Welcome to the weekly digest about the Cybersecurity & Threats in the wild.
Below you will find a very subjective summary of Cybersecurity events for the prior week.
1.Analyzing DEEP#DRIVE: North Korean Threat Actors Observed Exploiting Trusted Platforms for Targeted Attacks by @Securonix Threat Research
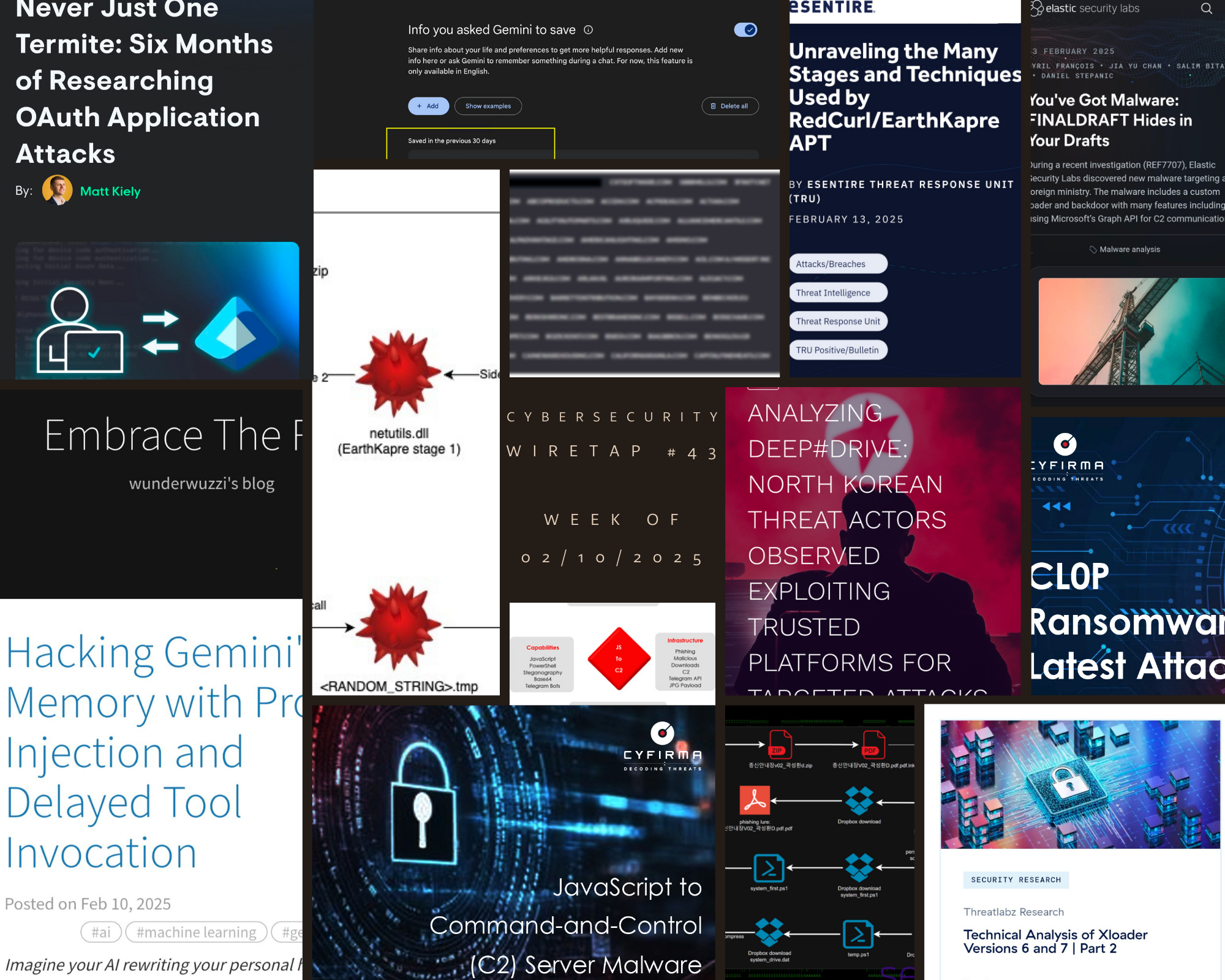
- attack chain began with .lnk file disguised as legitimate docs
- .lnk file created scheduled task named ChromeUpdateTaskMachine to execute malicious scripts periodically
- system_first.ps1 gathered detailed system info, exfiltrating data to Dropbox
- temp.ps1 downloaded, modified & decompressed Gzip-compressed .NET assembly (system_drive.dat)
- used Dropbox as hosting platform for payloads
2.CL0P Ransomware : Latest Attacks by @CyfirmaR
- Cl0p group recently targeted 43 orgs and exfiltrated sensitive info
- highlights & breakup of the target orgs, trends observed of Cl0p ransomware in last 6 quarters
https://www.cyfirma.com/research/cl0p-ransomware-latest-attacks/
3. JavaScript to Command-and-Control (C2) Server Malware by @CyfirmaR
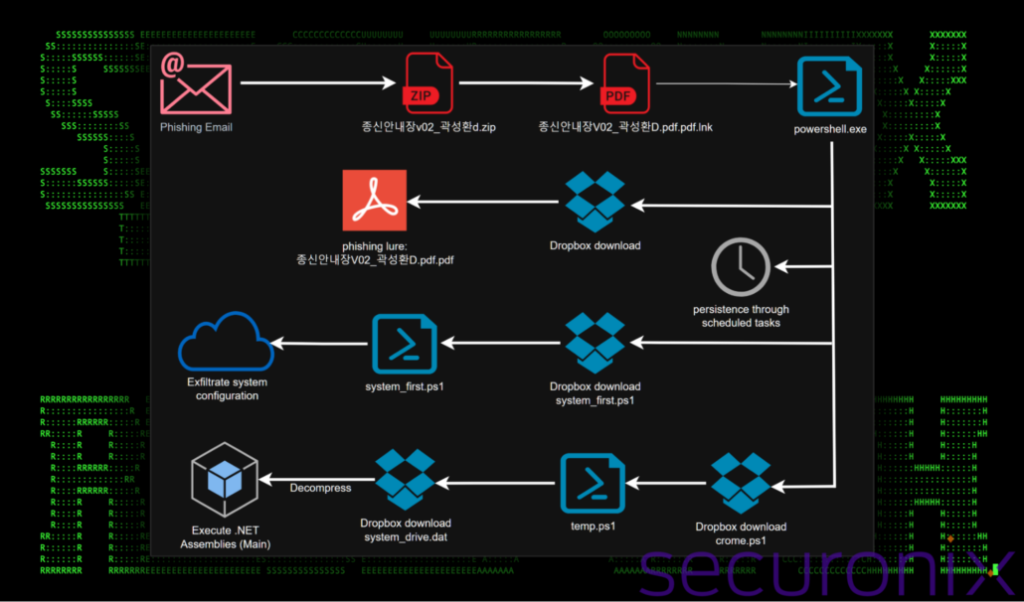
- sophisticated multi-stage malware attack that employs obfuscation, steganography & covert communication channels
- attack begins with obfuscated JavaScript file that fetches encoded strings from open-source service to execute PowerShell script
- script downloads JPG & text file both of which contain malicious MZ DOS executables embedded using steganographic
- once executed, these payloads deploy Stealer malware, designed to extract sensitive data
https://www.cyfirma.com/research/javascript-to-command-and-control-c2-server-malware/
4. Technical Analysis of Xloader Versions 6 and 7 | Part 2 by @Threatlabz
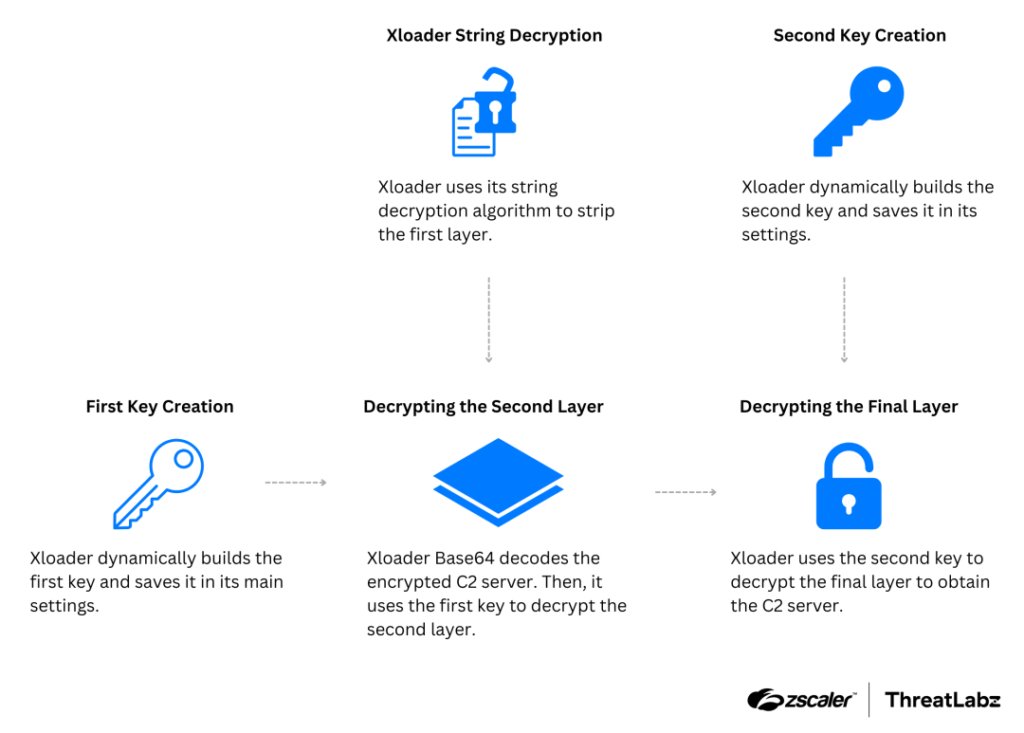
- Xloader v6 & v7 use advanced obfuscation techniques to mask critical parts of code & data
- malware continues to utilize hardcoded decoy lists to blend real C2 network communications in with traffic to legitimate websites
- decoy lists and real C2 server are encrypted using different keys and algorithms.Xloader versions 6 and 7 use the same network protocol and are protected by multiple layers of encryption
https://www.zscaler.com/blogs/security-research/technical-analysis-xloader-versions-6-and-7-part-2
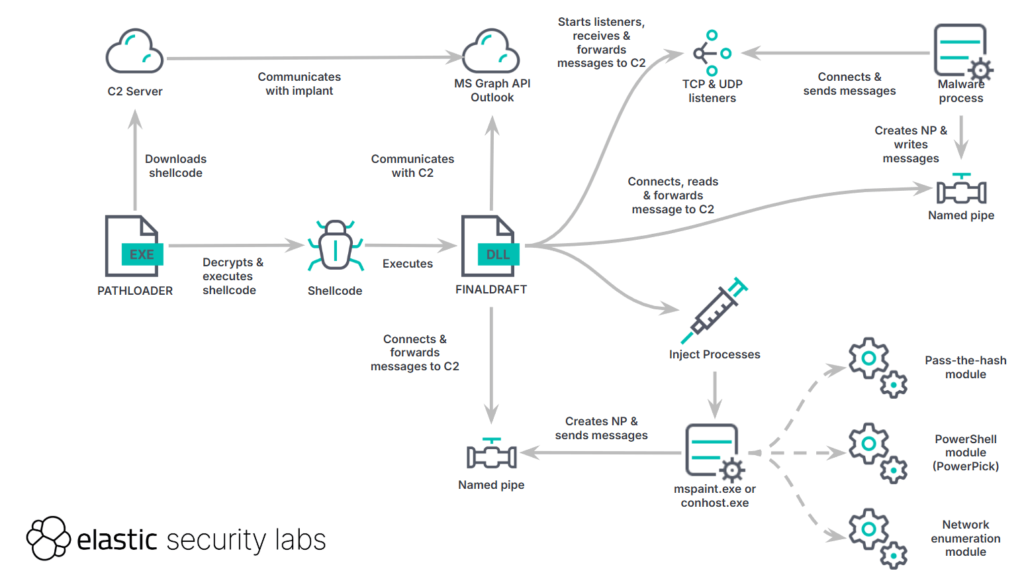
5. You’ve Got Malware: FINALDRAFT Hides in Your Drafts by @elasticseclabs
- new family of previously unknown malware that leverages Outlook as communication channel via Microsoft Graph API
- post-exploitation kit includes a loader, a backdoor, and multiple submodules that enable advanced post-exploitation activities
https://www.elastic.co/security-labs/finaldraft
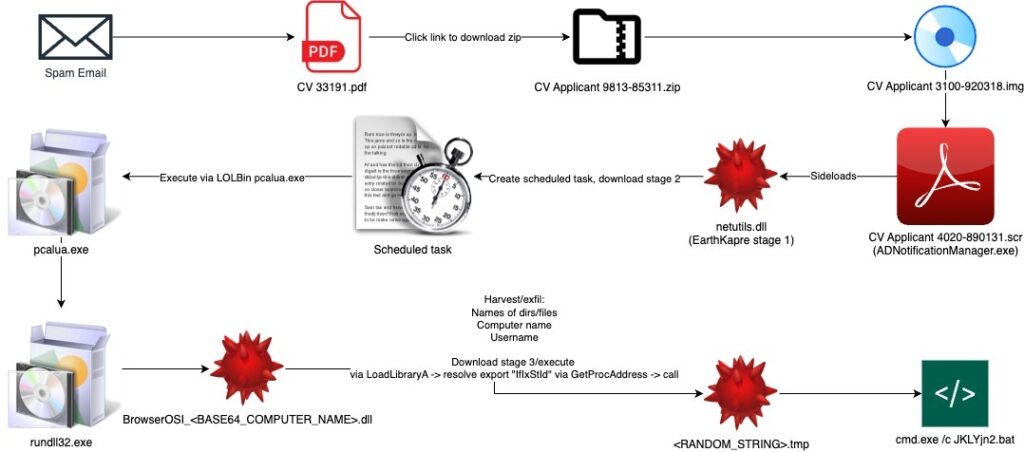
6. Unraveling the Many Stages and Techniques Used by RedCurl/EarthKapre APT by @esthreat
- use of legitimate Adobe executable (ADNotificationManager.exe) to sideload the EarthKapre/RedCurl loader
- EarthKapre (aka RedCurl) -h ighly sophisticated cyber espionage group known for its advanced operations, primarily targeting private-sector orgs
- target of this attack is org within Law Firms & Legal Services industry.
7. Termite: Six Months of Researching OAuth Application Attacks by @HuntressLabs
- If you administer at least one Microsoft 365 tenant, audit your OAuth applications right now. Statistically speaking, there’s a good chance your tenant is infected with a malicious app.
8. Hacking Gemini’s Memory with Prompt Injection and Delayed Tool Invocation by @wunderwuzzi23
- risk for long-term manipulation of user memories, even if infrequent, represents significant risk to be aware of
- likelihood of successful exploitation may increase over time as LLM context lengths grow, making it more challenging to detect hidden instructions within lengthy
https://embracethered.com/blog/posts/2025/gemini-memory-persistence-prompt-injection/
Thank you for reading.
Please add interesting items you came across during the week in the comments below.