Welcome to the weekly digest about the Cybersecurity & Threats in the wild. Below you will find a very subjective summary of Cybersecurity events for the prior week.
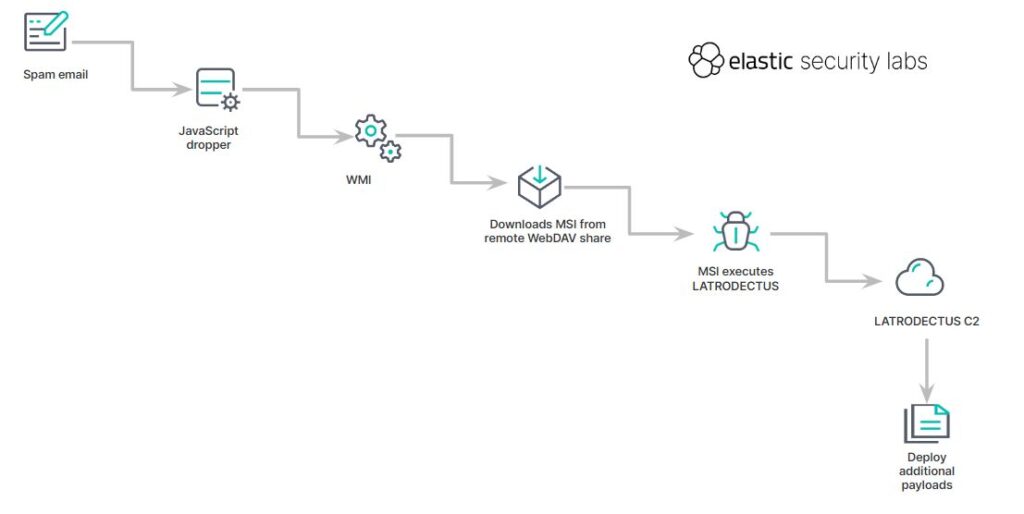
Spring Cleaning with LATRODECTUS: A Potential Replacement for ICEDID by @elasticseclabs
- new event handlers (process discovery, desktop file listing) since its inception and integration of a self-delete technique to delete running files
https://www.elastic.co/security-labs/spring-cleaning-with-latrodectus
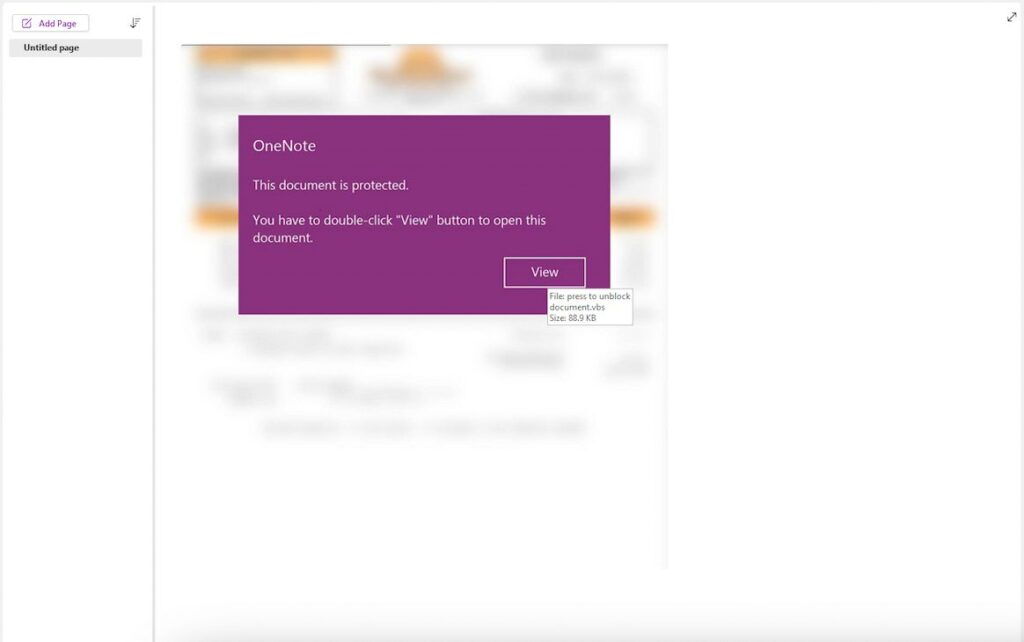
Payload Trends in Malicious OneNote Samples by #PaloAlto‘s #Unit42
- attackers have the freedom to embed either text-based malicious scripts or binary files inside OneNote. This offers them more flexibility compared to traditional macros in documents
https://unit42.paloaltonetworks.com/payloads-in-malicious-onenote-samples/
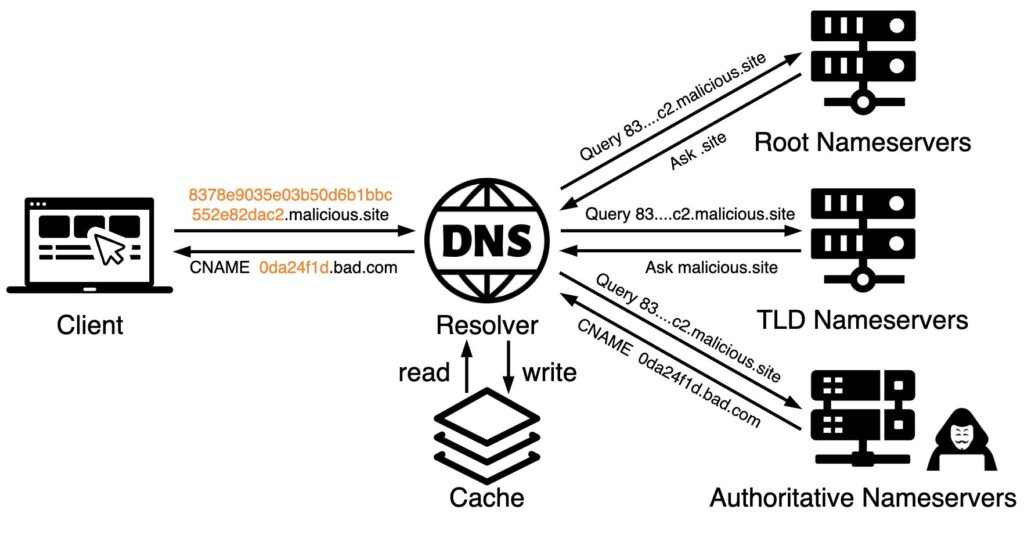
Leveraging DNS Tunneling for Tracking and Scanning by #PaloAlto‘s #Unit42
- scan a victim’s network infrastructure & gather info useful for future attacks
- use DNS tunneling techniques to track delivery of malicious emails & monitor use of CDN
https://unit42.paloaltonetworks.com/three-dns-tunneling-campaigns/
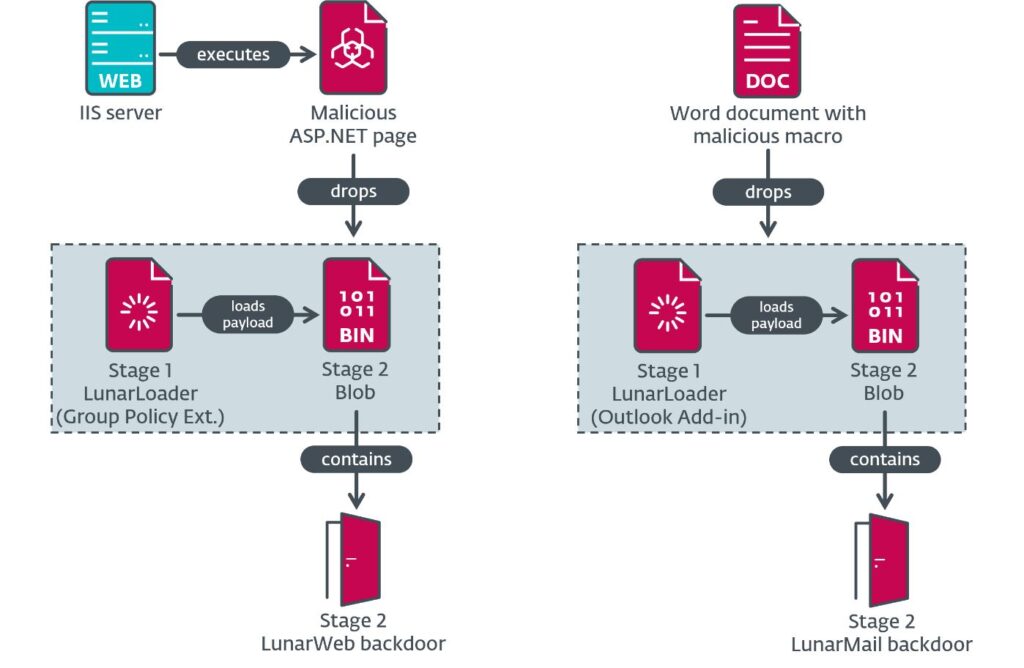
To the Moon and back(doors): Lunar landing in diplomatic missions by @ESETresearch
- previously unknown backdoors – LunarWeb & LunarMail – used in compromise of European MFA & its diplomatic missions
- Both employ steganography, hiding commands in images
https://www.welivesecurity.com/en/eset-research/moon-backdoors-lunar-landing-diplomatic-missions/
Ebury is alive but unseen: 400k Linux servers compromised for cryptocurrency theft and financial gain by @ESETresearch
- follow-up on how Ebury has evolved, and the new malware families its operators use to monetize their botnet of Linux servers.
Tracking the Progression of Earth Hundun’s Cyberespionage Campaign in 2024 by @TrendMicro
- targeting Asia-Pacific & employs updated tactics for infection spread and comm
- how operates, including stages of infection C&C interaction & malware behavior
https://www.trendmicro.com/en_us/research/24/e/earth-hundun-2.html
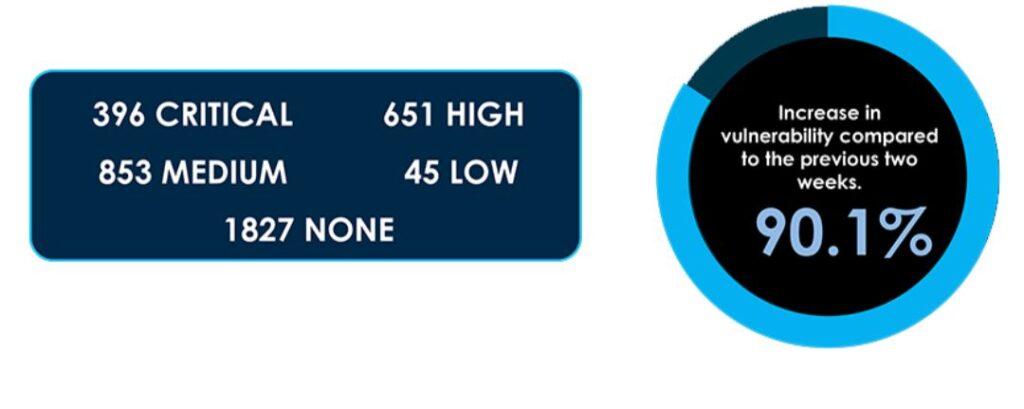
Fortnightly Vulnerability Summary by @CyfirmaR
- Most Impacted Product: Linux | FRRouting | RobotOS
- vulnerabilities: 3772
- exploits published: 91
- threat Actors: 8
- zero day: 28
https://www.cyfirma.com/research/fortnightly-vulnerability-summary-2/
Cyber Attacks on Egypt, UAE, and Saudi Arabia by @CyfirmaR
- pro-Palestine hacktivist groups targeted the Etisalat Egyptian unit in Mar
- month before, systems belonging to Etisalat UAE were encrypted by LockBit ransomware group
https://www.cyfirma.com/research/cyber-attacks-on-egypt-uae-and-saudi-arabia/

Thanks a lot for reading.