Welcome to the weekly digest about the Cybersecurity & Threats in the wild.
Below you will find a very subjective summary of Cybersecurity events for the prior week.
1.Unmasking The Gentlemen Ransomware: Tactics, Techniques, and Procedures Revealed by @TrendMicro
- campaign leveraged combination of legitimate driver abuse, Group Policy manipulation, custom anti-AV utilities, privileged account compromise & encrypted exfiltration channels
- group targeted multiple industries and regions, focusing heavily on range of industries such as manufacturing, construction, healthcare, and insurance, with attacks spanning at least 17 countries
https://www.trendmicro.com/en_us/research/25/i/unmasking-the-gentlemen-ransomware.html
2. EvilAI Operators Use AI-Generated Code and Fake Apps for Far-Reaching Attacks by @TrendMicro
- disguises itself as productivity or AI-enhanced tools, with professional-looking interfaces & valid digital signatures that make it difficult for users and security tools to distinguish it from legitimate soft
- EvilAI infections have appeared globally, with the highest impact in Europe, the Americas, and the AMEA region
- malware campaign has predominantly impacted organizations in manufacturing, government/public services, and healthcare
https://www.trendmicro.com/en_us/research/25/i/evilai.html
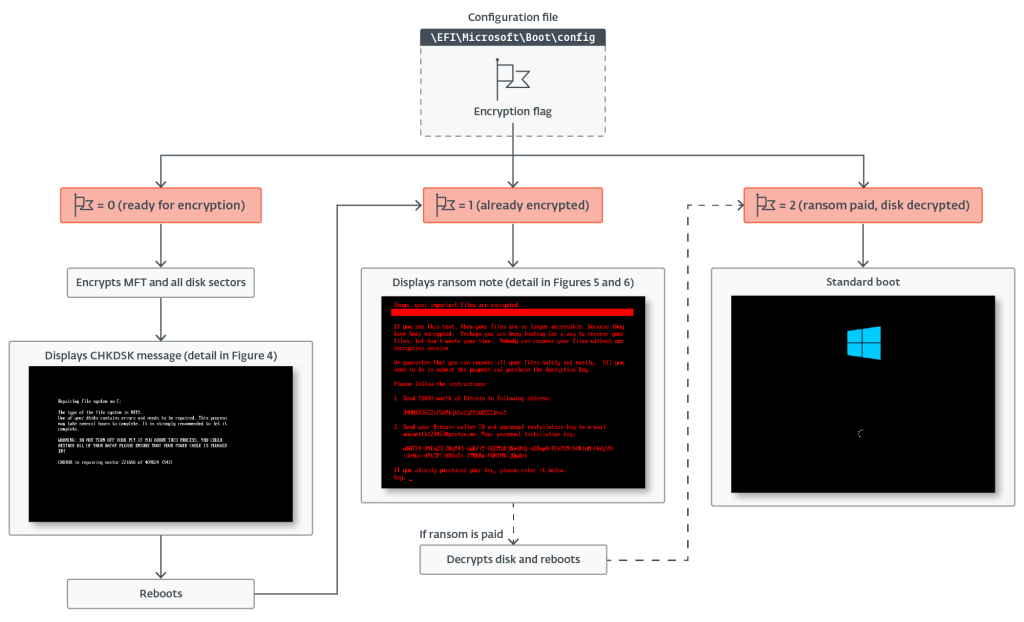
3. Introducing HybridPetya: Petya/NotPetya copycat with UEFI Secure Boot bypass by @ESETresearch
- HybridPetya encrypts Master File Table, which contains important metadata about all files on NTFS-formatted partitions
- Unlike original Petya/NotPetya, HybridPetya can compromise modern UEFI-based systems by installing malicious EFI application onto EFI System Partition
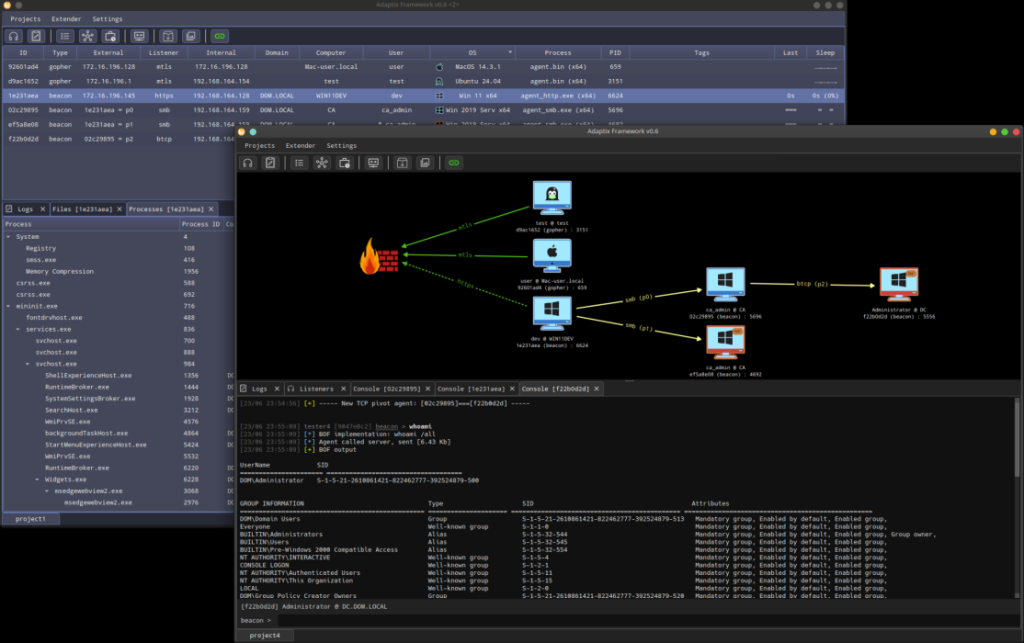
4. AdaptixC2: A New Open-Source Framework Leveraged in Real-World Attacks by #PaloAlto’s #Unit42
- open-source post-exploitation & adversarial emulation framework made for pentesters that threat actors are using in campaigns
- unlike many well-known C2 frameworks, AdaptixC2 has remained largely under radar
- there is limited public documentation available demonstrating its use in real-world
https://unit42.paloaltonetworks.com/adaptixc2-post-exploitation-framework/
5. Trusted Connections, Hidden Risks: Token Management in the Third-Party Supply Chain by #PaloAlto’s #Unit42
- high-severity alert – single, unfamiliar OAuth token is making hundreds of connections from 3 different IP addresses, 2 belong to unknown VPN servicr
- token belongs to 3rd-party app integrated with company’s Salesforce instance (one of those forgotten dormant integrations)
- threat actor has stolen OAuth token to bypass traditional defenses & is enumerating CRM accounts & exfiltrating sensitive data …
https://unit42.paloaltonetworks.com/third-party-supply-chain-token-management

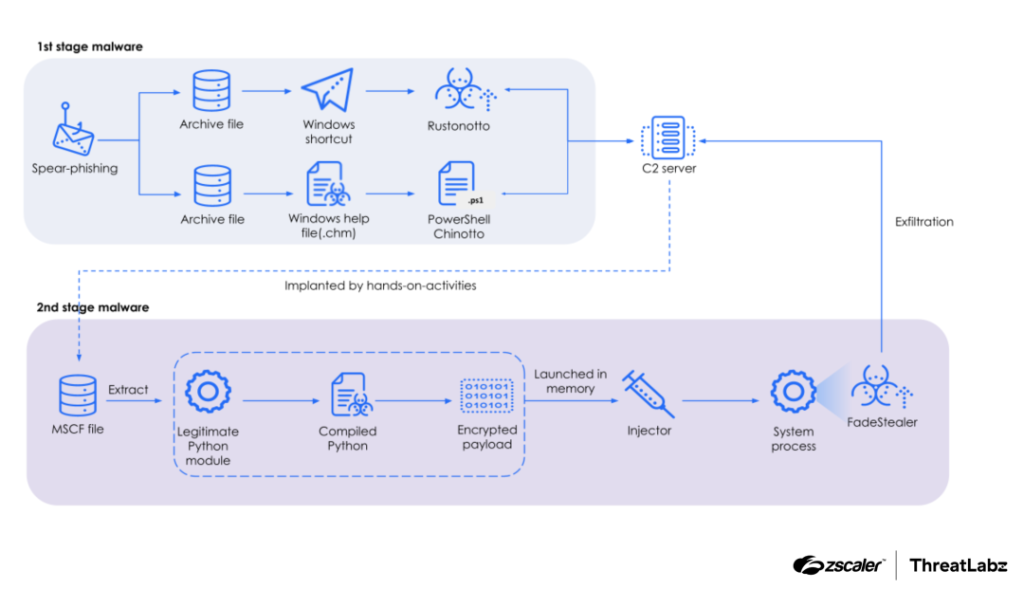
6.APT37 Targets Windows with Rust Backdoor and Python Loader by @Threatlabz
- in recent campaigns, APT37 utilizes single C2 server to orchestrate all components of their malware arsenal, including Rust-based backdoor named Rustonotto, PowerShell-based Chinotto malware & FadeStealer.
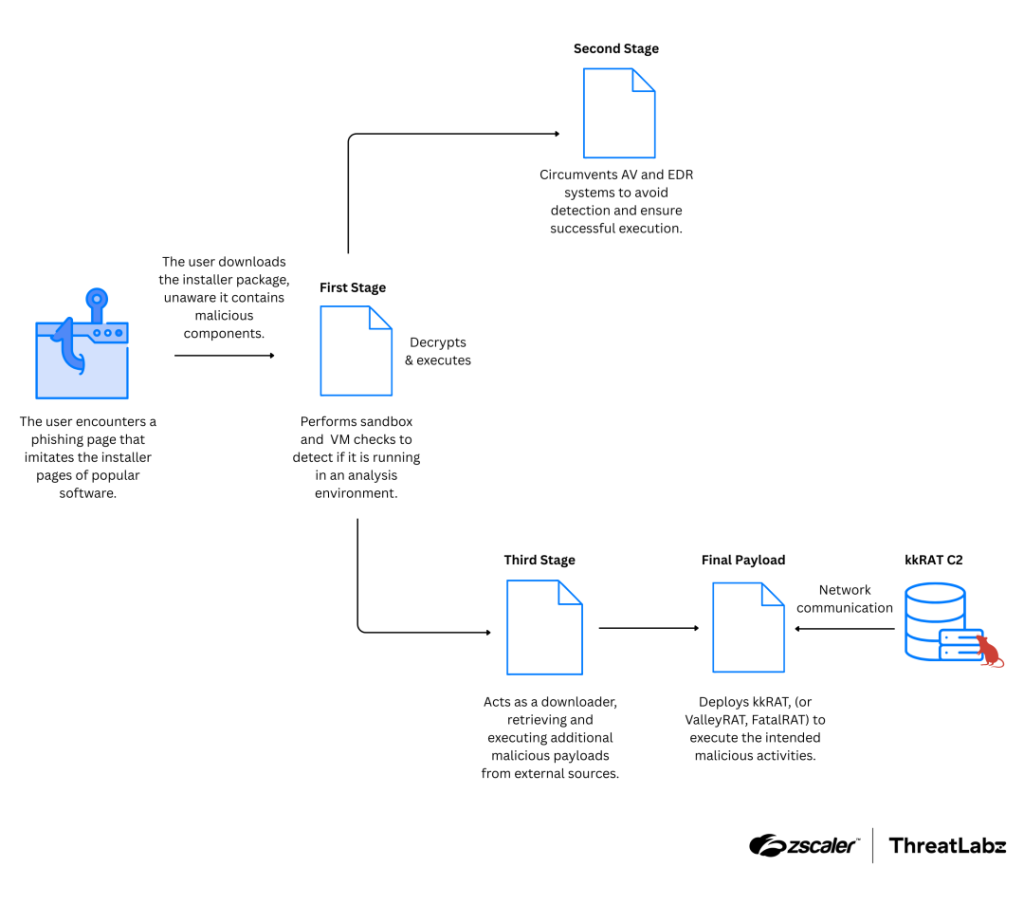
7. Technical Analysis of kkRAT by @Threatlabz
- campaign uses fake installer pages mimicking popular soft to deliver 3 different RATs as the final payload in various instances
- kkRAT employs network comm protocol similar to Ghost RAT, with added encryption layer after data compression
- RAT’s features include clipboard manipulation to replace cryptocurrency addresses & the deployment of remote monitoring tools
https://www.zscaler.com/blogs/security-research/technical-analysis-kkrat
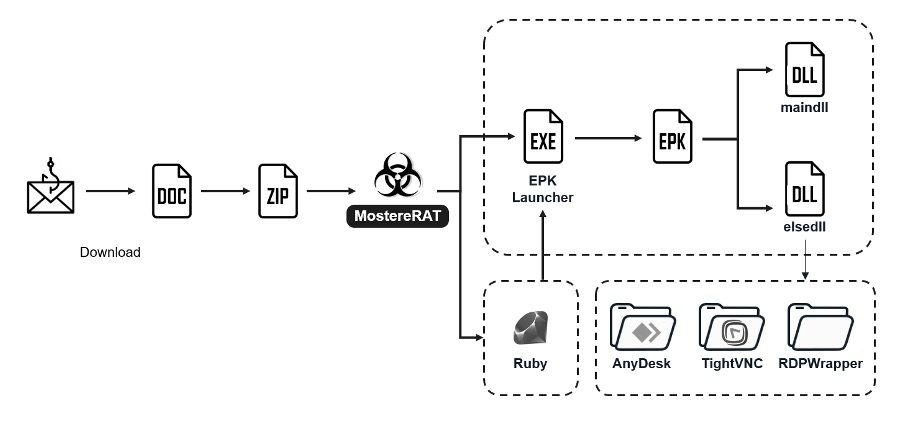
8.MostereRAT Deployed AnyDesk/TightVNC for Covert Full Access by #FORTIGUARD LABS
- phishing campaign that include use of an Easy Programming Language (EPL) to develop staged payload, concealing malicious ops & disabling security tools to prevent alert triggers, securing C2 comms using mutual TLS supporting various methods for deploying additional payloads, installing popular RATs to grant attackers complete control over compromised system
9.SEO Poisoning Attack Targets Chinese-Speaking Users with Fake Software Sites by #FORTIGUARD LABS
- campaign aimed at Chinese-speaking users
- attackers manipulated search rankings with SEO plugins & registered lookalike domains that closely mimicked legitimate software sites
- by using convincing language & small character substitutions, they tricked victims into visiting spoofed pages & downloading malware
Thanks a lot for reading.
Please add interesting items you came across during the week in the comments below.