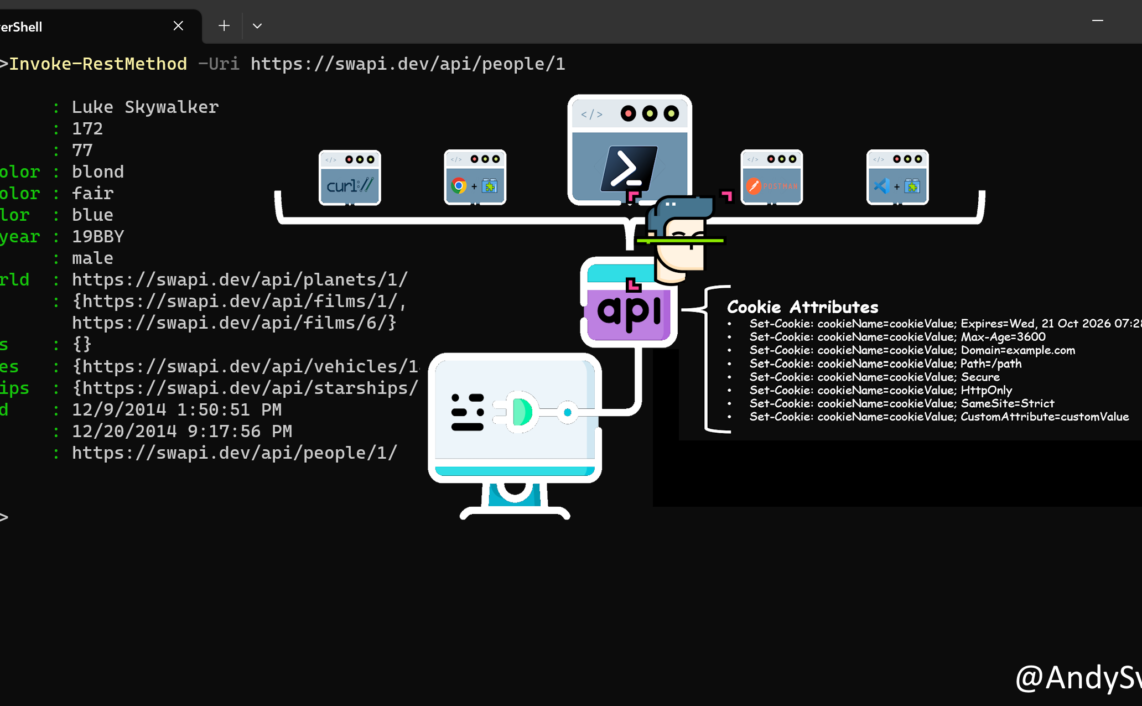
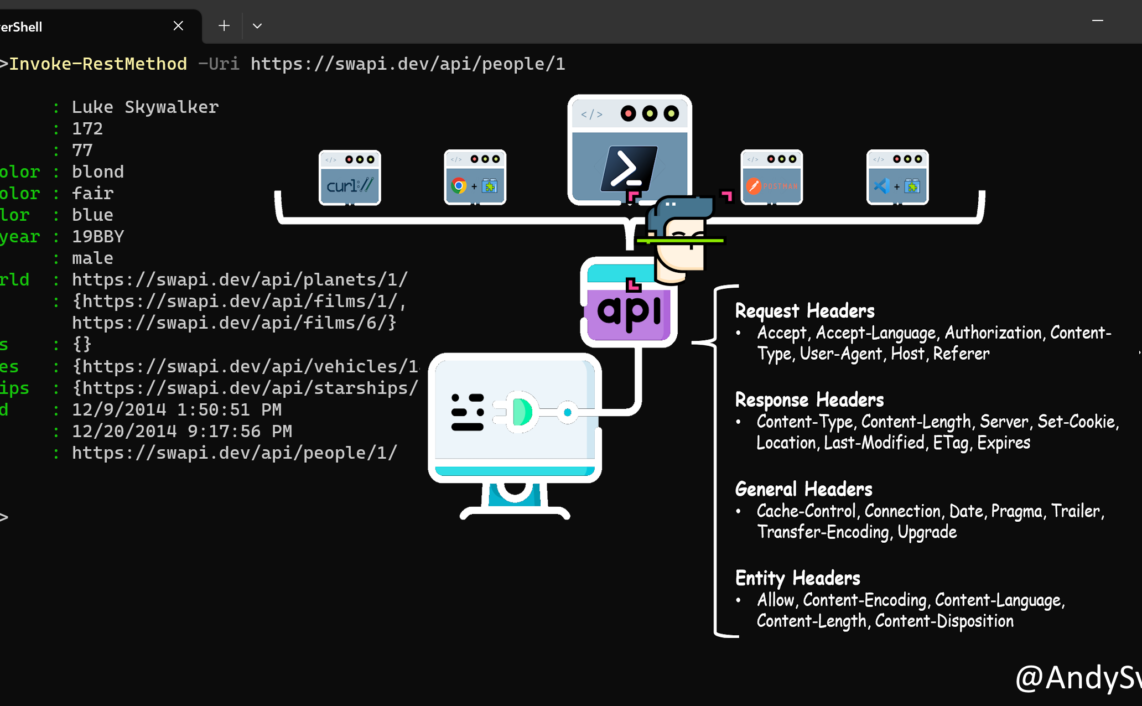
During my preparation to Az-500 exam I generated/gathered bunch of notes, summarizing some specific topics and emphasizing important things. They are in completely random order.
These notes also have been posted on Twitter Thread.
P.S. I did pass AZ-500 on February 2020. Here is the link to my Credly account.
Used Resources
- Azure-AZ-500-Study-Guide by @AzureMentor
- AZ-500-Azure-Security Labs by Microsoft Learning
My Preparation Notes
The Microsoft identity platform endpoint allows work and school accounts from Azure AD and personal Microsoft accounts, such as hotmail.com, outlook.com and msn.com to sign in.
The v1.0 endpoint allows only work and school accounts to sign in to your application (Azure AD).
The Microsoft identity platform endpoint does not support SAML or WS-Federation.
For delegated permissions, the effective permissions of your app will be the least privileged intersection of the delegated permissions the app has been granted (via consent) and the privileges of the currently signed-in user.
For application permissions, the effective permissions of your app will be the full level of privileges implied by the permission.
The remember Multi-Factor Authentication feature is not compatible with B2B users and will not be visible for B2B users when signing into the invited tenants.
Authentication Administrator can require users to reset their password, re-register for MFA, or revoke existing MFA sessions from their user object.
Delete users existing app passwords requires Global Admin permissions
Azure Active Directory (Azure AD) groups can be managed by group owners instead of IT administrators. Known as self-service group management, this feature allows group owners who are not assigned an administrative role to create and manage security groups.
Self-service group management is available only for Azure AD security and Office 365 groups. It is not available for mail-enabled groups, distribution lists, or any group that has been synchronized from your on-premises Active Directory Domain Services (AD DS).
When Users can create groups is enabled, all users in your tenant are allowed to create new groups and add members to these groups.
You should not configure group-based licensing for groups that contain Azure business to business (B2B) accounts.
You’ll need an Azure AD Premium P1 license for each unique user that is a member of one or more dynamic groups.
Application Administrator – Can add and manage enterprise applications and application registrations, and configure proxy application settings. Application Administrators can view Conditional Access policies and devices, but not manage them.
Cloud Application Administrator – Can add and manage enterprise applications and enterprise app registrations. This role has all of the permissions of the Application Administrator, except it can’t manage application proxy settings.
Application Developer – Can add and update application registrations, but can’t manage enterprise applications or configure an application proxy.
Azure AD paid licenses are built on top of your existing free directory, providing self-service, enhanced monitoring, security reporting, and secure access for your mobile users.
Azure Active Directory Free
Provides user and group management, on-premises directory synchronization, basic reports, self-service password change for cloud users, and single sign-on across Azure, Office 365, and many popular SaaS apps.
Azure Active Directory Premium P1
In addition to the Free features, P1 also lets your hybrid users access both on-premises and cloud resources. It also supports advanced administration, such as dynamic groups, self-service group management, Microsoft Identity Manager (an on-premises identity and access management suite) and cloud write-back capabilities, which allow self-service password reset for your on-premises users.
Azure Active Directory Premium P2
In addition to the Free and P1 features, P2 also offers Azure Active Directory Identity Protection to help provide risk-based Conditional Access to your apps and critical company data and Privileged Identity Management to help discover, restrict, and monitor administrators and their access to resources and to provide just-in-time access when needed.
“Pay as you go” feature licenses
You can also get additional feature licenses, such as Azure Active Directory Business-to-Customer (B2C). B2C can help you provide identity and access management solutions for your customer-facing apps.
Azure AD custom roles support assignments on a per-resource basis, in addition to the more traditional organization-wide assignments. This approach gives you the ability to grant access to manage some resources (for example, one app registration) without giving access to all resources (all app registrations).
Granting permission using custom Azure AD roles is a two-step process that involves:
- creating a custom role definition
- assigning it using a role assignment.
The same role can be assigned to one user over all applications in the organization and then to another user with a scope of only the Contoso Expense Reports app.
Azure RBAC controls access to Azure resources such as virtual machines or storage using Azure Resource Management, and Azure AD custom roles control access to Azure AD resources using Graph API.
Role assignment consists of three elements:
- User (an individual who has a user profile in Azure Active Directory)
- Role definition
- Resource scope
A role definition lists the operations that can be performed on Azure AD resources, such as create, read, update, and delete.
For Azure AD roles in Privileged Identity Management, only a user who is in the Privileged Role Administrator role can manage assignments for other administrators.
There’s no difference in the access given to someone with a permanent versus an eligible role assignment. The only difference is that some people don’t need that access all the time.
When an Application Developer creates a new application registration, they are automatically added as the first owner.
An enterprise application can have many owners, and a user can be the owner for many enterprise applications.
The first person to use Azure AD Privileged Identity Management in your tenant is automatically assigned the Security administrator and Privileged role administrator roles in the tenant.
Only privileged role administrators can manage the Azure AD directory role assignments of users.
Identity Protection requires users be a Security Reader, Security Operator, Security Administrator, Global Reader, or Global Administrator in order to access.
Each subscription can have a different billing and payment setup, so you can have different subscriptions and different plans by office, department, project, and so on. Every service belongs to a subscription.
Only the Azure portal and the Azure Resource Manager APIs support RBAC. Users, groups, and applications that are assigned RBAC roles cannot use the Azure classic deployment model APIs.
If you are a member of the Global Administrator role, you have global administrator capabilities in Azure AD and Office 365, such as making changes to Microsoft Exchange and Microsoft SharePoint. However, by default, the Global Administrator doesn’t have access to Azure resources.
All objects you want to synchronize must be a direct member of the group. Users, groups, contacts, and computers/devices must all be direct members. Nested group membership is not resolved.
There’s another benefit to deploying password hash synchronization in addition to pass-through authentication. It acts as a backup authentication method when the primary authentication method is no longer available. Fail over to password hash synchronization doesn’t happen automatically and you must use Azure AD Connect to switch the sign-on method manually.
Microsoft currently only has about 10 administrators with the Global Administrator role.
Microsoft recommends you have zero permanently active assignments for both Azure AD roles and Azure resource roles other than the recommended two break-glass emergency access accounts, which should have the permanent Global Administrator role.
For each paid Azure AD Premium P2 license that you assign to one of your own organization’s users, you can use Azure AD business-to-business (B2B) to invite up to five guest users under the External User Allowance. These guest users can also use Azure AD Premium P2 features.
If you move the subscription to the new account’s Azure AD tenant, all role-based access control (RBAC) assignments to manage resources in the subscription are permanently removed.
Azure API Management gateway is the endpoint that:
- Accepts API calls and routes them to your backends.
- Verifies API keys, JWT tokens, certificates, and other credentials.
- Enforces usage quotas and rate limits.
- Transforms your API on the fly without code modifications.
- Caches backend responses where set up.
- Logs call metadata for analytics purposes.
When connecting VNets from different subscriptions, the subscriptions do not need to be associated with the same Active Directory tenant.
If you update the address space for one VNet, the other VNet automatically knows to route to the updated address space.
You must use separate PowerShell sessions when configuring the connections for VNets that reside in different subscriptions.
Always name your gateway subnet specifically GatewaySubnet. If you name it something else, your gateway creation fails.
Create and configure VNet in Azure via Powershell
- Create a resource group.
- Create the subnet configurations
- Create VNet
- Request a public IP address
- Create the gateway configuration
- Create the VNet gateway (can often take 45 minutes or more)
VNet-to-VNet traffic travels across the Microsoft Azure backbone, not the internet.
All resources in a VNet can communicate outbound to the internet, by default.
Network security groups are processed after Azure translates a public IP address to a private IP address for inbound traffic, and before Azure translates a private IP address to a public IP address for outbound traffic.
You only need to specify an inbound security rule if communication is initiated externally. The opposite is also true. If inbound traffic is allowed over a port, it’s not necessary to specify an outbound security rule to respond to traffic over the port.
You cannot remove the default rules, but you can override them by creating rules with higher priorities.
Security rules in an NSG associated to a subnet can affect connectivity between VM’s within it.
Hub and spoke model
The hub is a virtual network in Azure that acts as a central point of connectivity to your on-premises network. The spokes are virtual networks that peer with the hub, and can be used to isolate workloads.
Azure Storage firewall
Be sure to set the default rule to deny, or network rules have no effect.
Database-level IP firewall rules can only be configured through Transact-SQL.
An action group is a group of actions that you can use across multiple alerts.
Kubernetes environments, in AKS or elsewhere, currently aren’t completely safe for hostile multi-tenant usage. Additional security features such as Pod Security Policies or more fine-grained role-based access controls (RBAC) for nodes make exploits more difficult.
Secrets are stored within a given namespace and can only be accessed by pods within the same namespace.
The raw secret manifest files contains the secret data in base64 format.
For registry access, the token used by az acr login is valid for 3 hours, so we recommend that you always log in to the registry before running a docker command.
Each container registry includes an admin user account, which is disabled by default.
Limiting containers so they can access or run only preapproved or safelisted files and executables is a proven method of limiting exposure to risk.
When you apply a lock at a parent scope, all resources within that scope inherit the same lock. Even resources you add later inherit the lock from the parent. The most restrictive lock in the inheritance takes precedence.
Thanks a lot for reading.