Welcome to the weekly digest about the Cybersecurity & Threats in the wild.
Below you will find a very subjective summary of Cybersecurity events for the prior week.
1.GhostSpy Web-Based Android RAT : Advanced Persistent RAT with Stealthy Remote Control and Uninstall Resistance by @CyfirmaR
- infection begins with dropper that silently escalates privileges by exploiting Accessibility Services and UI automation to sideload & install secondary APK (update.apk)
- malware automatically grants itself all required permissions, simulating user interactions to bypass permission dialogs – eliminating the need for human interaction
- main payload provides comprehensive control over the device, enabling keylogging, screen capture, background audio and video recording, SMS and call log theft, GPS location tracking & remote command execution
2.WHILE TRUMP DISRUPTS THE WORLD ORDER, CHINA PREPARES FOR WAR OVER TAIWAN by @CyfirmaR
- With Donald Trump’s erratic style and his many isolationist tendencies, none of America’s allies can be 100% sure where they stand.
- Unlike Ukraine—which, despite America’s wavering, still maintains the support of European nations—Taiwan cannot rely on similar level of backing from its Asian neighbors
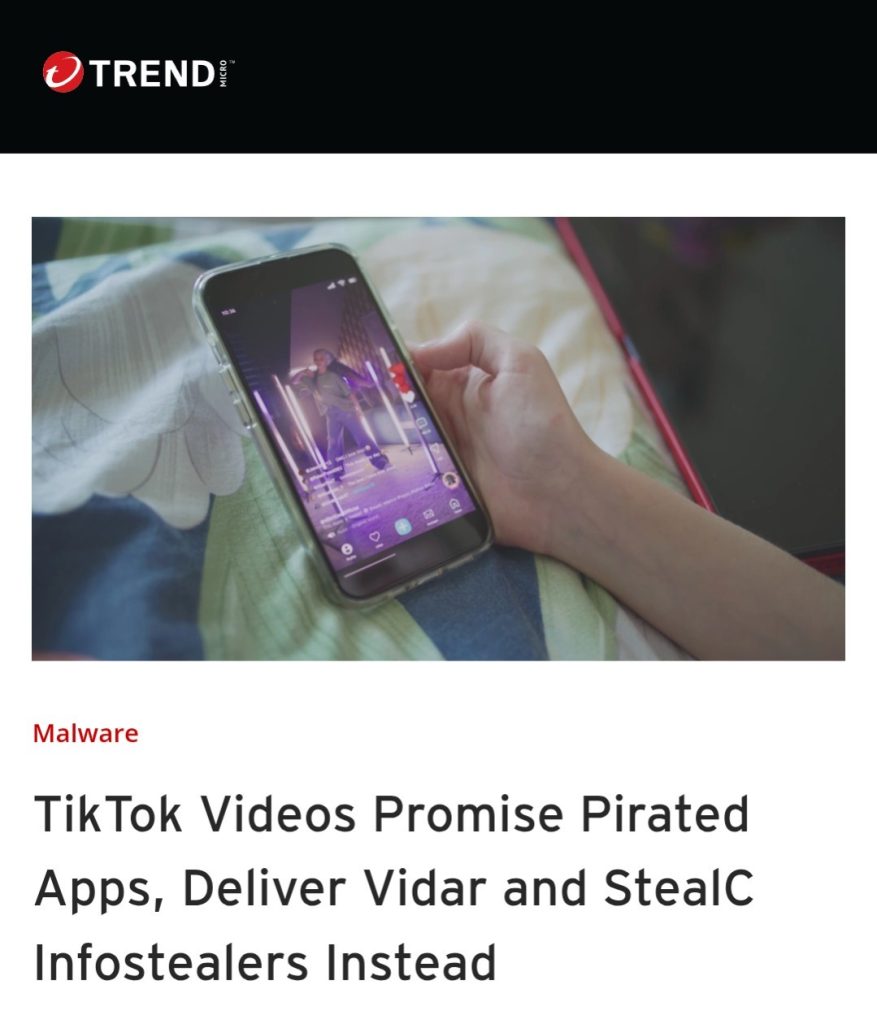
3.TikTok Videos Promise Pirated Apps, Deliver Vidar and StealC Infostealers Instead by @TrendMicro
- new social engineering campaign using TikTok to deliver the Vidar & StealC info stealers
- attack uses videos (possibly AI-generated) to instruct users to execute PowerShell commands, which are disguised as software activation steps
https://www.trendmicro.com/en_us/research/25/e/tiktok-videos-infostealers.html
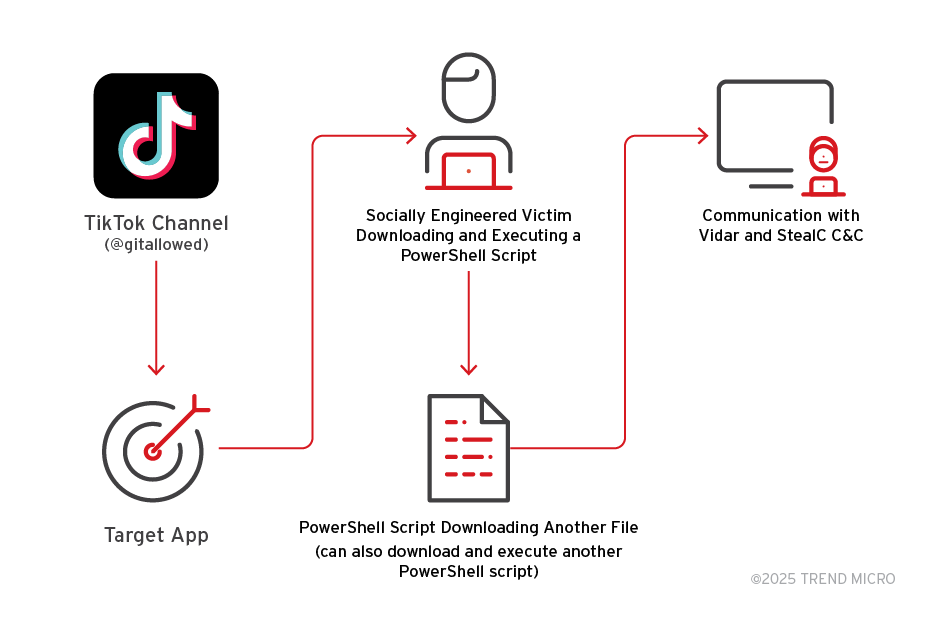
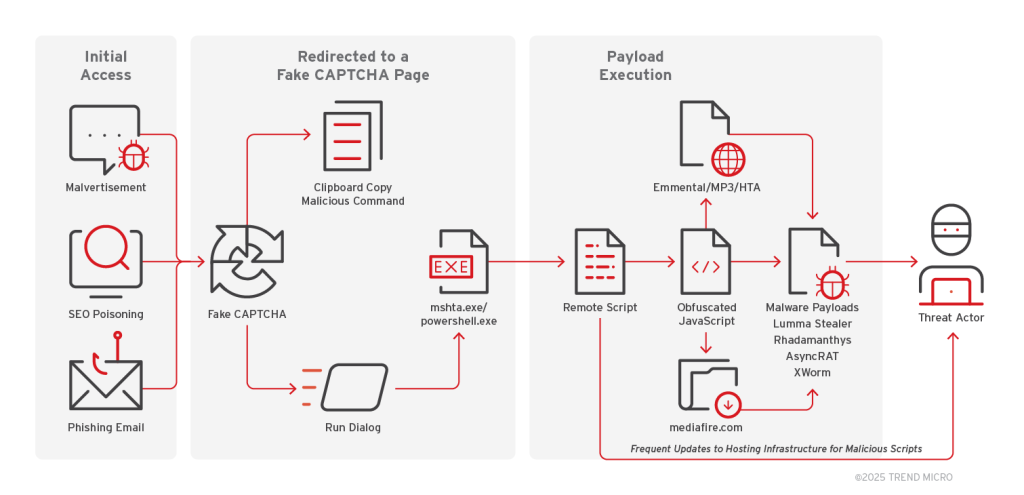
4. Fake CAPTCHA Attacks Deploy Infostealers and RATs in a Multistage Payload Chain by @TrendMicro
- wave of fake CAPTCHA pages that trick users into pasting malicious commands into Windows Run dialog
- campaigns feature use files (e.g., MP3, PDF) embedded with obfuscated JavaScript, delivered via phishing emails, malvertising, or SEO poisoning
- payloads are executed in-memory using mshta.exe or PowerShell
https://www.trendmicro.com/en_us/research/25/e/unmasking-fake-captcha-cases.html
5. Danabot: Analyzing a fallen empire by @ESETresearch
- primarily developed as infostealer & banking trojan
- has been used to distribute additional malware, including ransomware
- authors promote their toolset via underground forums & offer rental options to potential affiliates
https://www.welivesecurity.com/en/eset-research/danabot-analyzing-fallen-empire/
6.Malicious attack method on hosted ML models now targets PyPI by @ReversingLabs
- researchers detected 3 newly uploaded malicious packages that pose as “Python SDK for interacting with Aliyun AI Labs services.”
- attack that targets users of Alibaba AI labs
- After installation, malicious package delivers infostealer payload hidden inside a PyTorch model loaded from initialization script
- malicious payload exfiltrates basic info about the infected machine and content of.gitconfig file
https://www.reversinglabs.com/blog/malicious-attack-method-on-hosted-ml-models-now-targets-pypi
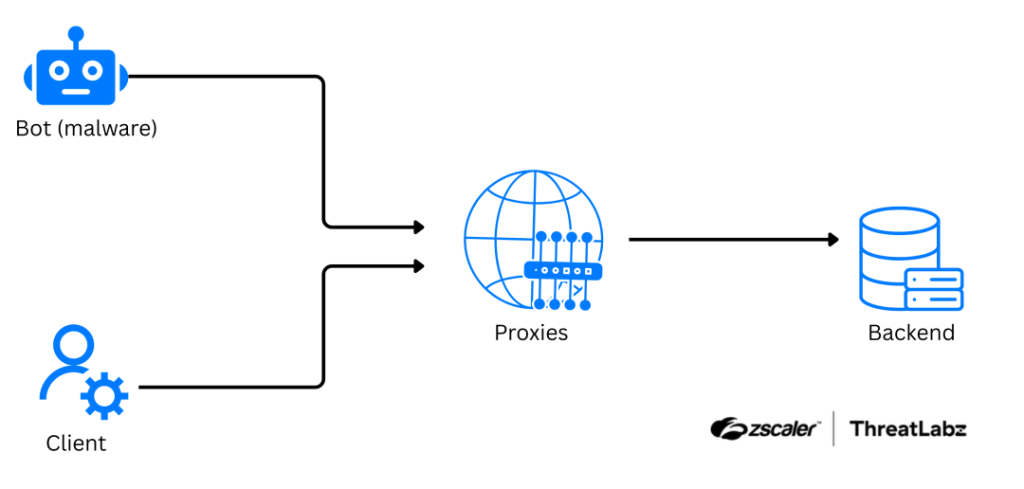
7. Operation Endgame 2.0: DanaBusted by @Threatlabz
- powerful modular malware family that is written in Delphi with ability to monitor keystrokes, capture screenshots, record video of victim’s desktop, exfiltrate files, inject arbitrary content into web browser, and deploy 2nd-stage malware payloads.
https://www.zscaler.com/blogs/security-research/operation-endgame-2-0-danabusted
8. De- obfuscating ALCATRAZ by @elasticseclabs
- open-source obfuscator ALCATRAZ has been seen within new malware deployed alongside RHADAMANTHYS infections
- Obfuscation techniques such as control flow flattening continue to serve as road blocks for analysts
https://www.elastic.co/security-labs/deobfuscating-alcatraz
9. Duping Cloud Functions: An emerging serverless attack vector by @TalosSecurity
- based on Tenable’s research, Cisco Talos conducted series of offensive tests within Cisco’s Google Cloud Platform (GCP) to identify additional threats that may affect customer environments
- by implementing different malicious console commands into Node Package Manager (NPM) ‘package.json’ file used in this technique, threat actors could execute environment enum
https://blog.talosintelligence.com/duping-cloud-functions-an-emerging-serverless-attack-vector/
10. Scarcity signals: Are rare activities red flags? by @TalosSecurity
- key findings reveal that odds of rare domain being malicious were 3.18 times higher than for frequently contacted domains (95% CI: 0.39–25.9), suggesting trend towards higher risk in rare domains
- non-rare domain ‘githubusercontent.com’ was flagged as malicious due to activity from its subdomain ‘raw.githubusercontent.com’
- subdomains should be considered when looking for malicious network traffic, especially for cloud services where service itself is legitimate, but content hosted on it is not guaranteed to be
https://blog.talosintelligence.com/scarcity-signals-are-rare-activities-red-flags/
11. Traitorware Court: The Case For SigParser by @HuntressLabs
- details of anonymized Huntress incident report concerning identity that displayed extremely high confidence IoCs
- use of a particular Microsoft 365 OAuth application called “SigParser.”
- post explores facts of intrusion and hypothesizes as to why threat actor would install this app during an attack
https://www.huntress.com/blog/traitorware-court-the-case-for-sigparser
12.Authentication Bypass to RCE in Versa Concerto (0-Day) by @pdiscoveryio
- discovery of multiple critical security flaws in Versa Concerto’s deployment
- multiple vulnerabilities discovered in Versa Concerto, a Spring Boot-based app deployed via Docker containers and routed through Traefik.
https://projectdiscovery.io/blog/versa-concerto-authentication-bypass-rce
13. AI ClickFix: Hijacking Computer-Use Agents Using ClickFix by @wunderwuzzi23
- traditional TTPs can be modified to specifically and effectively target Computer-Use Agents
- built 1st AI ClickFix proof-of-concept that shows agentic AI systems, powered by state of the art models, like claude-3-7-sonnet-20250219. (recorded the demo before Claude 4 came out)
- these attacks work because state of the art AI systems are susceptible to prompt injection and may follow GUI-based instructions from untrusted content
https://embracethered.com/blog/posts/2025/ai-clickfix-ttp-claude/
Thanks a lot for reading.
Please add interesting items you came across during the week in the comments below.