Welcome to the weekly digest about the Cybersecurity & Threats in the wild. Below you will find a very subjective summary of Cybersecurity events for the prior week.
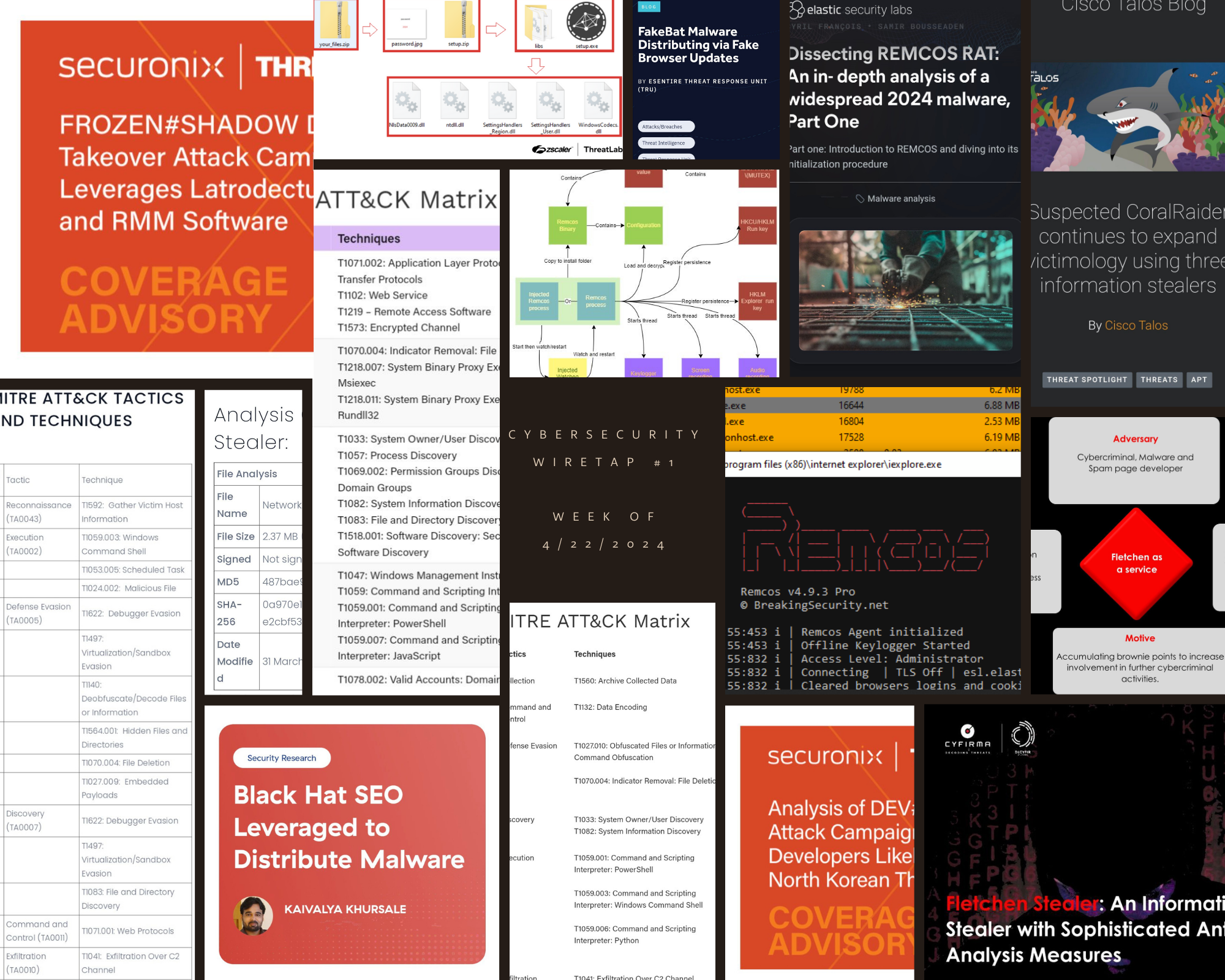
Analysis of Ongoing FROZEN#SHADOW Attack Campaign by @Securonix Threat #Research
- introduced via phishing emails & redirects to JavaScript that kicks off code exec chain downloading & executing further
- https://buff.ly/49Sx4Rr

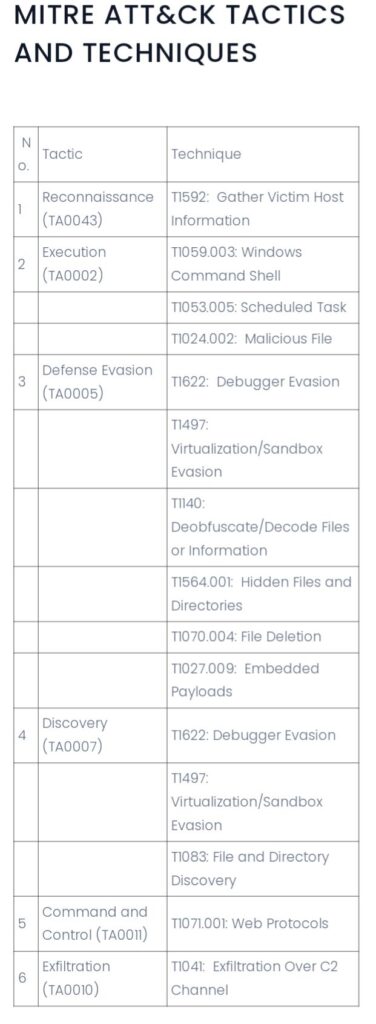
Analysis of DEV#POPPER by @Securonix Threat Research
- attackers set up fake job interviews for devs & asked to download and run soft from GitHub which contained malicious Node JS payload
- https://www.securonix.com/blog/analysis-of-devpopper-new-attack-campaign-targeting-software-developers-likely-associated-with-north-korean-threat-actors/

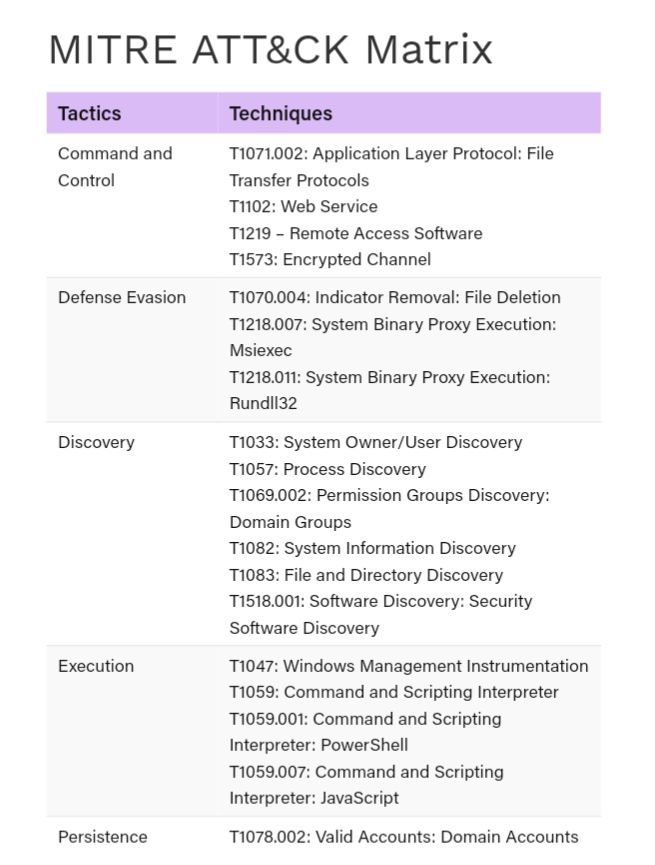
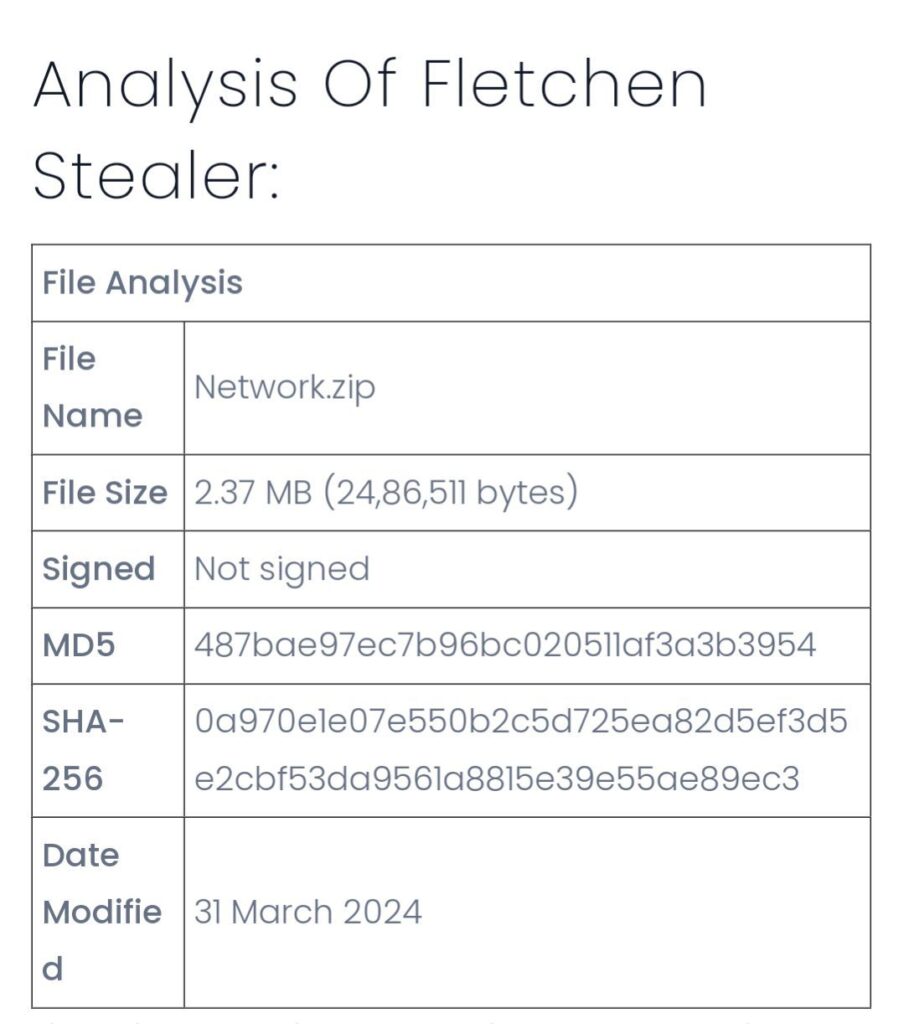
Fletchen Stealer: An Info Stealer with Sophisticated Anti-Analysis Measures by @CyfirmaR
- sophisticated info-stealing malware offered as stealer-as-a-service for free
- gains persistence using scheduled task and auto-run registry
- https://www.cyfirma.com/research/fletchen-stealer-an-information-stealer-with-sophisticated-anti-analysis-measures/


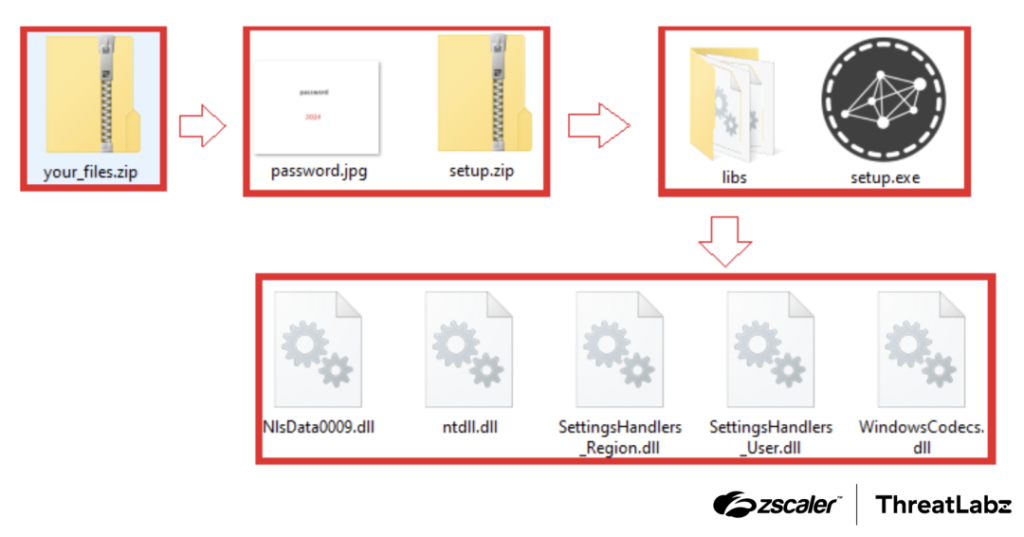
Black Hat SEO Leveraged to Distribute Malware by @Threatlabz
- payloads delivered via multi-level zipped files hidden within innocuous content
- once executed perform the activities & initiating comm with C2
- https://buff.ly/44ihHAx
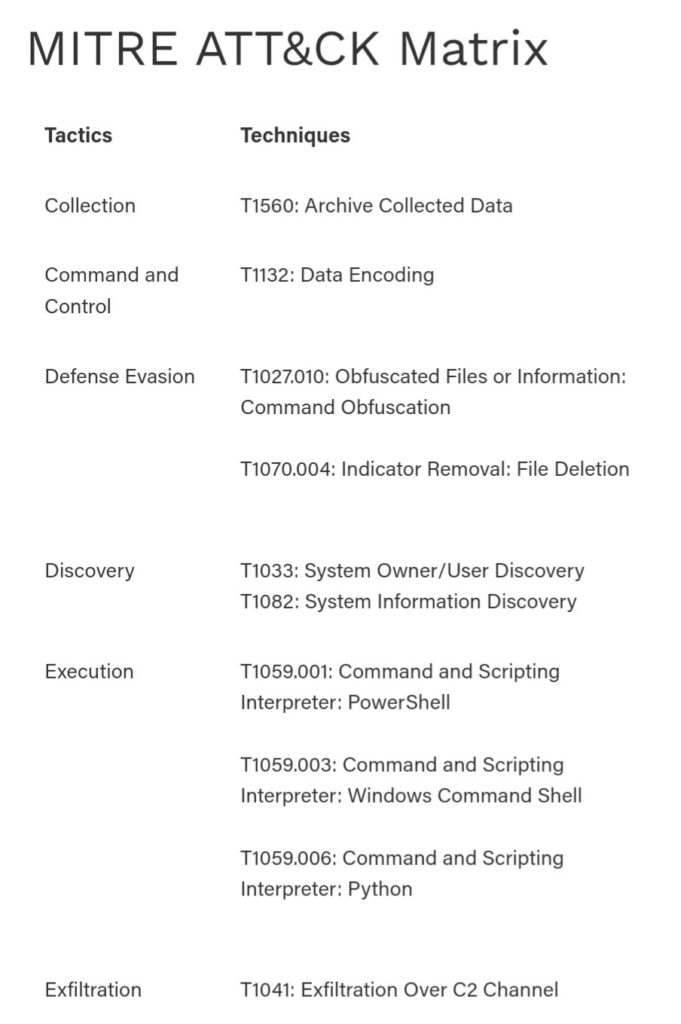
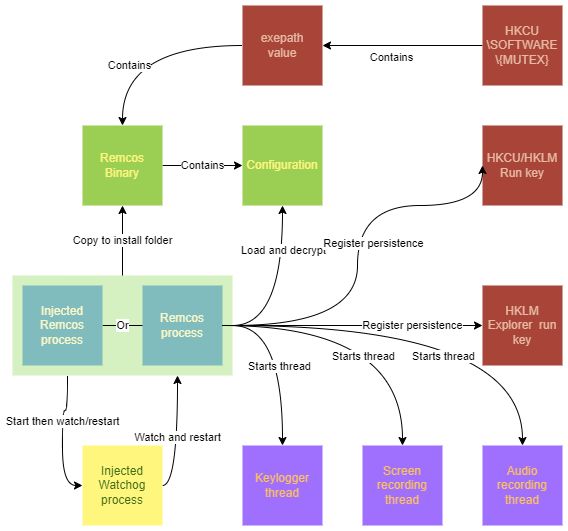
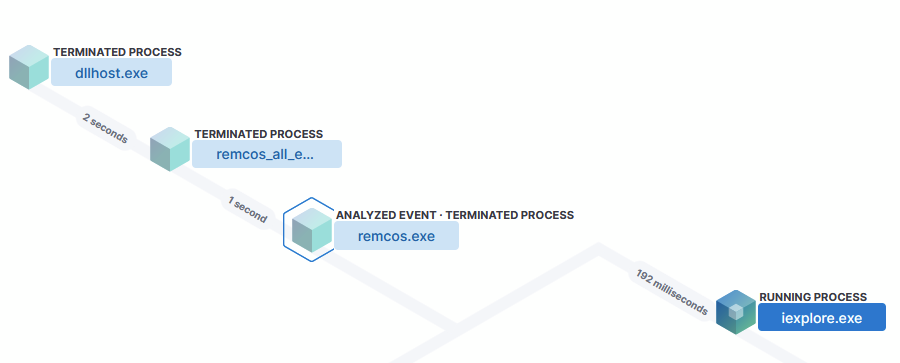
Dissecting REMCOS RAT: An in- depth analysis of a widespread 2024 malware P1 by @elasticseclabs
- wide range of functionality including evasion techniques, privilege escalation, process injection & recording
- https://buff.ly/44jiCRm
#FakeBat Malware Distributing via Fake Browser Updates by @esthreat
- loader being distributed via compromised websites that contain injected malicious JavaScript that triggers fake browser update notifications
- https://buff.ly/3UAA68z

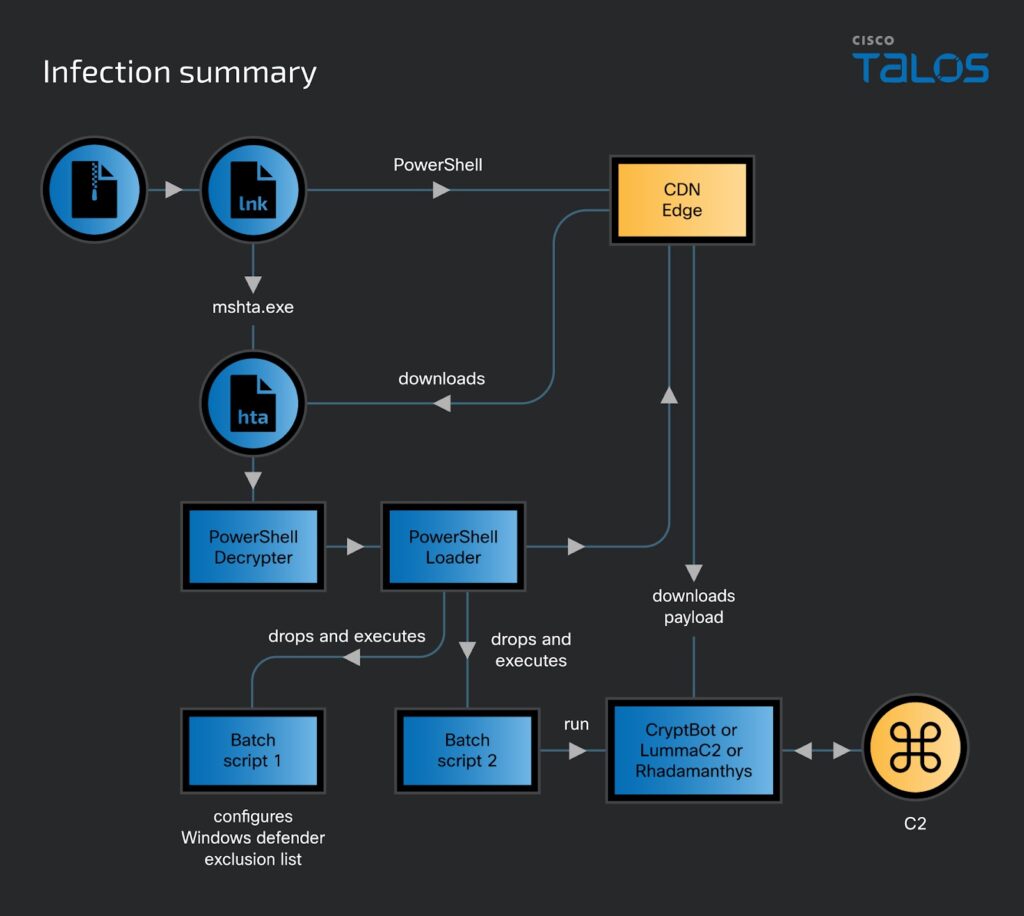
Suspected #CoralRaider continues to expand victimology using three information stealers by @TalosSecurity
- new PowerShell command-line arg embedded in LNK file to bypass anti-virus & download final payload
- https://blog.talosintelligence.com/suspected-coralraider-continues-to-expand-victimology-using-three-information-stealers/

Thanks a lot for reading.