Welcome to the weekly digest about the Cybersecurity & Threats in the wild.
Below you will find a very subjective summary of Cybersecurity events for the prior week.
1.Unmasked: Salat Stealer – A Deep Dive into Its Advanced Persistence Mechanisms and C2 Infrastructure by @CyfirmaR
- sophisticated Go-based infostealer targeting Windows systems
- malware exfiltrates browser creds, cryptocurrency wallet data, and session information while employing advanced evasion techniques, including UPX packing, process masquerading, registry run keys, and scheduled tasks
- operated under a Malware-as-a-Service (MaaS) model by Russian-speaking actors, it leverages resilient C2 infrastructure.
2.GhostRedirector poisons Windows servers: Backdoors with a side of Potatoes by @ESETresearch
- at least 65 Windows servers compromised in Jun 2025
- victims are mainly located in Brazil, Thailand, and Vietnam
- GhostRedirector has developed a new C++ backdoor, Rungan, capable of executing commands on the victim’s server
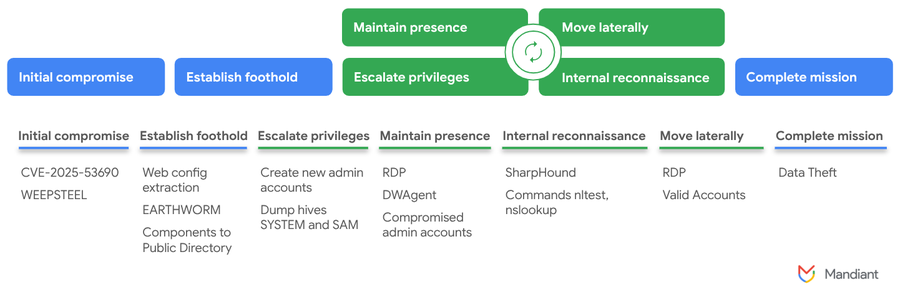
3.ViewState Deserialization Zero-Day Vulnerability in Sitecore Products (CVE-2025-53690) by @Mandiant
- initial compromise was achieved by exploiting the ViewState Deserialization vuln CVE-2025-53690 on affected internet-facing Sitecore instance, resulting in RCE
- decrypted ViewState payload contained WEEPSTEEL, malware designed for internal recon
- leveraging this access, threat actor archived root directory of web app, indicating intent to obtain sensitive files such as web.config
4. Threat Brief: Salesloft Drift Integration Used To Compromise Salesforce Instances by #PaloAlto’s #Unit42
- threat actor performed mass exfil of sensitive data from various Salesforce objects, including Account, Contact, Case and Opportunity records
- following exfil actor appeared to be actively scanning acquired data for creds, likely with intent to facilitate further attacks or expand their access
- threat actor deleted queries to hide evidence of jobs they run, likely as anti-forensics technique
https://unit42.paloaltonetworks.com/threat-brief-compromised-salesforce-instances/
5. Model Namespace Reuse: An AI Supply-Chain Attack Exploiting Model Name Trust by #PaloAlto’s #Unit42
- fundamental flaw in AI supply chain that allows attackers to gain RCE and additional capabilities on major platforms like Microsoft’s Azure AI Foundry, Google’s Vertex AI and thousands of open-source projects
- Model Namespace Reuse occurs when cloud provider model catalogs or code retrieve deleted or transferred model by name
- by re-registering abandoned namespace & recreating its original path, malicious actors can target pipelines that deploy models based solely on their name
https://unit42.paloaltonetworks.com/model-namespace-reuse/
6.Ethereum smart contracts used to push malicious code on npm by @ReversingLabs
- 2 new pieces of open source malware discovered on npm package repository by ReversingLabs researchers in July employ novel and creative technique for loading malware on compromised devices: smart contracts for the Ethereum blockchain
https://www.reversinglabs.com/blog/ethereum-contracts-malicious-code
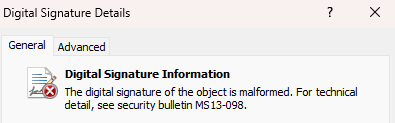
7. Investigating a Mysteriously Malformed Authenticode Signature by @elasticseclabs
- Elastic Security Labs recently encountered signature validation issue with one of our Windows binaries
- executable was signed using signtool.exe as part of our standard continuous integration (CI) process, but on this occasion, the output file failed signature validation
https://www.elastic.co/security-labs/malformed-authenticode-signature
8. New Botnet Emerges from the Shadows: NightshadeC2 by @esthreat
- identified new botnet, tracked as “NightshadeC2,” which is being deployed via loader that employs simple yet highly effective technique to bypass malware analysis sandboxes & exclude final payload in Windows Defender using technique we refer to here-in as “UAC Prompt Bombing”
https://www.esentire.com/blog/new-botnet-emerges-from-the-shadows-nightshadec2
Thanks a lot for reading.
Please add interesting items you came across during the week in the comments below.