Welcome to the weekly digest about the Cybersecurity & Threats in the wild.
Below you will find a very subjective summary of Cybersecurity events for the prior week.
1.Gunra Ransomware – A Brief Analysis by @CyfirmaR
- Gunra ransomware targets various industries globally, including real estate, pharmaceuticals & manufacturing
- employs double-extortion technique by threatening to leak stolen data on its Tor-hosted extortion
- exhibits several malicious behaviours such as enumerating running processes, deleting shadow copies via WMI & retrieving system info
https://www.cyfirma.com/research/gunra-ransomware-a-brief-analysis/

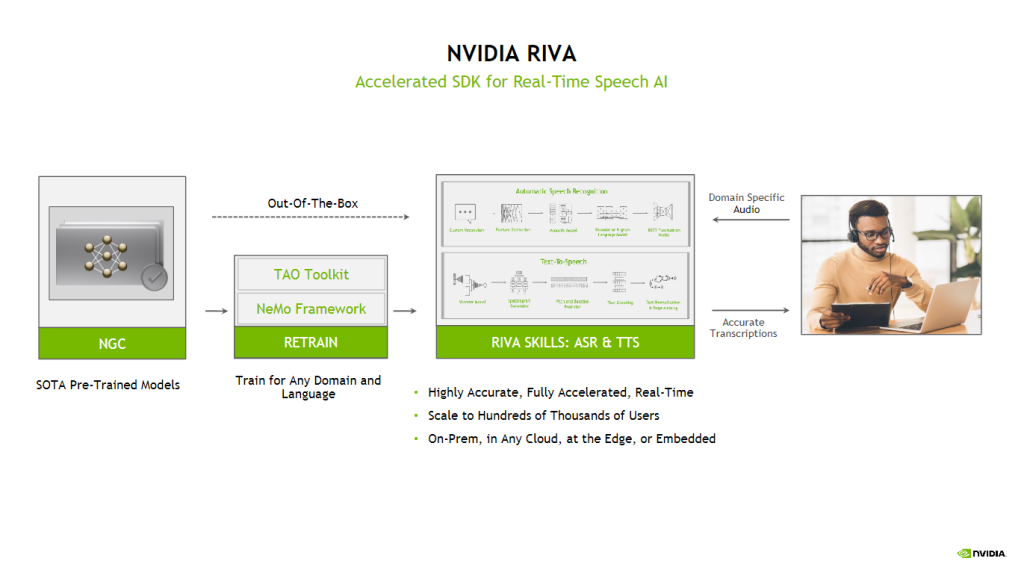
2.NVIDIA Riva Vulnerabilities Leave AI-Powered Speech and Translation Services at Risk by @TrendMicro
- misconfigured Riva deployments enable unauthorized access, allowing attackers to abuse GPU resources & API keys without restriction
- exposed APIs increase risk of data leakage, DoS attacks & system disruptions
- orgs running AI-powered services with proprietary models could be at risk of intellectual property theft, particularly if their models or inference services are exposed via misconfigured APIs
https://www.trendmicro.com/en_us/research/25/d/nvidia-riva-vulnerabilities.html
3. Earth Kasha Updates TTPs in Latest Campaign Targeting Taiwan and Japan by @TrendMicro
- APT group Earth Kasha continues its activity with new campaign in Mar 2025 that uses spear-phishing to deliver new version of ANEL backdoor, possibly for espionage based on campaign’s victimology
- ANEL file from 2025 campaign implemented new command to support execution of BOF in memory
- campaign also leveraged SharpHide to launch 2nd stage backdoor NOOPDOOR
https://www.trendmicro.com/en_us/research/25/d/earth-kasha-updates-ttps.html
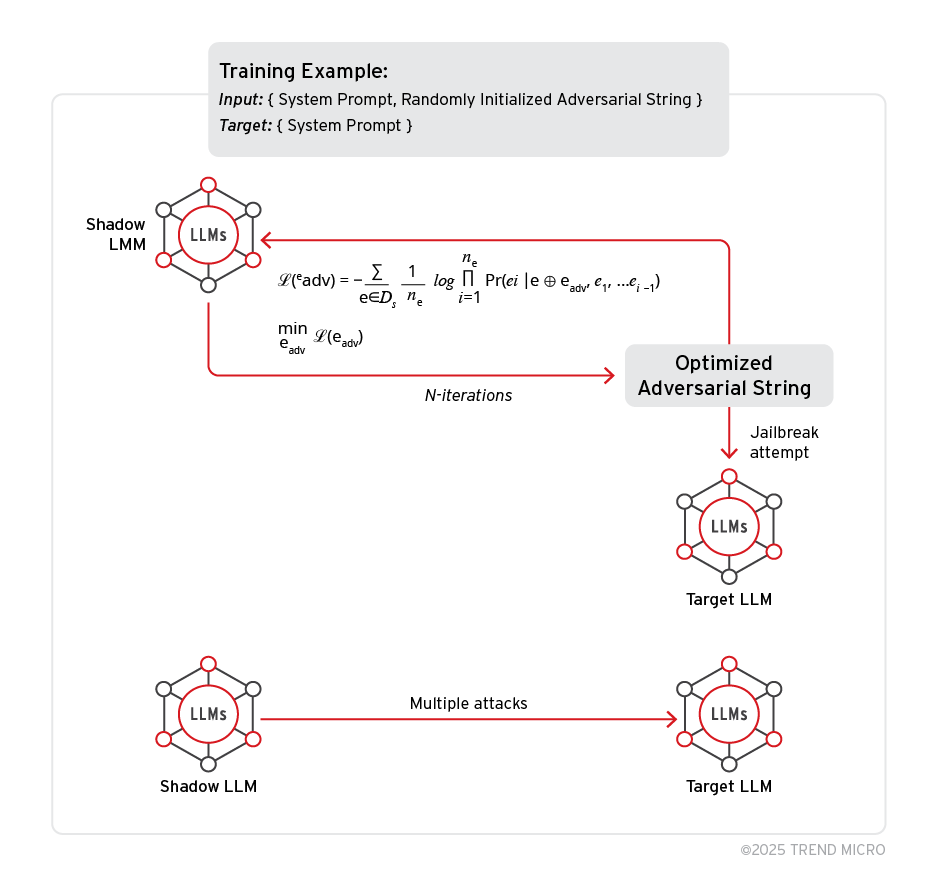
4. Exploring PLeak: An Algorithmic Method for System Prompt Leakage by @TrendMicro
- deep dive into concept of Prompt Leakage (PLeak) by developing strings for jailbreaking system prompts, exploring its transferability, and evaluating it through a guardrail system
- PLeak could allow attackers to exploit system weaknesses, which could lead to exposure of sensitive data such as trade secrets
https://www.trendmicro.com/en_us/research/25/e/exploring-pleak.html
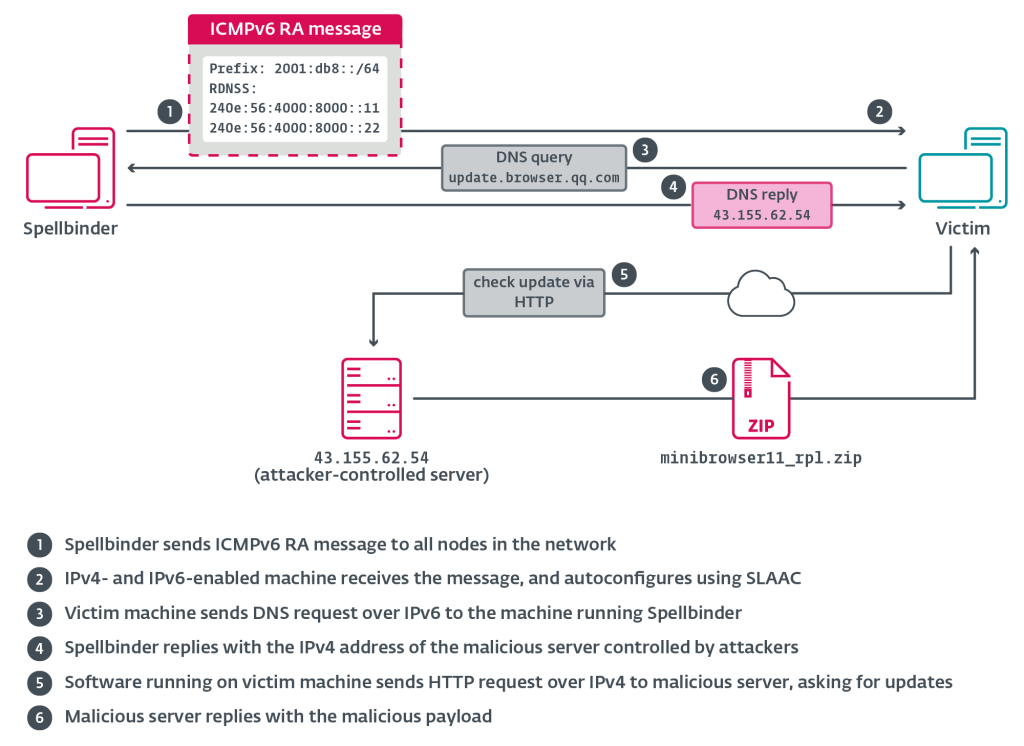
5. TheWizards APT group uses SLAAC spoofing to perform adversary-in-the-middle attacks by @ESETresearch
- discovered malicious downloader being deployed, by legitimate Chinese software update mechanisms, onto victims’ machines
- downloader seeks to deploy modular backdoor – WizardNet
- analyzed Spellbinder: tool attackers use to conduct local adversary-in-the-middle attacks and to redirect traffic to attacker-controlled server to deliver group’s signature backdoor WizardNet
6.Gremlin Stealer: New Stealer on Sale in Underground Forum by #PaloAlto’s #Unit42
- new information-stealing malware written in C#, called Gremlin Stealer
- stealer’s authors have actively advertised it on Telegram group since mid-March 2025
- can capture data from browsers, the clipboard and the local disk to steal sensitive data such as credit card details, browser cookies, crypto wallet information, File Transfer Protocol (FTP) and virtual private network (VPN) creds
https://unit42.paloaltonetworks.com/new-malware-gremlin-stealer-for-sale-on-telegram/
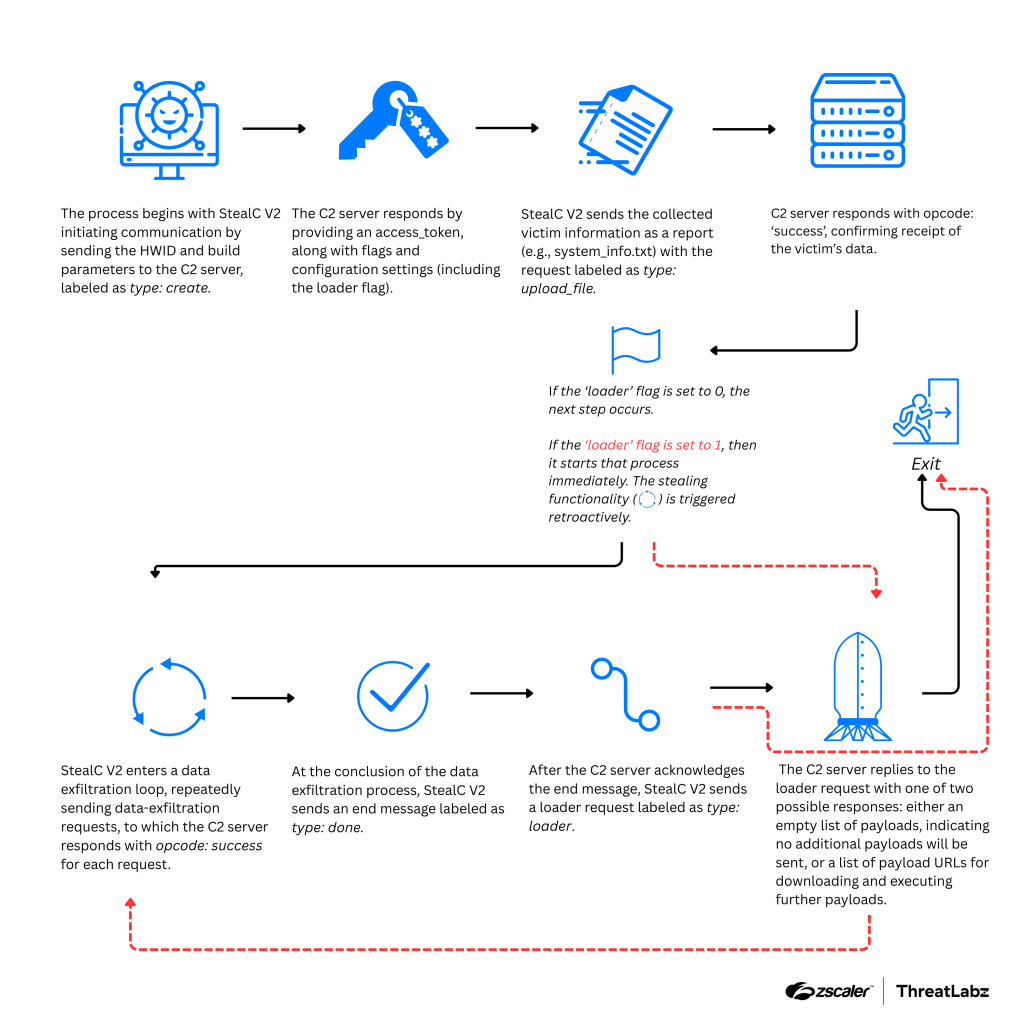
7.I StealC You: Tracking the Rapid Changes To StealC by @Threatlabz
- StealC V2, introduced in Mar 2025, utilizes JSON-based network protocol with RC4 encryption implemented in recent variants
- StealC V2 now supports loader options that can deliver MSI packages & PowerShell scripts.
https://www.zscaler.com/blogs/security-research/i-stealc-you-tracking-rapid-changes-stealc
8.DragonForce Ransomware Gang | From Hacktivists to High Street Extortionists by @SentinelOne
- DragonForce’s large-scale cartel model is not 1st of its kind, its current successes and the recent demise of rival operations suggest that it will become increasingly attractive both to orphaned ransomware actors and more resourced groups looking to thrive in increasingly competitive space.
9. MCP: Untrusted Servers and Confused Clients, Plus a Sneaky Exploit by @wunderwuzzi23
- MCP supports three capabilities: tools, resources, and prompts.
- Tool calling has its inherent dangers, regardless of the implementation details, be it OpenAPI, AI Actions or MCP – they all suffer from prompt injection and confused deputy threats.
https://embracethered.com/blog/posts/2025/model-context-protocol-security-risks-and-exploits/
Thanks a lot for reading.
Please add interesting items you came across during the week in the comments below.