Welcome to the weekly digest about the Cybersecurity & Threats in the wild. Below you will find a very subjective summary of Cybersecurity events for the prior week.
Threat Actors Actively Exploiting CVE-2024-3273 : Underground Forums Share IP Addresses of Vulnerable D-Link NAS Devices by @CyfirmaR
- devices utilized for data backup purposes, are vulnerable, with notable impacts observed in UK, RU, DE, IT, US, FR
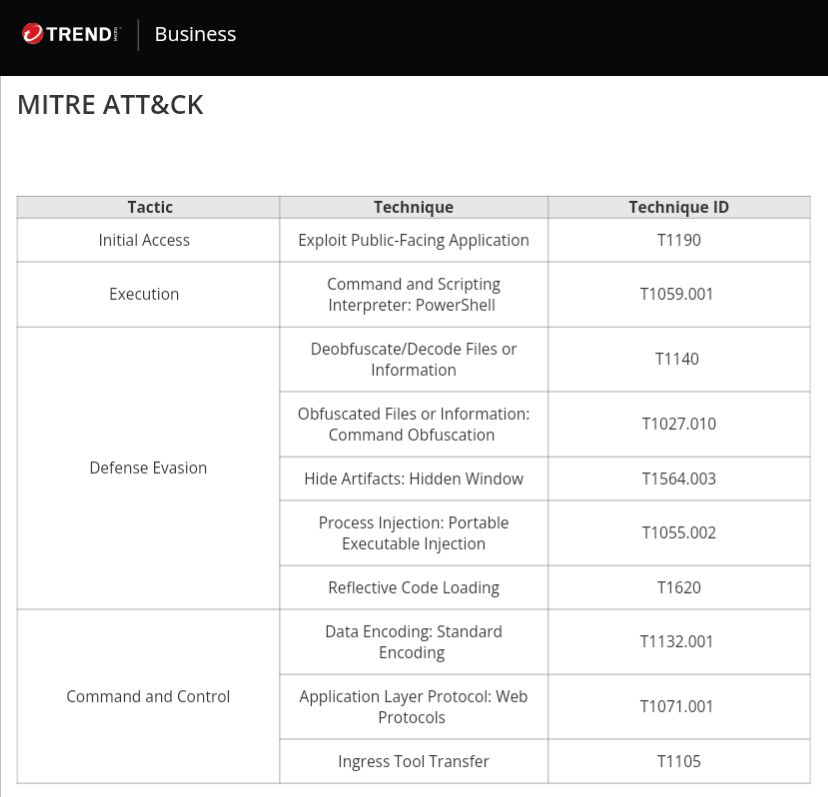
Decoding Water Sigbin’s Latest Obfuscation Tricks by @TrendMicro
- exploited CVE-2017-3506 & CVE-2023-21839 to deploy cryptocurrency miner via PowerShell script
- employed hexadecimal encoding of URLs & HTTP over 443, allowing for stealthy payload delivery
https://www.trendmicro.com/en_us/research/24/e/decoding-8220-latest-obfuscation-tricks.html
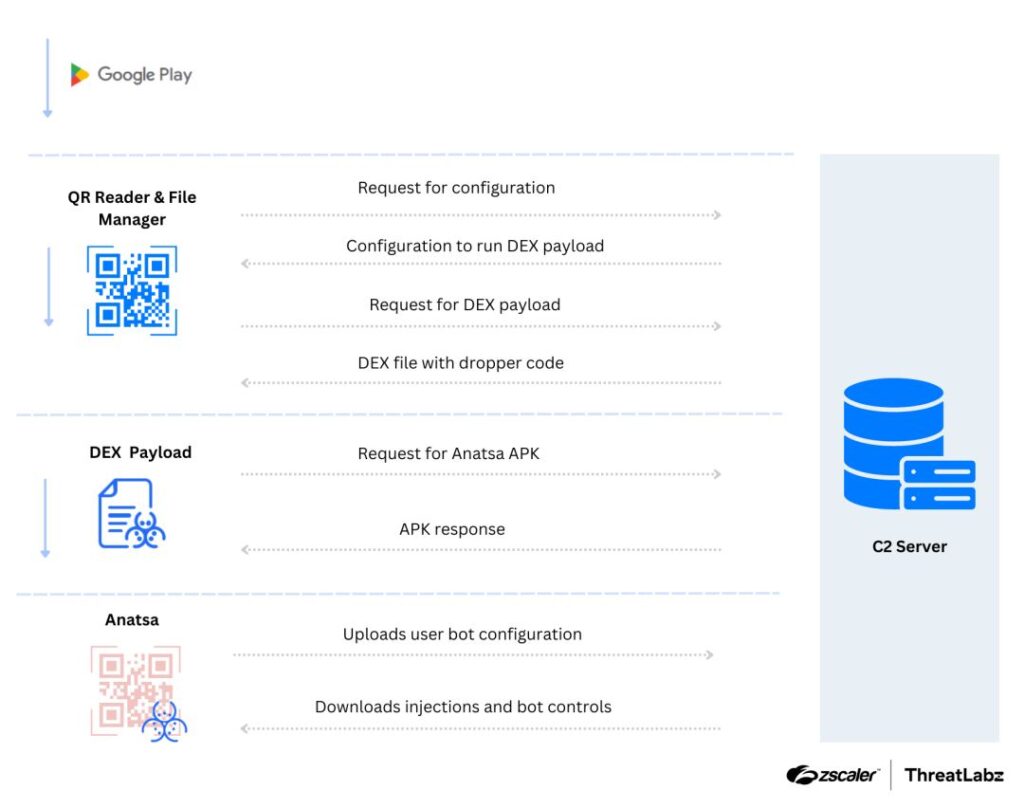
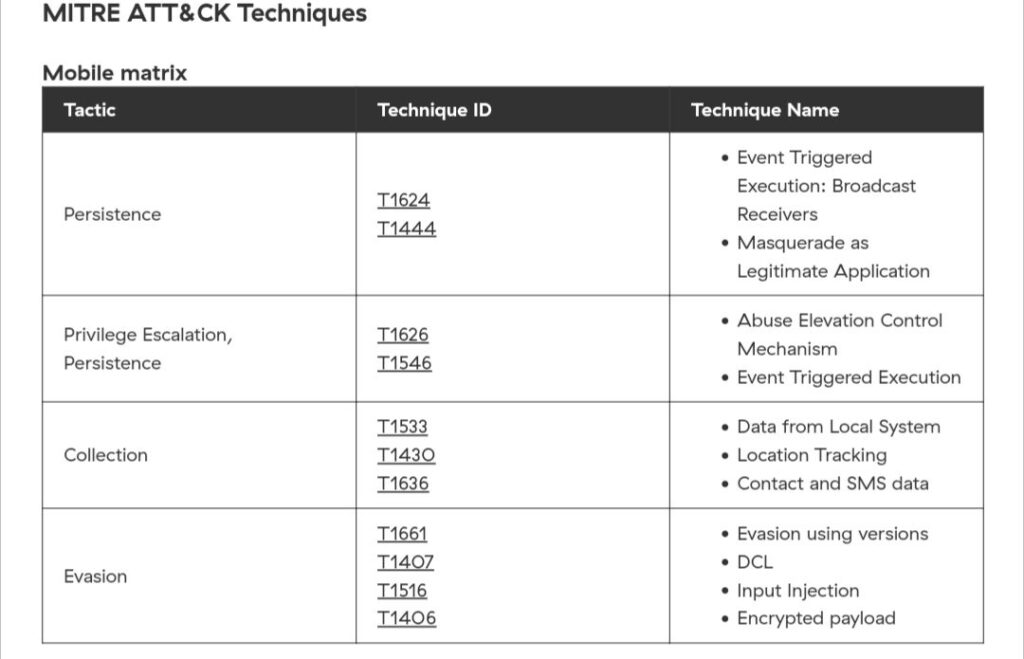
Technical Analysis of Anatsa Campaigns: An Android Banking Malware Active in the Google Play Store by @Threatlabz
- leveraging decoy applications such as PDF readers and QR code readers that act as loaders to deploy the Anatsa
Operation Endgame: Up In Smoke by @Threatlabz
- Smoke is a malware downloader that originated in 2011 that is designed to deliver second stage malware payloads that include information stealers and ransomware
https://www.zscaler.com/blogs/security-research/operation-endgame-smoke
Fake Browser Updates delivering BitRAT and Lumma Stealer by @esthreat
- infection chain began when user visited infected page containing injected malicious JavaScript
- Upon loading the page,code redirects the user to fake update page
https://www.esentire.com/blog/fake-browser-updates-delivering-bitrat-and-lumma-stealer
Attackers are impersonating a road toll payment processor across the U.S. in phishing attacks by @TalosSecurity
- they’re looking to collect users’ credit card information after they go in to pay the alleged overdue toll
https://blog.talosintelligence.com/threat-source-newsletter-may-30-2024/
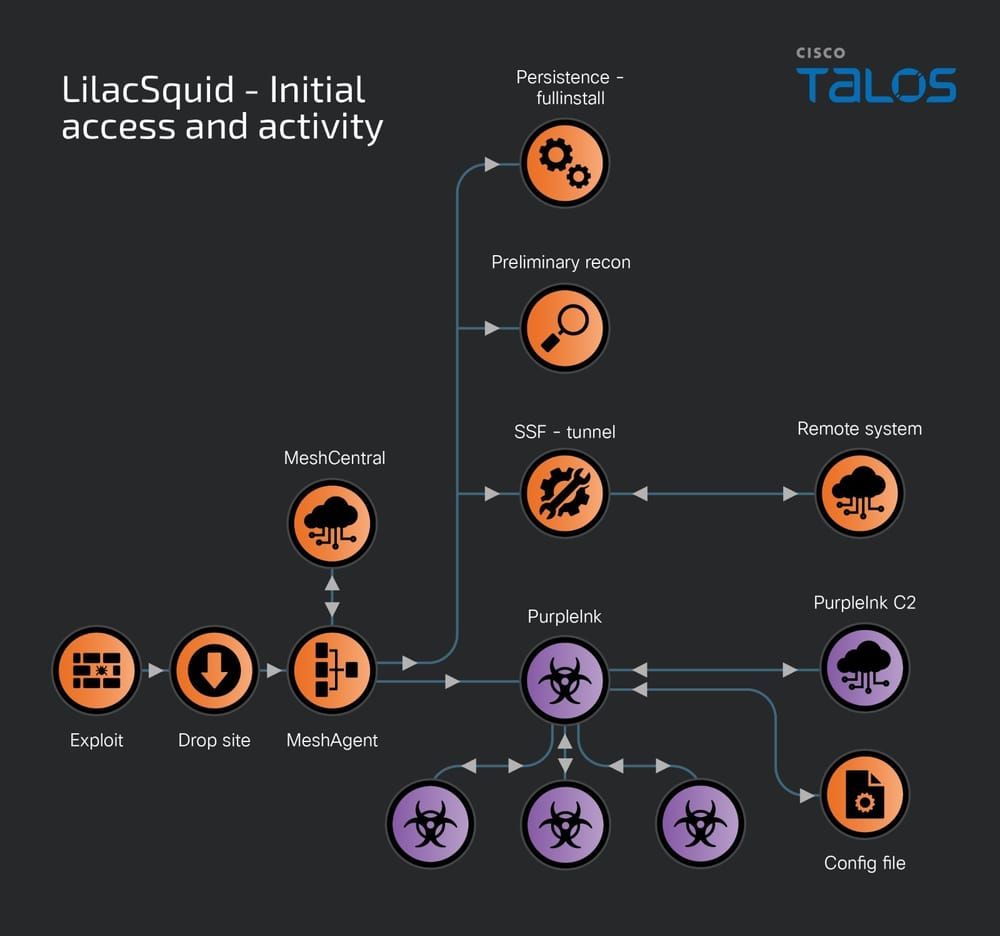
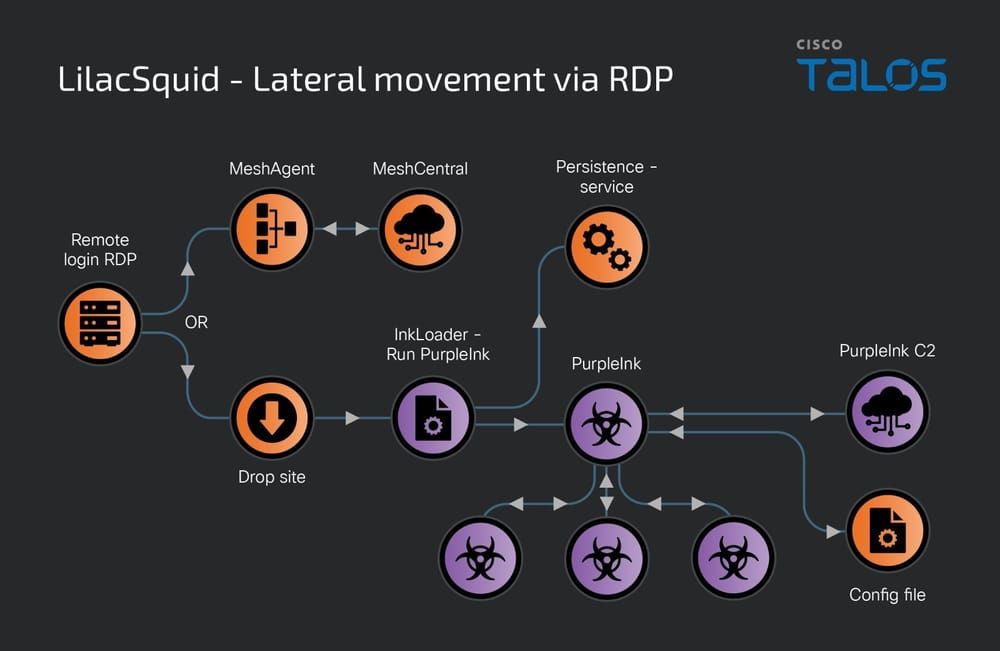
LilacSquid: The stealthy trilogy of PurpleInk, InkBox and InkLoader by @TalosSecurity
- campaign uses MeshAgent, an open-source remote management tool, and a customized version of QuasarRAT we’re calling “PurpleInk” to serve as the primary implants
https://blog.talosintelligence.com/lilacsquid/

Thanks a lot for reading.