel does not cost anything when data is ingested from Office 365 audit logs, Azure activity logs, and from Microsoft Threat Protection solutions.
Azure Sentinel can use a charge-as-you-go or a pre-commit model.
Azure Sentinel significant discounts start at 100GB per day and move up to 500GB per day.
You do not get a credit for data under the chosen tier, so monitor your volume each month.
Microsoft allows you to change tiers each month as your needs change, moving up or down as you need.
BitLocker requires a TPM version 1.2 or later chip.
Administrators can use the Threat Explorer/Threat Tracker to view what is going on across the Internet that is related to new attacks.
Baseline Protection, which includes standard permissions barriers and basic security configurations.
Sensitive Protection is useful for organizations that need to more strictly secure a subset of data in their environments, and it’s probably useful for users who are accessing that sensitive data at an elevated level.
Highly Confidential Protection is a small customer base that requires advanced protection options including encryption, Bring-Your-Own-Key (BYOK) scenarios, disabled external sharing, and more.
Organization-wide sharing settings for SharePoint also apply to OneDrive. Any settings made at the tenant level cannot be overwritten to be less restrictive at individual site levels, but they could be made more restrictive.
AIP integrates with Exchange Online (automatically enabled in new tenants), SharePoint, and OneDrive for Business.
DLP: multiple actions could be taken for the same activity, depending on policy configuration.
DLP policies are what power the active monitoring of your environment for potential data loss.
Microsoft Cloud App Security (CAS) is licensed per-user.
Microsoft CAS includes Office 365 CAS and does not require an Office 365 subscription.
Because external user activity isn’t monitored like your internal users, you’ll want to be sure all domains you manage are included for the most accurate insight into your CAS environment.
By monitoring matches and alerts, you’ll be better able to fine-tune policies to catch helpful and relevant information and find fewer false positives.
Reporting and auditing are critical security features that are vital for enforcing governance and ensuring compliance.
Secure Score helps you to:
- Evaluate the current state of your security posture
- Identify ways to improve your security posture
- Compare your posture with benchmarks and KPIs
Auditing of administrative actions is enabled in Office 365 by default.
Unified audit log retains data for 90 days. Download the audit logs or import them into Azure Log Analytics for longer retention.
Audit logging is not intended to be used to perform troubleshooting or real-time alerting. It is intended to provide a record of actions that were taken.
Organizations might need to identify and classify certain data as records, which indicates the data not only must be retained but that it cannot be modified.
It can take up to an hour before the policy is available to users.
Data governance helps you keep what you want and get rid of what you don’t.
Retention policies help to ensure that data is maintained for the required period of time and can make that data immutable when necessary.
Data can only be tagged with one retention label.
Manual labels take precedence over automatic labels, and the longest retention period takes precedence over shorter retention periods.
Holds have no defined end date. Data is held until you remove or delete the hold.
Content searches are typically ad hoc, where data needs to be found because you are trying to assess the state of things, you are looking for data that might be sensitive or needs protection, or you have a one-off need.
eDiscovery is most often used for specific requirements and when the results of the search must be preserved, typically in response to a search warrant, discovery motion, or because you wish to pursue legal action and must preserve the results as evidence of wrong-doing.
While GDPR does provide EU residents with the right to be forgotten, litigation holds or the retention of data necessary to meet other compliance requirements or regulations make take precedence over this.
MFA for users is prerequisites for running Microsoft Office 365 Attack simulator.
Thanks a lot for reading.