Welcome to the weekly digest about the Cybersecurity & Threats in the wild.
Below you will find a very subjective summary of Cybersecurity events for the prior week.
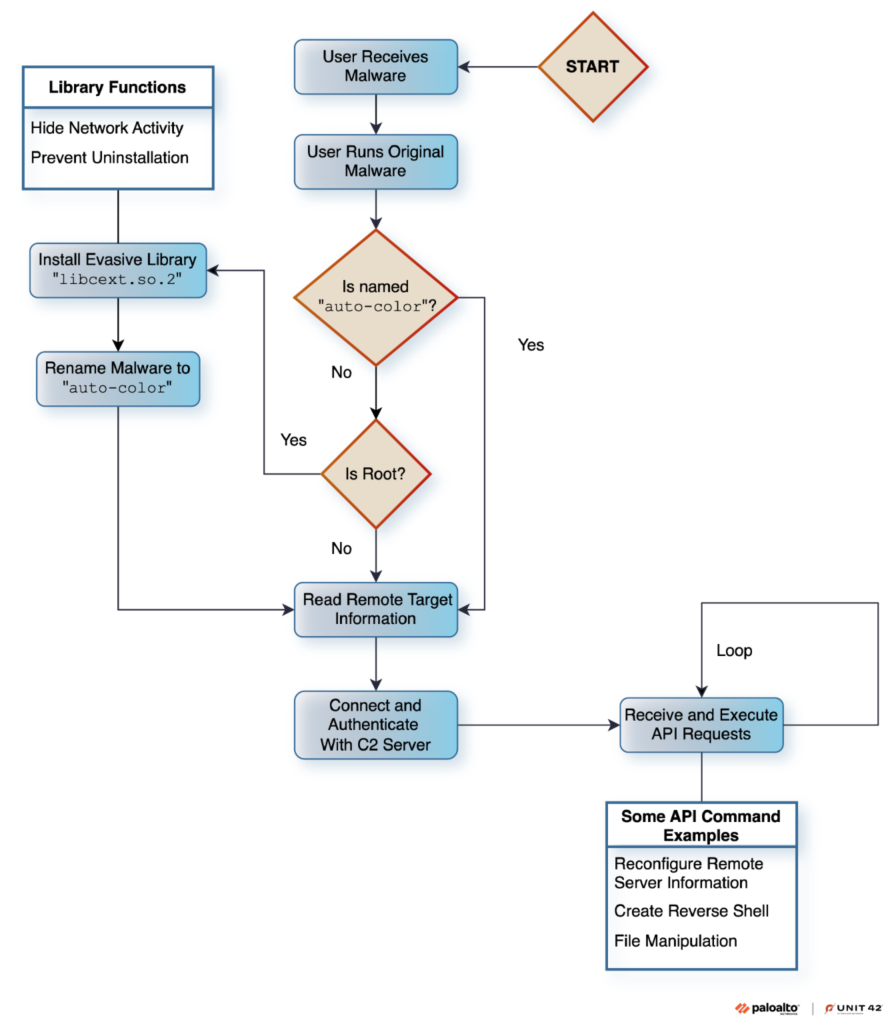
1.Auto-Color: An Emerging and Evasive Linux Backdoor by #PaloAlto’s #Unit42
- using benign-looking file names
- hiding remote C2 connections via advanced technique used by Symbiote malware family
- deploying proprietary encryption algorithms to hide communication & configuration info
https://unit42.paloaltonetworks.com/new-linux-backdoor-auto-color/
2.RustDoor and Koi Stealer for macOS Used by North Korea-Linked Threat Actor to Target the Cryptocurrency Sector by PaloAlto’s #Unit42
- characteristics of attackers are similar to various reports during 2024 of North Korean threat actors targeting other job seekers
- details of the activity of attackers within compromised environments
- technical analysis of newly discovered Koi Stealer macOS variant & depicts the different stages of the attack
https://unit42.paloaltonetworks.com/macos-malware-targets-crypto-sector/
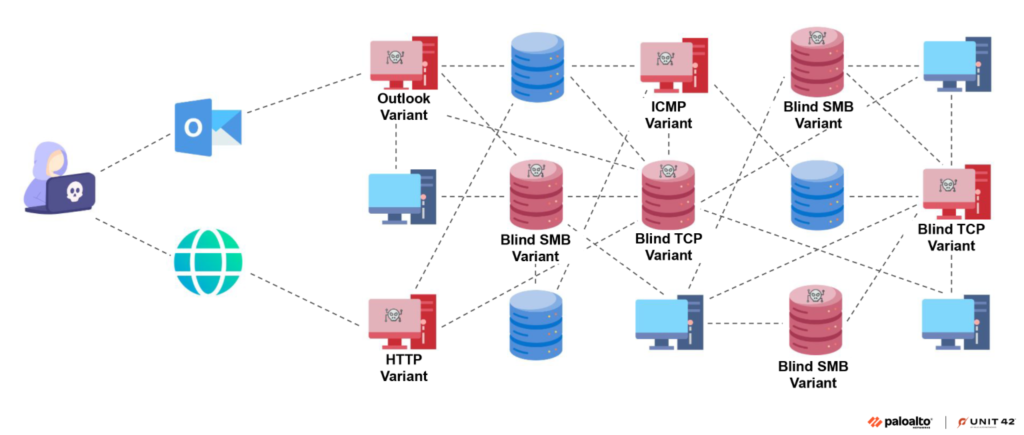
3.Squidoor: Suspected Chinese Threat Actor’s Backdoor Targets Global Organizations by #PaloAlto’s #Unit42
- advanced backdoor that supports multiple modules, designed for stealth
- features rarely seen set of capabilities, including using multiple protocols to communicate with the C2(Outlook API,DNS & ICMP tunneling)
https://unit42.paloaltonetworks.com/advanced-backdoor-squidoor/
4. JavaGhost’s Persistent Phishing Attacks From the Cloud by #PaloAlto’s #Unit42
- common methodologies that JavaGhost uses to create their phishing infra
- tactics employed within compromised cloud environments to establish long-term persistence
https://unit42.paloaltonetworks.com/javaghost-cloud-phishing/
5. DeepSeek Lure Using CAPTCHAs To Spread Malware by @Threatlabz
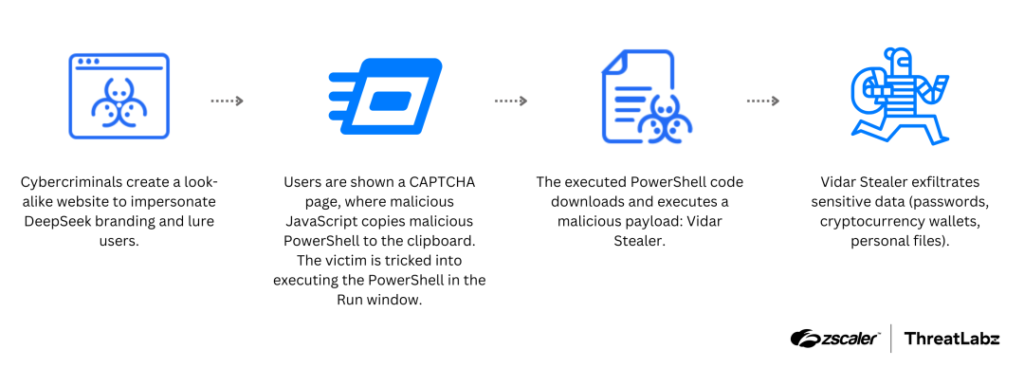
- cybercriminals are leveraging DeepSeek’s popularity by creating websites hosted on fake look-alike domains to deceive users and deliver Vidar info stealer
- campaign uses fake CAPTCHA page to conduct clipboard injection, secretly copying a malicious PowerShell command for users to execute
https://www.zscaler.com/blogs/security-research/deepseek-lure-using-captchas-spread-malware
6. Linux Detection Engineering – The Grand Finale on Linux Persistence by @elasticseclabs
- continue to dig deep into world of Linux persistence
- building on foundational concepts and techniques explored previously, discusses some more obscure, creative and/or complex backdoors & persistence mechanisms
https://www.elastic.co/security-labs/the-grand-finale-on-linux-persistence
7. Your MFA Is No Match for Sneaky2FA by @esthreat
- phishing operators making use of stolen session cookies behind VPN and proxy-associated hosting providers
- leading to follow-on activities like modification/creation of MFA methods for maintaining persistent access to stolen accounts
https://www.esentire.com/blog/your-mfa-is-no-match-for-sneaky2fa
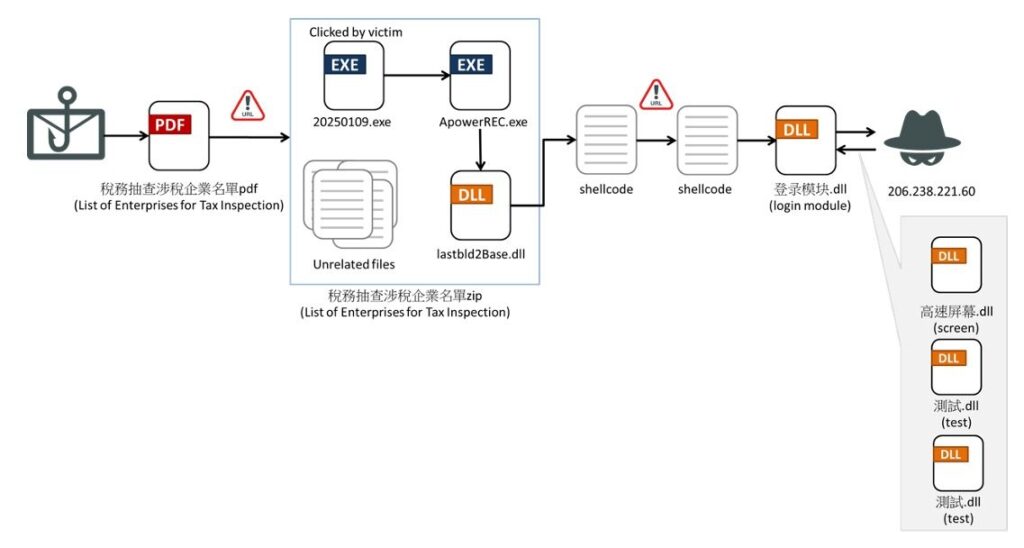
8. Winos 4.0 Spreads via Impersonation of Official Email to Target Users in Taiwan by #FORTIGUARD LABS
- In jan 2025 attack used Winos4.0, an advanced malware framework actively used in recent threat campaigns, to target companies in Taiwan
- usually, there is loader that is used to load malicious DLL & Winos4.0 module is extracted from shellcode downloaded from its C2
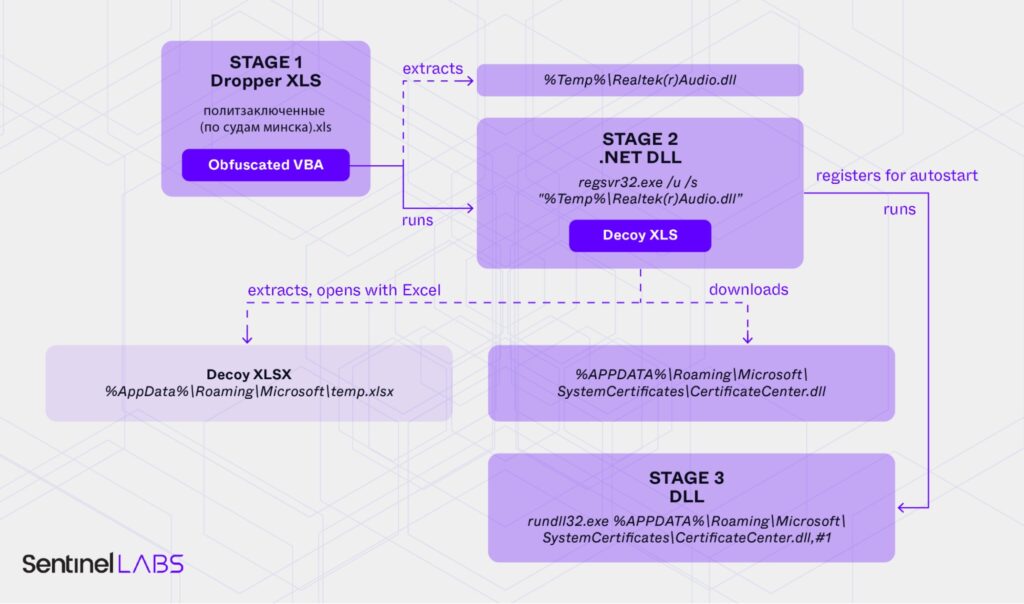
9. Ghostwriter | New Campaign Targets Ukrainian Government and Belarusian Opposition by @LabsSentinel
- recent malware samples & C2 infra activity indicate that operation remains active
- this cluster of threat activity is extension of long-running Ghostwriter campaign identified in previous public reporting
10. Your item has sold! Avoiding scams targeting online sellers by @TalosSecurity
- recent phishing campaigns targeting sellers on marketplaces have leveraged platforms’ direct messaging feature(s) to attempt to steal credit card details for sellers’ payout accounts
- shipment detail changes, pressure to conduct off-platform transactions, and attempted use of “friends and family” payment options are commonly encountered scam techniques, all of which seek to remove the seller protections usually afforded by platforms
https://blog.talosintelligence.com/online-marketplace-scams/
11. Lotus Blossom espionage group targets multiple industries with different versions of Sagerunex and hacking tools by @TalosSecurity
- based on examination of tactics, techniques, and procedures (TTPs) utilized in these campaigns, alongside deployment of Sagerunex, backdoor family used exclusively by Lotus Blossom was used
- using specific commands to install their Sagerunex backdoor within the system registry and configuring it to run as a service on infected endpoints
- also developed new variants of Sagerunex that not only use traditional C2 servers but also use legitimate, 3rd-party cloud services like Dropbox, Twitter & Zimbra (open-source webmail) as C2 tunnels
https://blog.talosintelligence.com/lotus-blossom-espionage-group
Thank you for reading.
Please add interesting items you came across during the week in the comments below.