Welcome to the weekly digest about the Cybersecurity & Threats in the wild.
Below you will find a very subjective summary of Cybersecurity events for the prior week.
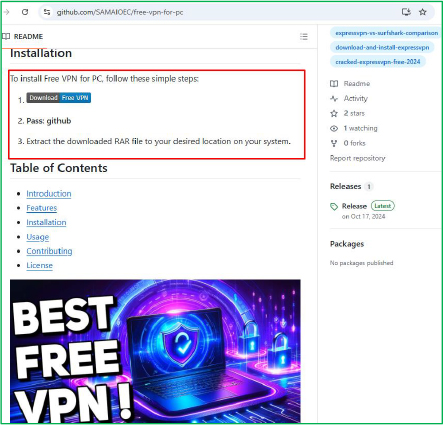
1.GitHub Abused to Spread Malware Disguised as Free VPN by @CyfirmaR
- GitHub-hosted malware campaign in which threat actors disguised malicious payloads as “Free VPN for PC” & “Minecraft Skin Changer”
- these lures are designed to attract users seeking free software and trick them into executing a malware dropper named Launch.exe
https://www.cyfirma.com/research/github-abused-to-spread-malware-disguised-as-free-vpn/
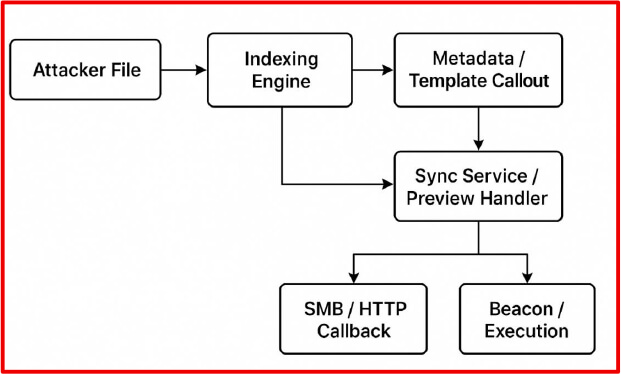
2.RENDERSHOCK: WEAPONIZING TRUST IN FILE RENDERING PIPELINES by @CyfirmaR
- comprehensive zero-click attack strategy that targets passive file preview, indexing, and automation behaviours in modern operating systems and enterprise environments
- leverages built-in trust mechanisms and background processing in file systems, email clients, antivirus tools, and graphical user interfaces to deliver payloads without requiring any user interaction
https://www.cyfirma.com/research/rendershock-weaponizing-trust-in-file-rendering-pipelines/
3.OCTALYN STEALER UNMASKED by @CyfirmaR
- consists of a C++-based payload module supported by Delphi-based builder interface, which simplifies payload generation and allows even low-skilled actors to produce fully functional binaries with minimal effort.
- builder requires only Telegram bot token and chat ID to configure payload capable of real-time data exfil via Telegram
https://www.cyfirma.com/research/octalyn-stealer-unmasked/
4. BERT Ransomware Group Targets Asia and Europe on Multiple Platforms by @TrendMicro
- newly emerged ransomware group targeting both Windows & Linux platforms, with confirmed victims in Asia, Europe, and the US, particularly across healthcare, technology, and event services sectors
- group’s tactics include PowerShell-based loaders, privilege escalation, and concurrent file encryption, allowing them streamlined attack execution and evasion despite their reliance on a simple codebase
5. GoldMelody’s Hidden Chords: Initial Access Broker In-Memory IIS Modules Revealed by #PaloAlto’s #Unit42
- group seems to follow opportunistic approach but has attacked organizations in Europe & U.S. in the following industries: financial services, manufacturing, wholesale and retail, high technology, and transportation and logistics
- IAB used these leaked keys to sign malicious payloads that provide unauthorized access to targeted servers, in a technique called ASP.NET View State deserialization
https://unit42.paloaltonetworks.com/initial-access-broker-exploits-leaked-machine-keys/
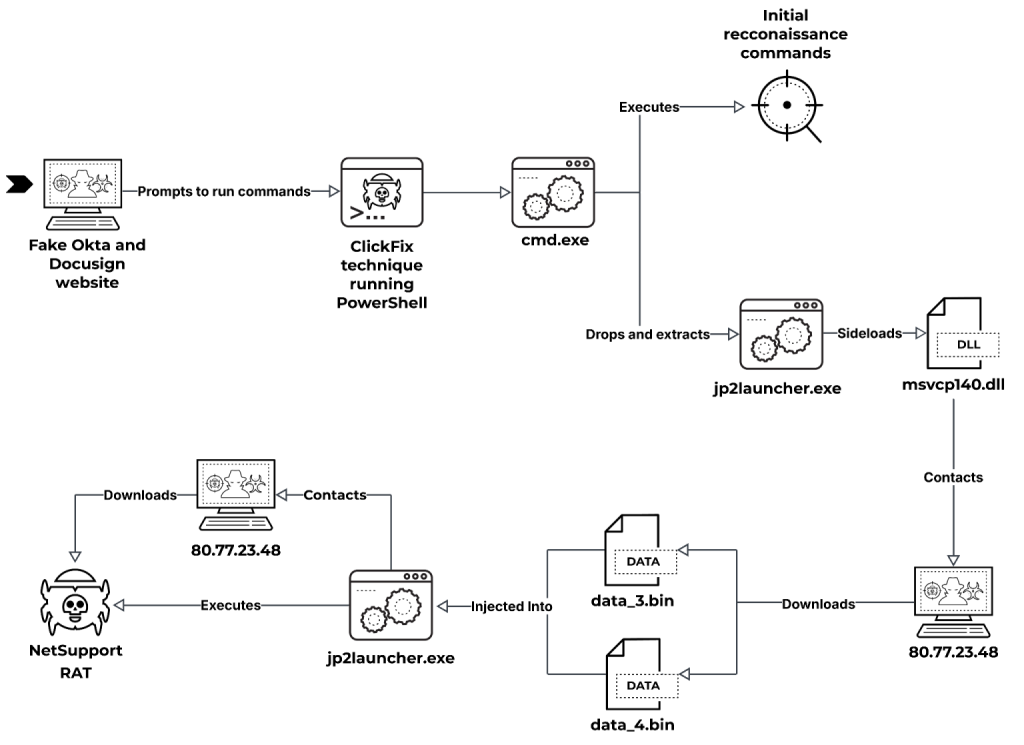
6.Fix the Click: Preventing the ClickFix Attack Vector by #PaloAlto’s #Unit42
- inside view of some of the most prominent ClickFix campaigns in 2025 so far)
- attackers distributing NetSupport RAT are ramping up activities with new loader
- attackers distributing Latrodectus malware are luring victims with new ClickFix campaign
- prolific Lumma Stealer campaign targeting multiple industries with new techniques
https://unit42.paloaltonetworks.com/preventing-clickfix-attack-vector/
7.Evolving Tactics of SLOW#TEMPEST: A Deep Dive Into Advanced Malware Techniques by #PaloAlto’s #Unit42
- analyze more recent variant of malware sample from SLOW#TEMPEST campaign
- attackers distribute malware as ISO file, which is common technique used to bundle multiple files to potentially evade initial detection
- ISO file contains 11 files; 2 are malicious, and remainder are benign
https://unit42.paloaltonetworks.com/slow-tempest-malware-obfuscation/
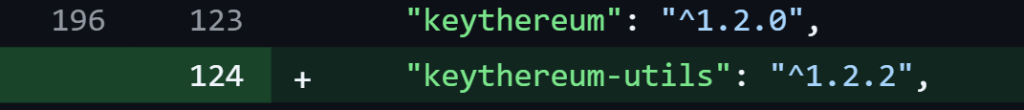
8.Malicious pull request infects VS Code extension by @ReversingLabs
- ETHcode is VS Code extension developed and maintained by 7finney, small GitHub orgs that develops tools related to Ethereum blockchain platform
- analysis of this malicious campaign is ongoing, and updates will continue to be shared with the community via RL Blog
https://www.reversinglabs.com/blog/malicious-pull-request-infects-vscode-extension
9.NordDragonScan: Quiet Data-Harvester on Windows by #FORTIGUARD LABS
- active delivery site that hosts weaponized HTA script and silently drops the infostealer “NordDragonScan” into victims’ environments
- once installed, NordDragonScan examines host and copies documents, harvests entire Chrome & Firefox profiles, and takes screenshots
- package is then sent over TLS to its command-and-control server, “kpuszkiev.com,” which also serves as heartbeat server to confirm victim is still online and to request additional data when needed
https://www.fortinet.com/blog/threat-research/norddragonscan-quiet-data-harvester-on-windows
10.macOS.ZuRu Resurfaces | Modified Khepri C2 Hides Inside Doctored Termius App by @SentinelOne
- recent sample uses new method to trojanize legitimate apps as well as modified Khepri beacon
- technical analysis of this latest version of malware along with new technical indicators to aid detection engineers & threat hunters
11.Wing FTP Server Remote Code Execution (CVE-2025-47812) Exploited in the Wild by @HuntressLabs
- CVE-2025-47812 is null byte and Lua injection flaw that can lead to root/SYSTEM-level remote code execution if exploited
- vulnerability was first publicly disclosed on June 30 by Julien Ahrens in versions prior to 7.4.4 of Wing FTP Server, its file transfer protocol software for Windows, Linux, and macOS
https://www.huntress.com/blog/wing-ftp-server-remote-code-execution-cve-2025-47812-exploited-in-wild
Thanks a lot for reading.
Please add interesting items you came across during the week in the comments below.